Recently, Congressman Maxwell Alejandro Frost and Congressman Don Beyer introduced new legislation called "The Spacecraft Cybersecurity Act" that will require NASA to secure a cybersecurity protection plan from manufacturers applying to use federal dollars to build NASA spacecrafts. This legislation is a response to "thousands of cyberattacks from malicious actors, including state-sponsored threats from China and Russia, [that] have been launched against NASA, threatening the safety of Americans, including astronauts."
"As we enter a new era of cyber threats, establishing a reasonable timeline for NASA to incorporate cybersecurity measures into their acquisition process is more important than ever. The Spacecraft Cybersecurity Act would safeguard NASA's space missions and continue to advance our country's leadership in space exploration that contributes to our economy, security, and understanding of space." -Congressman Frost
This Act requires NASA to finalize a plan within 270 days of the law’s enactment to revise its spacecraft acquisition standards to incorporate important cybersecurity requirements. Recognizing the technical complexities of this task, the bill allows NASA’s experts time to develop this plan.
NASA's recent actions are not occurring in isolation. They're part of a broader trend of increased scrutiny on software supply chains, particularly in government and critical infrastructure sectors. As governments worldwide deal with increasing cyber threats, they're turning their attention to the backbone of modern software - open source. This shift is creating both challenges and opportunities for the open source community.
The Cyber Resilience Act (CRA)
While NASA's actions have brought immediate attention to the issue of software supply chain security, the European Union's proposed Cyber Resilience Act (CRA) represents a more comprehensive and far-reaching shift in the regulatory landscape. The CRA, first proposed in September 2022, aims to establish "common cybersecurity standards for products with digital elements across the EU."
Key Points of the CRA:
- Scope: The CRA applies to all products with "digital elements," which includes software and potentially impacts a high number of open source projects.
- Requirements: Manufacturers would need to implement security measures, conduct risk assessments, and provide ongoing support and updates for their products.
- Reporting Obligations: The Act mandates reporting of actively exploited vulnerabilities and incidents to EU authorities within 24 hours.
- Penalties: Non-compliance could result in fines of up to €15 million or 2.5% of "global annual turnover."
Why the CRA Matters for Open Source:
- Global Impact: Although an EU regulation, the CRA's effects will be felt globally because of the interconnected nature of software supply chains.
- SBOM (Software Bill of Material) Adoption: SBOMs may become more of a standard practice due to the CRA's requirements.
- Open Source Implications: Initially, the open source community raised concerns about the CRA's potential to create a "chilling effect" on open source development. However, recent amendments have introduced the concept of an "open source steward" and provided some exceptions for open source software.
- Preparation Time: With the CRA expected to come into effect within the next two years, the open source community has a limited window to prepare and adapt.
The CRA and SBOMs
The CRA doesn't explicitly mandate the use of SBOMs, but its requirements for security measures and transparency align closely with SBOM principles.
An SBOM, or Software Bill of Materials, is a detailed list of the software components and dependencies that make up a software application. It’s like an inventory or a “recipe” that outlines the different parts that have been used to create the software. SBOMs are useful for understanding the software supply chain, tracking vulnerabilities, and ensuring compliance with regulations like the CRA.
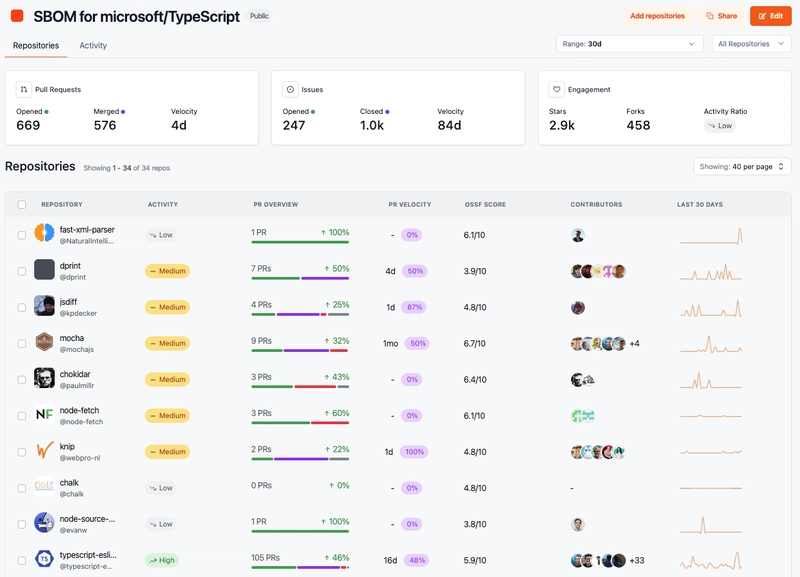
In OpenSauced, you can create SBOMS from a Repository Page. This feature allows you to generate a Software Bill of Materials (SBOM) for your open source project, providing a detailed inventory of all the software components and dependencies used in your application. For example, if I create an SBOM for Microsoft/TypeScript, I can see a list of 34 of it's dependencies, making it easier to track and manage the software supply chain.
Implementing comprehensive SBOMs could help organizations as the CRA is enforced by allowing for:
- Risk assessment of software components
- Ongoing vulnerability management
- Transparency in software composition
- Facilitating incident reporting and response
Last Thoughts
The tightening focus on software supply chain security mark a crossroad for the open source community. This shift isn’t just a challenge — it’s a chance to lead in strengthening the security and transparency of open source projects. We need to find ways to build greater trust with users, understand regulatory demands, and ensure the continued success of our projects.
Generate and review the SBOMs for your projects to see how secure the projects you depend on are. When we understand the software supply chain, we can better prepare for the changing regulations and find ways to improve our projects security.



Top comments (0)