Another great talk at the DevSecCon conference was "Container Security - Strengthening the Heart of your Operations", by Siddhant Khisty and Kunal Verma.
Kunal is a Community Manager at Kubesimplify.
Siddhant is a Community Manager at WeMakeDevs.
The video from the DevSecCon conference
Short sum up of this amazing talk, to give you some understanding till you can watch the whole video 😊
I really liked their definition of the container as a way to package an application with all the dependencies.
While dealing with container security, understanding of architecture is essential:
- Hypervisor
- (Operating System)
- Kernel
- Hardware
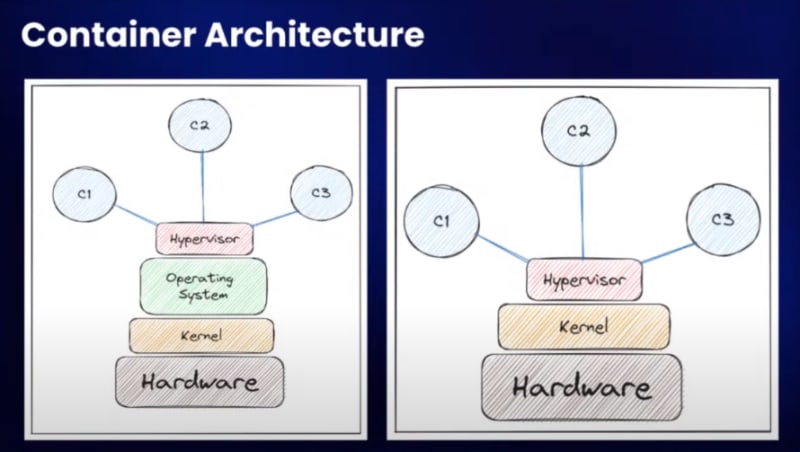
What does the container workflow look like?

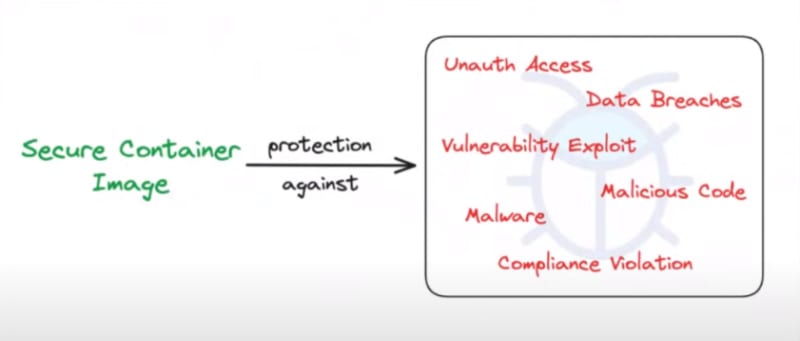
What are the reasons for securing container images?

Secure Container Image improves protection against:
- Unauth Access
- Data Breaches
- Vulnerability Exploit
- Malicious Code
- Malware
- Compliance Validation
5 questions regarding your container image security.
Q1. Are the container images up-to-date?
- use stable releases
- check for available security patches or updates
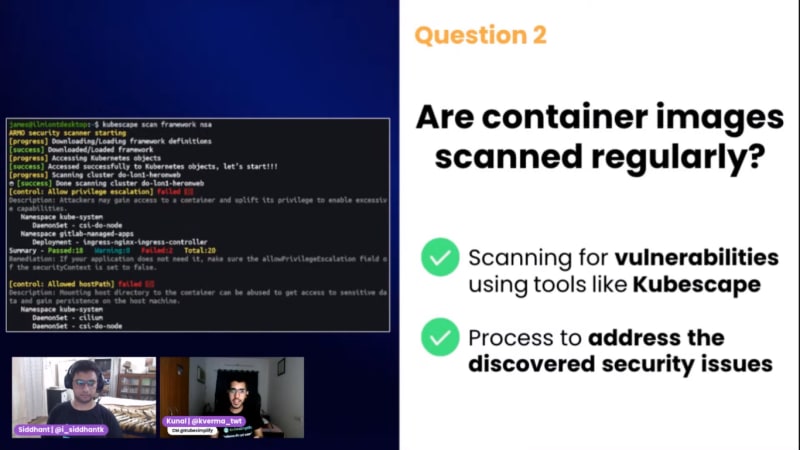
Q2. Are container images scanned regularly?
- Scanning for vulnerabilities using tools like Kubescape
- Process to address the discovered security issues
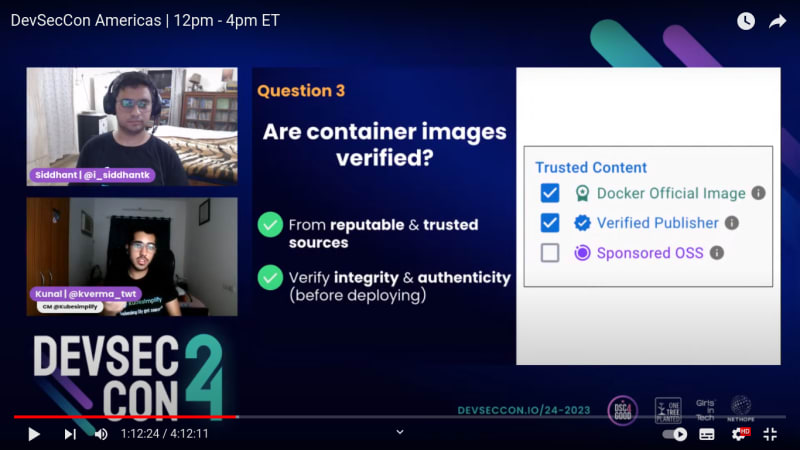
Q3. Are container images verified?
- From reputable & trusted sources
- Verify integrity and authenticity
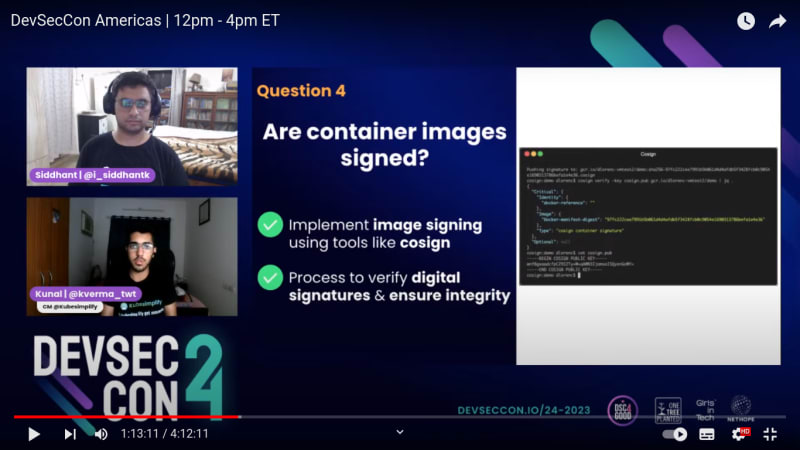
Q4. Are container images signed?
- Implement image signing using tools like cosign
- Process to verify digital signatures & ensure integrity
Q5. Is a Zero-trust model being implemented?
- Follow a zero-trust approach
- Implement strict access controls & auth mechanisms
Another key point of the talk was discussing the image registry.
Securing Image Registry is even more important than making sure your container images are secure:
- Safeguard from unathorised access or misuse
- Reduce risk of deploying compromised images
- Ensure compliance & trustworthiness
There are 4 main questions to make sure your container registry is secure.
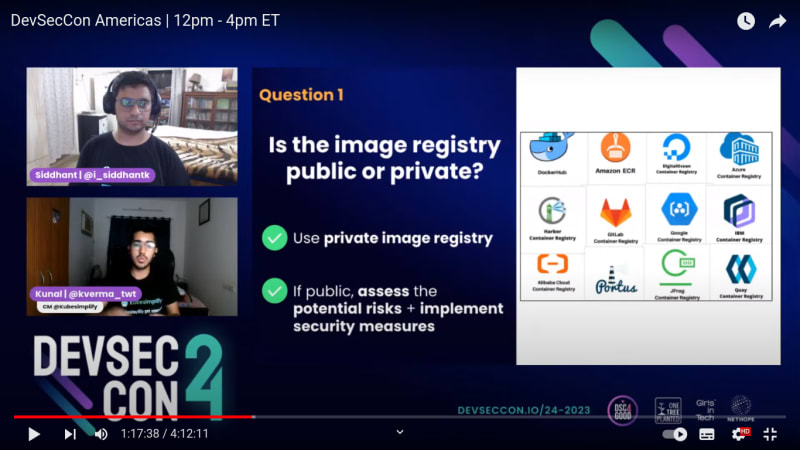
Q1. Is the image registry public or private?
- Use private image registry
- If public, assess the potential risks + implement security measures
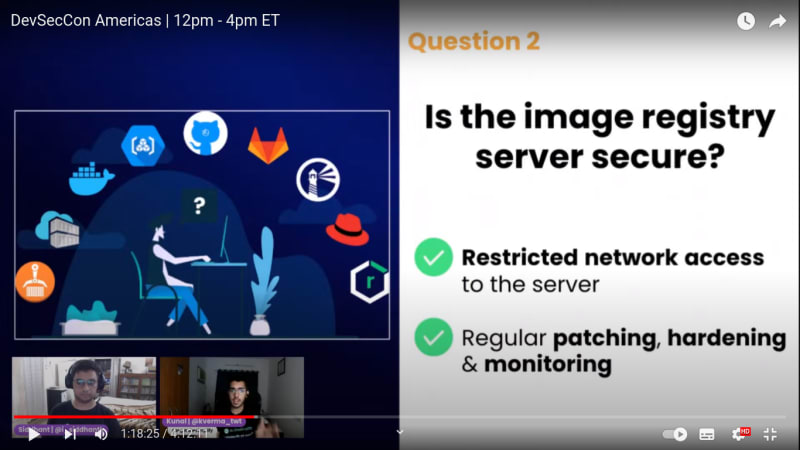
Q2. Is the image registry server secure?
- Restricted network access to the server
- Regular patching, hardening and monitoring
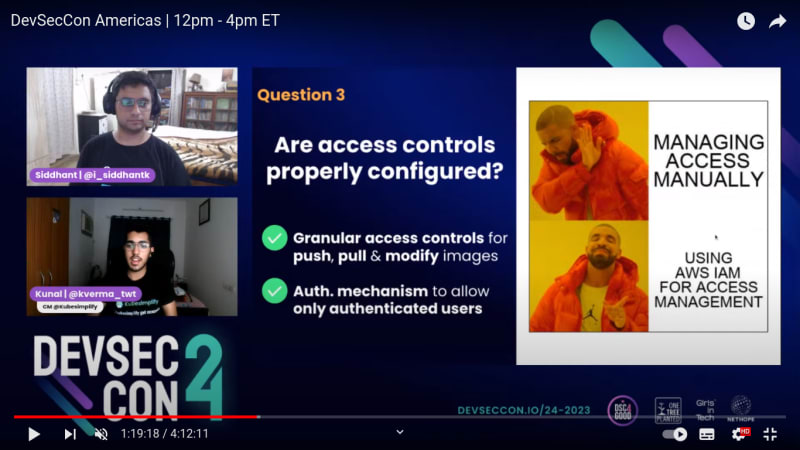
Q3. Are access controls properly configured?
- Granular access control for push, pull & modify images
- Authentication mechanism to allow only authenticated users
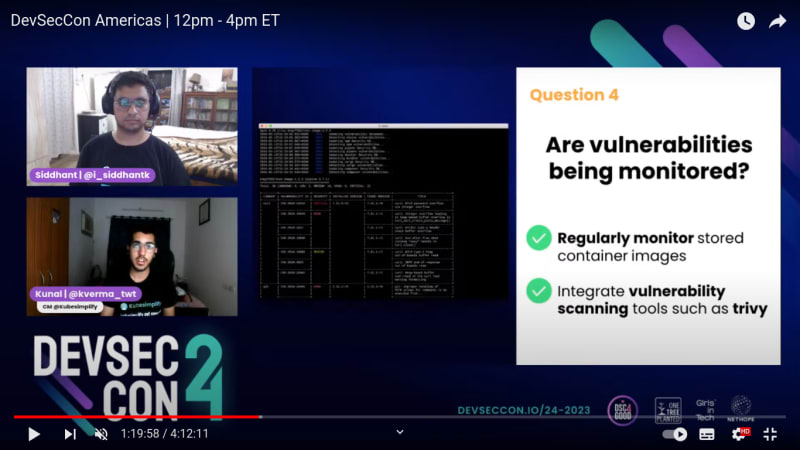
Q4. Are vulnerabilities being monitored?
- Regularly monitor stored container images
- Integrate vulnerability scanning tools such as trivy
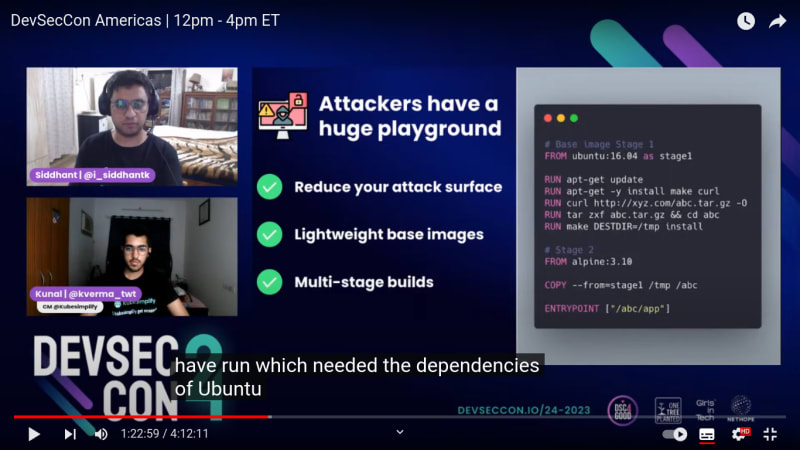
Attackers have a huge playground. How can we reduce it?
- Reduce your attack surface
- Lightweight base images
- Multi-stage builds
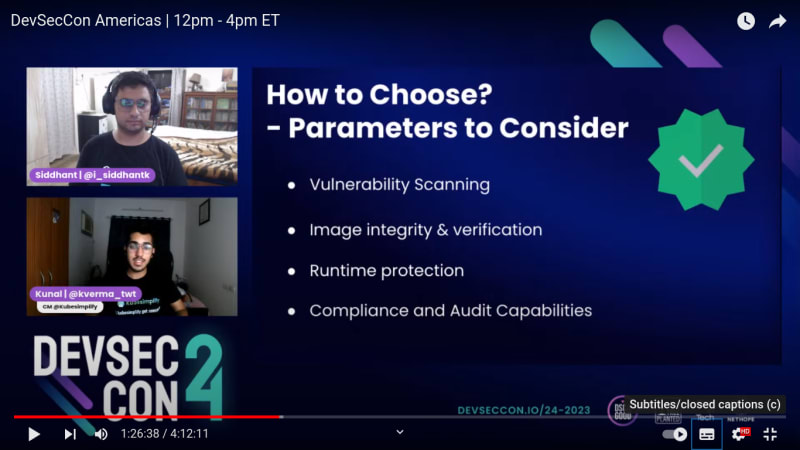
How to choose security tools? Which parameters to consider?
- Vulnerability Scanning
- Image integrity & verification
- Runtime protection
- Complience and Audit Capabilities
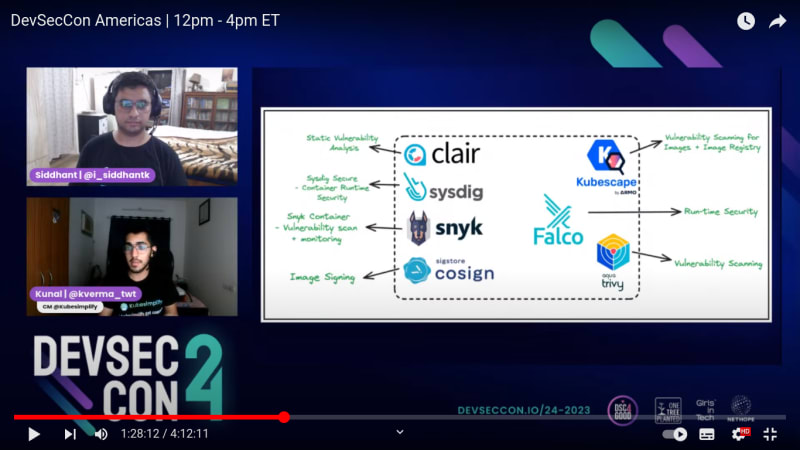
Some of the tools, which are spread around #opensource ecosystem:
- Clair - Static Vulnerability Analysis
- Sysdig - Container Runtime Security
- Snyk - Container Vulnerability scan & monitoring
- Kubescape - Vulnerability Scanning for Images & Image Registry
- Falco - Run-time Security
- Trivy - Vulnerability Scanning
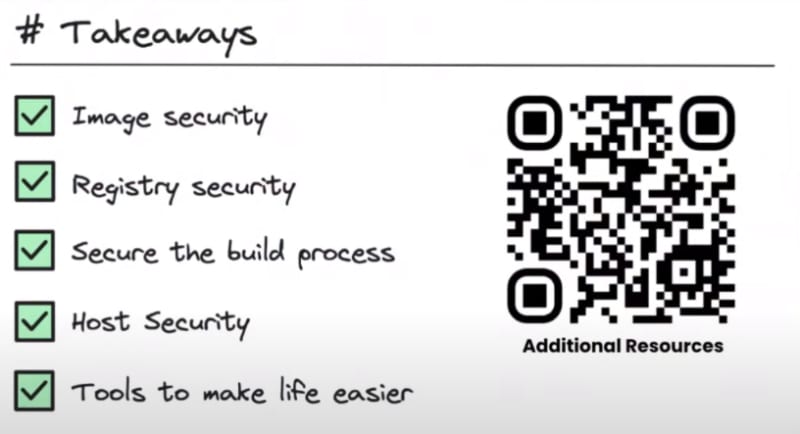
Takeaways:
- Image security
- Registry security
- Secure the build process
- Host Security
- Tools to make life easier
Overall it was a great talk and I am really grateful to Kunal and Siddhant for sharing their expertise.
Special thanks to @snyk_sec for powering the DevSecCon conference.









Top comments (2)
Thank you so much for this great read @nikitakoselev :)
You are welcome 😊