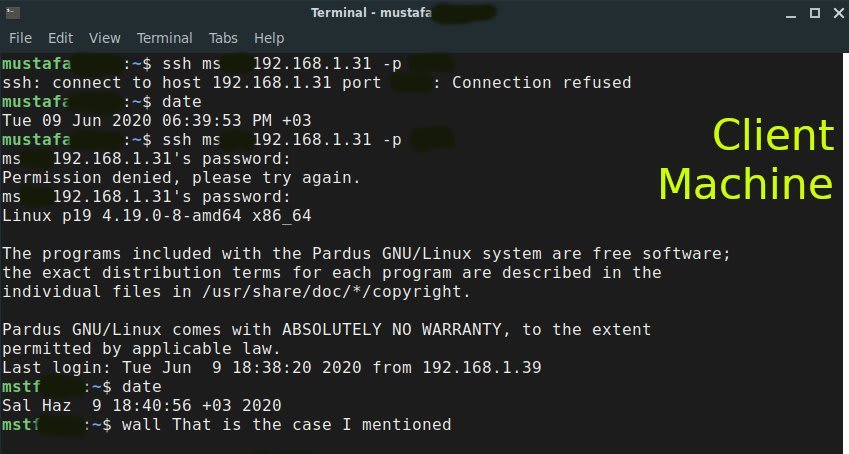
I have a question about the situation on an ssh connection. First, I install openssh-server on a Debian (buster) machine, let called as ServerMach, then I connected to the ServerMach by another Debian client.
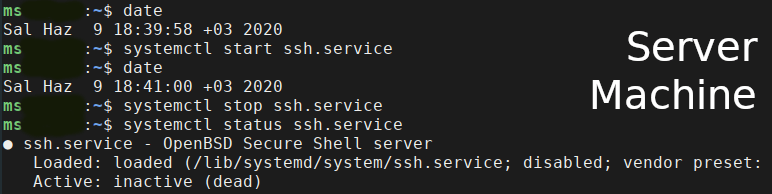
After successful connection established between client and server(time 18:40:56), I just stop ssh.services on the ServerMach (when 18:41:00) and I expect for the connection loss.
Then, I sent some further command from client machine to the ServerMach and the commands executed well.
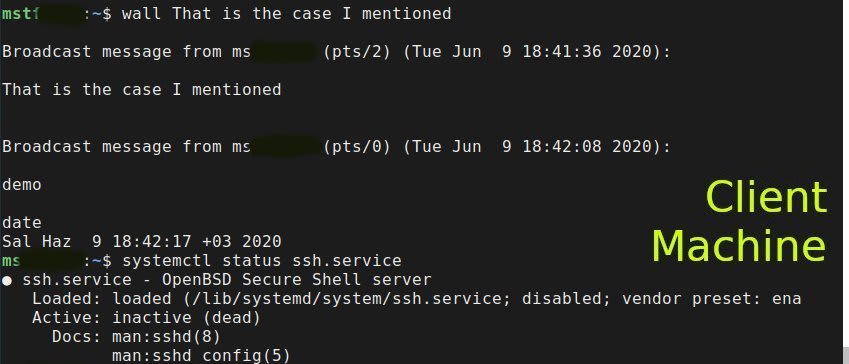
When I looking the service status, the ssh service is down on the ServerMach while the connection seems Up in processes. In addition reverse connection, which is from server to client is also active as seen below. ( "wall demo" command is executed on the server and the strings printed out to the client terminal, seen in the image above)
Then I just kill the ssh process on the client side terminal and connection now broken.

So, the question is that: There is something wrong with ssh or sshd configurations or that is an expected case for ssh connections?
Further, if an attacker open an ssh connection on target machine and they just set different port and process name for the blind ssh connection. Then, if he/she run the new blind ssh connection with changed/hidden process name and port. Let the defensive side (the protector) catch the attacker's initial ssh connection but without the blind connection information. How the defender side block or shutdown the remote connection (attacker's blind ssh connection)?
I think when the ssh.services stopped on a server all the connections should be terminated, otherwise there will be a vulnerability.







Top comments (0)