This is my first post in my AWS series.
What is IAM
IAM - Identity and Access Management
Allows who, what and how services are accessed and can interact in you AWS account.
IAM follows the rule of least priviledge i.e. only gives resources access to things it requires to perform some actions.
We can therefore create:
- IAM Users
- IAM Groups
- IAM roles
Then to manage their access to resources we attach:
- Policies Which is an entity when attached to a user/identity or resource and defines their permissions or
- Permissions Lets you specify access to AWS resources. By default resources have no permissions.
To read more on this, here is the technical documentation
Prerequisites
- Create AWS account, it is best practise to create one with MFA(Multi-factor Authentication)
Scenario
Our organisation has 3 new employees that we need to give responsibilities to, therefore we need to create 3 users: User1, User2 and User3. Since the users are in 3 different departments, they will be in different groups.
However for the sake of this tutorial, we will need to create 3 groups, attach policies to the groups and then add the users into them.
Let's get into it
Log in to your AWS account then from the AWS Management console, on the Services Menu, select IAM
-
Select users on the left side on the console then select create users, you have two options here:
- You can create multiple users at once or
- You can simultaneously create a user, then create a group and add the user and attach policies to it.
We will use method 2
Created User1
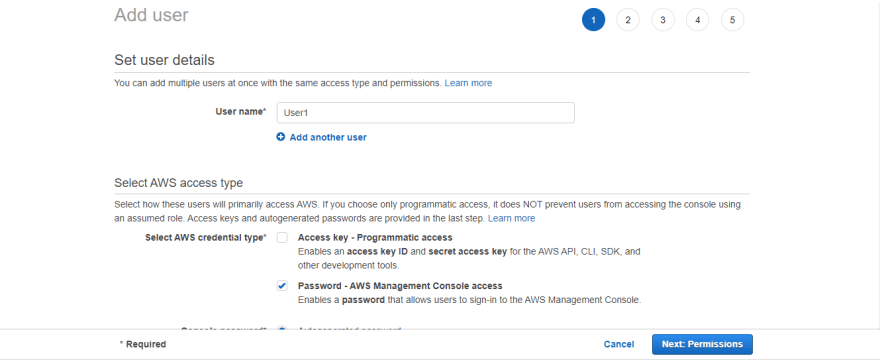
(make sure to download the csv file to access your console password)When the users are created, you can click on i.e User1 to go to their summary page.
Click on the Permissions tab and you will see that it has 1 permission attached to it, the IAM Userchange Password, which will allow the user to change their password when they first try to log in into their AWS account. This will be similar for the other users created.
Click on the Groups tabs and you will see that User1 is not a member of any group.
-
Create the groups:
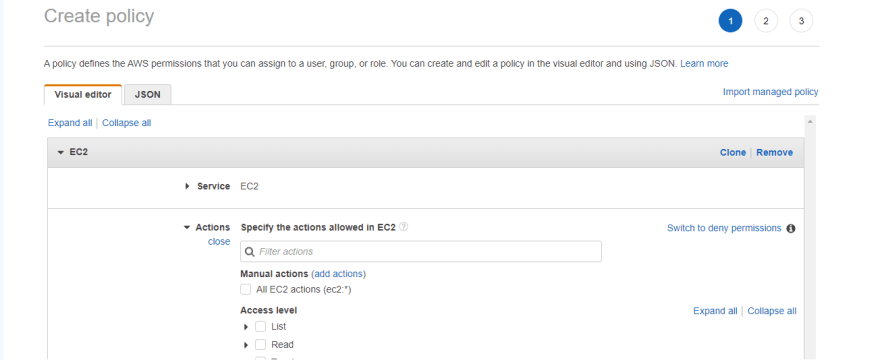
- EC2-Admin: Create an Inline policy by editing the policy to allow permission to view information about EC2 and allowing it to Start/stop instances
- EC2-Support: then attach the AmazonEc2ReadOnlyAccess policy(an AWS managed policy)
- S3-Support: then attach the AmazonS3ReadOnlyAccess policy(an AWS managed policy)
-
Add the users to their respective groups as per the Image 1 i.e:
- In the left navigation pane, click on the User Groups.
- View all the listed groups(make sure that all 3 groups were created) and click on the S3-Support group.
- In the left navigation pane, click on the Users tab .
- In the Users tab, click Add Users to group tab.
- In the Add Users to Group window, select User1(check the little box) , then add it to the respective group.
Test the sign on page for each of the users to see what they can see
In the navigation page on the left, click on dashboard
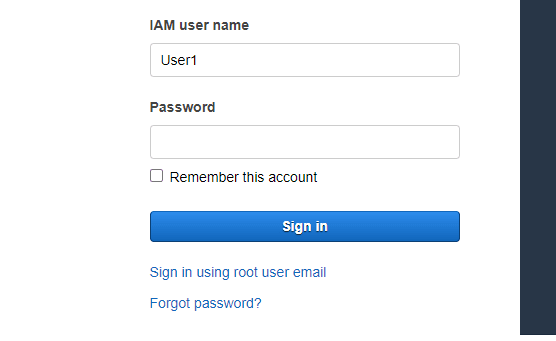
Copy the IAM users sign-in link to a text editor and open a private window, paste the link and go to it
Sign-in with :
IAM username: User1
Password:paste the value of password from the downloaded csv file for User1(you will use the password from downloaded csv files for the other users too)In the Services, click S3(in later labs, you will see output here when we create S3 buckets).









Top comments (0)