Cyber attacks have become a problem for everyone, and businesses are particularly at risk. Every day, we hear about new and sophisticated cyber attacks that can compromise sensitive information, disrupt operations, and damage a company’s reputation.
Credential stuffing is one such threat that is rapidly rising and causing damage to businesses of all sizes. This is because credential stuffing attacks are relatively easy to execute and can be highly effective, especially if users have reused the same password across multiple accounts.
User habits such as reusing passwords and using common passwords make credential stuffing attacks successful. And as per a recent study, 85% of users admitted to reusing passwords for multiple accounts.
Businesses should be aware of this attack and the steps they can take to protect themselves, their customers, and their reputation. This blog discusses the basics of credential stuffing, its impact on businesses, and, most importantly, the credential stuffing attack prevention measures that businesses can take to safeguard.
What is Credential Stuffing
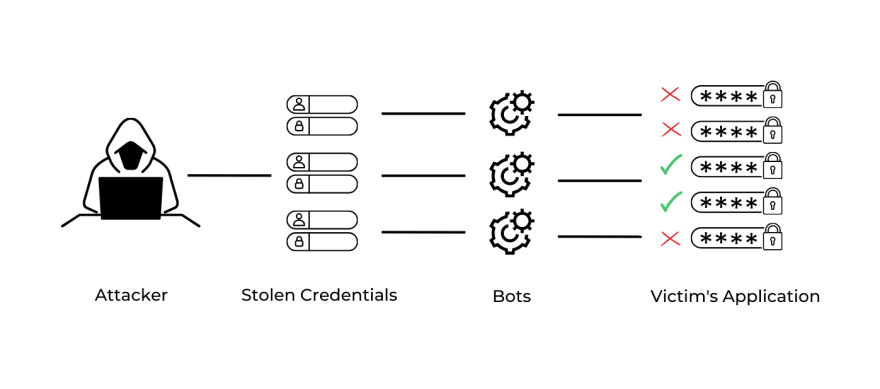
Credential stuffing is a cyber attack in which an attacker uses a list of stolen usernames or email addresses and passwords to gain access to user accounts on various applications.
Attackers generally get the list of credentials from a data breach or buy them on the dark web. They then use an automated tool to try the stolen credentials on other applications to gain access to those accounts.
Credential Stuffing vs. Password Spraying vs. Brute Force Attacks
All three attacks - Credential stuffing, password spraying, and brute force are made to gain unauthorized access to sensitive information, and it’s important for businesses to be aware of them and take steps to protect against them. The following explains the differences between credential stuffing, password spraying, and brute force attacks:
Credential Stuffing
- Uses lists of stolen credentials to attempt access to accounts
- Uses automated bots to attempt to gain access to accounts
- Often successful with reused or weak passwords
- Attackers use lists of usernames or email addresses and passwords from previous data breaches
Password Spraying
- Attempts to gain access to accounts by trying a small number of common passwords against a large number of accounts
- Tries to avoid detection by using a small number of attempts per account
- Often successful with weak or common passwords
- Attackers use lists of usernames or email addresses and commonly used passwords
Brute Force Attack
- Attempts to gain access to accounts by systematically trying every possible combination of characters
- May include dictionary words and phrases, as well as random characters
- Often successful with weak passwords
- Attackers can use specialized tools to run the attack. It could take from a few minutes to months to crack a password depending on the complexity of the password
How Credential Stuffing Attacks Work
Credential stuffing is a type of cyber attack in which someone uses a list of stolen username and password combinations to try and gain access to other accounts or services.
The following is a credential stuffing attack example displaying the three stages of attack:
1. Compiling a list of stolen credentials
The attacker first obtains a list of stolen usernames or email addresses and passwords from a previous data breach or the dark web.
2. Automating the attack
The attacker then uses automated tools or bots to attempt to access users’ accounts using the stolen credentials. This typically involves trying the stolen credentials on multiple applications at once.
3. Monitoring success
The attacker monitors the success of the attack and records any successful logins. The attacker can then use the successfully logged-in accounts to commit further malicious activities, such as fraud or identity theft.
Impact of Credential Stuffing Attacks on Businesses
Successful credential stuffing attacks provide access to users’ accounts and personal information, which attackers use to launch further attacks. Thus, it can have a significant impact on businesses, including
- Loss of sensitive data such as personal and financial information
- Disruption of business operations
- Damage to the company’s reputation
- Loss of revenue from customers who may lose trust in the business
- Increased costs to the business for incident response, customer notification, and credit monitoring services.
It’s crucial that businesses take proactive steps to protect themselves against credential stuffing, such as implementing strong authentication measures, regularly monitoring their systems for suspicious activity, and educating users about security best practices such as unique and complex passwords. Additionally, businesses should also consider implementing multi-factor authentication and have an incident response plan in place. Further sections in the blog talks more in-depth about how to eliminate credential stuffing attacks.
How to Detect Credential Stuffing Attacks
Before digging into ways to prevent credential stuffing, it is important to understand how businesses can detect credential stuffing attacks. The following are some ways of efficiently detecting credential stuffing attacks:
Monitor Logins
Monitor the login attempts and look for suspicious patterns that indicate credential stuffing attacks, such as multiple failed login attempts from the same IP address or multiple login attempts with the same username but different passwords.
Monitor IP Reputation
Monitor IP reputation for identifying the malicious IP addresses that are used in credential stuffing attacks. There are various IP reputation services available that businesses can utilize in their authentication process.
Monitor for Unusual Traffic
Monitor your network for any unusual traffic that could be indicative of an attack. Also, businesses can use machine learning-based detection systems or authentication providers that provide protection against such attacks by detecting and blocking credential stuffing attacks in real time.
How To Prevent Credential Stuffing Attacks
Defending against credential stuffing attacks is crucial for businesses to protect sensitive information and maintain the trust of their users. Here are 10 ways businesses can consider for credential stuffing prevention:
- Utilize Password-free Authentication
- Implement Multi-factor Authentication
- Monitor Systems Regularly for Suspicious Activity
- Educate Employees and Users About Security Best Practices
- Implement a Rate-limiting System
- Check Regularly for Data Breaches
- Implement IP Reputation
- Use CAPTCHAs
- Use a Web Application Firewall
- Have an Incident Response Plan
Important: A business can either implement all the above-mentioned methods for credential stuffing mitigation or simply use a third-party authentication solution that takes care of all these prevention methods.
MojoAuth is a platform that takes care of authentication and security for businesses and doesn’t let it become a headache for them.
1. Utilize Password-free Authentication
As it’s clear that attackers use stolen usernames and passwords during credential stuffing attacks, getting rid of passwords can be the most effective way to protect against this and many similar cyber attacks.
We all know that a good amount of users tend to reuse passwords no matter how well they know the repercussions. I am guilty of doing so because it is practically impossible to remember so many passwords for the applications I use in day-to-day life. For some reason, I use a password manager for my work laptop, but it does not exist in my personal life.
Many password alternative authentication methods are available for businesses to choose from that fit their requirements and provide a good user experience - Email magic link authentication, Email OTP authentication, SMS OTP authentication, Biometric authentication, Passkey authentication.
Important: If the application is using Password-based authentication already, to begin with, you can add on any password-free method to help transition your users from password to passwordless. Once the password-free method is adopted, you can make a final call on existing password authentication.
MojoAuth Login Widget lets you add passwordless authentication to your existing authentication without the hassle and acts as a credential stuffing defense layer for businesses.
- Implement Multi-Factor Authentication
Implement multi-factor authentication (MFA) to make it more difficult for attackers to gain access to user accounts. By requiring users to provide a second form of authentication, such as a fingerprint or a one-time code sent to their phone, businesses can ensure that only authorized users are able to access sensitive information.
3. Monitor Systems Regularly for Suspicious Activity
Businesses should monitor their systems and networks for suspicious activity, such as repeated failed login attempts from the same IP address. Any suspicious activity should be investigated immediately, and appropriate measures should be taken to prevent such attacks.
4. Educate Employees and Users About Security Best Practices
No security measure can be fully effective if the employees and users don’t follow security practices. Thus, it is crucial for businesses to educate their employees and users about security best practices, such as the importance of using unique and complex passwords and never reusing the same password across multiple accounts.
5. Implement a Rate-limiting System
Rate-limiting systems help in preventing automated attacks by limiting the number of login attempts that can be made within a certain period of time. Utilizing a rate-limiting system makes it difficult for attackers to use automated tools to try multiple login credentials in a short period of time.
6. Check Regularly for Data Breaches
Businesses should keep an eye on data breaches and run scans against the leaked credentials to ensure whether the email addresses and passwords of employees or users have been exposed to any data breach and if so, have them change their passwords immediately.
This approach can also be used when users set their account passwords; businesses should restrict them from utilizing previously leaked passwords or common passwords.
7. Implement IP Reputation Services
Credential stuffing attacks tend to use multiple IPs to execute login attempts, and IP reputation services help businesses identify and block such malicious IP addresses. It also checks the behavioral quality of IP addresses and restricts the unwanted login requests coming from them.
8. Use CAPTCHAs
Credential stuffing attacks use bots to launch and execute attacks, and CAPTCHAs have been proven effective in detecting bots and preventing automated login attempts. Businesses should use it with their authentication form to identify if the login attempt is made by a human or a bot.
9. Use a Web Application Firewall (WAF)
A web application firewall can detect and block malicious traffic coming toward a web application. This filtration helps businesses prevent automated login attempts by recognizing patterns in the traffic. Thus, overall reduces the success of credential stuffing attacks.
10. Have an Incident Response Plan
Taking all security measures and implementing best practices to protect against cyber attacks is in businesses’ hands, but no security measures can promise 100% protection against all attacks. Thus, having an incident response plan in place is crucial for all businesses to quickly and effectively respond to a security incident and minimize the damage caused.
Conclusion
By implementing above mentioned credential stuffing prevention measures, businesses can greatly reduce the risk of a successful credential stuffing attack. However, it’s important to note that no security measure is foolproof and that businesses should continuously evaluate and update their security measures to protect against new and evolving threats.
Sometimes, looking into all these authentication security measures can be tedious and deviating for businesses. Thus, opting for a third-party authentication provider who can effectively handle authentication and security requirements can be a good fit - as it takes extra pressure from businesses to let them focus on their niche.






Top comments (0)