User management is the backbone of Linux system administration. Whether you're setting up a personal server, managing a development team, or securing a production environment, knowing how to handle users and groups effectively is essential. This guide is designed to be your one-stop resource for everything related to user management in Linux. We'll cover every command, concept, and best practice in exhaustive detail, with practical examples, tips, and even advanced techniques. Let’s dive into the world of Linux user management and explore every nook and cranny together!
Understanding Users and Groups
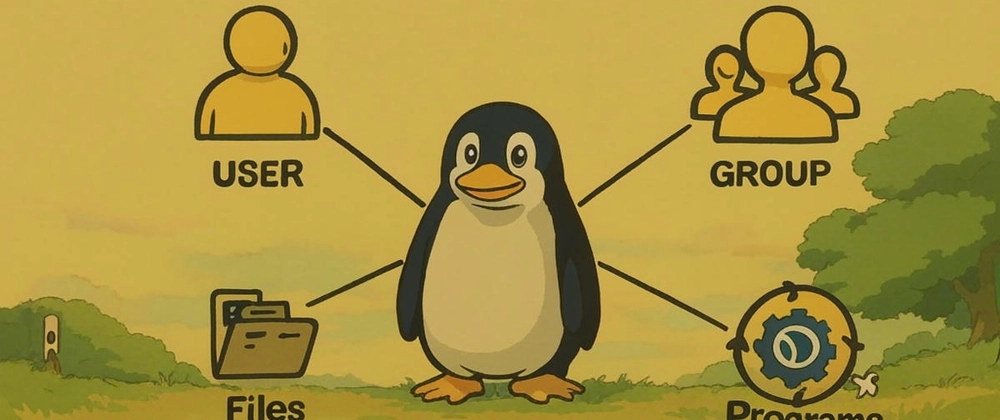
In Linux, every process—whether it's a command you run or a service in the background—operates under a user account. Users are the entities that interact with the system, and groups are collections of users that share common permissions. This structure is fundamental to Linux’s security and access control model.
Types of Users
Root User: The superuser with UID (User ID) 0, capable of performing any action on the system. Use it sparingly to avoid accidental damage.
Regular Users: Everyday accounts for humans, typically with UIDs starting at 1000 (varies by distribution).
System Users: Non-human accounts for services (e.g.,
www-datafor web servers), usually with UIDs below 1000.
Groups
Groups simplify permission management. Instead of setting permissions for each user individually, you assign them to a group and manage access collectively.
Primary Group: Every user has one primary group, stored in
/etc/passwd. New files a user creates inherit this group by default.Supplementary Groups: Additional groups a user belongs to, listed in
/etc/group, for extra permissions.
Example: A "developers" group might have access to a project directory, while "admins" have broader system privileges.
Tip: Use id to check a user’s UID, GID (Group ID), and group memberships:
id newuser
# Output: uid=1001(newuser) gid=1001(newuser) groups=1001(newuser),1002(developers)
User Account Management
Creating Users
Linux offers two main tools for creating users: useradd and adduser.
useradd
A low-level command requiring manual specification of options.
sudo useradd -m -s /bin/bash -c "New User" newuser
-m: Creates a home directory (e.g.,/home/newuser).-s /bin/bash: Sets the default shell.-c "New User": Adds a comment (e.g., full name).
Set a password afterward:
sudo passwd newuser
adduser
A higher-level, interactive tool (common on Debian-based systems).
sudo adduser newuser
Prompts for password, full name, and other details.
Automatically creates a home directory and sets a shell.
Tip: Use adduser for ease of use, especially for beginners. It’s less error-prone.
Modifying Users
The usermod command adjusts user properties.
Change shell:
sudo usermod -s /bin/zsh newuser
Change home directory:
sudo usermod -d /new/home/newuser -m newuser
-
-m: Moves existing home directory contents.
Add to supplementary groups:
sudo usermod -aG developers,admins newuser
-
-a: Appends to existing groups (omit it, and you’ll overwrite them!).
Tip: Verify changes with id or cat /etc/passwd | grep newuser.
Deleting Users
Use userdel to remove users.
Delete user without touching home directory:
sudo userdel newuser
Delete user and home directory:
sudo userdel -r newuser
-
-r: Removes/home/newuserand mail spool.
Tip: Back up critical data before using -r. There’s no undo!
Managing User Passwords
The passwd command handles passwords.
Set/change password:
sudo passwd newuser
Force password expiration (user must change at next login):
sudo passwd -e newuser
Lock account (disable login):
sudo passwd -l newuser
Unlock account:
sudo passwd -u newuser
Tip: Use passwd -S newuser to check account status (e.g., locked or password set).
Group Management
Creating Groups
Create groups with groupadd.
sudo groupadd developers
Specify a GID:
sudo groupadd -g 2000 developers
Modifying Groups
Use groupmod to tweak group settings.
Rename a group:
sudo groupmod -n devteam developers
Change GID:
sudo groupmod -g 2500 devteam
Deleting Groups
Remove groups with groupdel.
sudo groupdel devteam
Tip: If a group is a user’s primary group, you must reassign or delete those users first.
Adding Users to Groups
Add to a group:
sudo usermod -aG developers newuser
Set as primary group:
sudo usermod -g developers newuser
Tip: Use groups newuser to list a user’s groups.
User and Group Files
These files store user and group data. Avoid direct edits unless absolutely necessary—use commands instead.
/etc/passwd
Holds user account details.
Format: username:password:UID:GID:comment:home_dir:shell
Example:
newuser:x:1001:1001:New User:/home/newuser:/bin/bash
-
x: Password is in/etc/shadow.
/etc/shadow
Stores encrypted passwords and account aging info.
Format: username:encrypted_password:last_change:min:max:warn:inactive:expire
Example:
newuser:$6$abc...:18900:0:99999:7:::
-
18900: Days since Jan 1, 1970, of last password change.
/etc/group
Lists groups and their members.
Format: groupname:password:GID:member_list
Example:
developers:x:1002:newuser,anotheruser
/etc/gshadow
Secure group info (rarely used manually).
Tip: Use getent passwd newuser or getent group developers to safely view entries.
Permissions and Ownership
File Permissions
Permissions define who can read (r), write (w), or execute (x) a file, split into owner, group, and others.
Symbolic:
rwxr-xr--(owner: rwx, group: r-x, others: r--)Octal:
754(7=rwx, 5=r-x, 4=r--)
Check with:
ls -l file.txt
# Output: -rwxr-xr-- 1 newuser developers 0 Oct 10 12:00 file.txt
Changing Permissions with chmod
Set permissions:
chmod 755 script.sh
Add execute for group:
chmod g+x script.sh
Remove write for others:
chmod o-w file.txt
Recursive change:
chmod -R 750 /project/dir
Changing Ownership with chown and chgrp
Change owner and group:
sudo chown newuser:developers file.txt
Change group only:
sudo chgrp developers file.txt
Recursive ownership:
sudo chown -R newuser:developers /project/dir
Tip: Use stat file.txt for detailed ownership/permission info.
Sudo and Root Privileges
Understanding sudo
sudo lets users run commands as root or another user, controlled by /etc/sudoers.
Example:
sudo apt update
Configuring the sudoers File
Edit with visudo for safety:
sudo visudo
Grant full sudo to a user:
newuser ALL=(ALL:ALL) ALL
Limit to specific commands:
newuser ALL=(ALL) /bin/ls, /bin/cat
Group-based sudo (e.g., sudo group):
%sudo ALL=(ALL:ALL) ALL
Best Practices for sudo
Minimize sudo users.
Use
NOPASSWDsparingly:
newuser ALL=(ALL) NOPASSWD: /usr/bin/apt
- Log sudo usage (
/var/log/auth.log).
Tip: Test sudo rules with sudo -l -U newuser.
Advanced User Management
User Templates and Skeletons
The /etc/skel directory provides default files for new users’ home directories.
Customize:
sudo cp mybashrc /etc/skel/.bashrc
Managing User Environments
-
.bashrc: For interactive shells (aliases, PATH).
echo "alias ll='ls -la'" >> ~/.bashrc
-
.profile: For login shells (environment variables).
echo "export PATH=$PATH:/my/bin" >> ~/.profile
Limiting User Resources with ulimit
Limit processes:
ulimit -u 100
Limit file size:
ulimit -f 10240 # 10MB
Permanent limits (in /etc/security/limits.conf):
newuser hard nproc 100
newuser hard fsize 10240000
Tip: Check limits with ulimit -a.
Security Considerations
Password Policies
Set via PAM (e.g., /etc/pam.d/common-password):
password requisite pam_pwquality.so retry=3 minlen=10 difok=3
Enforce aging:
sudo chage -M 90 -m 7 -W 14 newuser
-M 90: Max 90 days.-m 7: Min 7 days between changes.-W 14: Warn 14 days before expiration.
Locking and Unlocking User Accounts
sudo passwd -l newuser
sudo passwd -u newuser
Monitoring User Activity
Last logins:
last
Lastlog per user:
lastlog -u newuser
Check auth logs:
sudo cat /var/log/auth.log | grep newuser
Tip: Set up auditd for detailed user auditing.
Automation and Scripting
Scripting User Management Tasks
Batch create users:
#!/bin/bash
while read -r user; do
sudo useradd -m -s /bin/bash "$user"
echo "$user:password123" | sudo chpasswd
done < users.txt
Delete users from list:
while read -r user; do
sudo userdel -r "$user"
done < users.txt
Using awk and sed for Batch Operations
Change all shells to Bash:
sudo sed -i 's|/bin/sh|/bin/bash|g' /etc/passwd
Extract users with UID > 1000:
awk -F: '$3 > 1000 {print $1}' /etc/passwd
Tip: Test scripts on a VM first!
Troubleshooting
Common Issues and Solutions
-
User can’t log in:
- Check lock status:
passwd -S newuser - Verify shell:
grep newuser /etc/passwd - Ensure home directory exists:
ls -ld /home/newuser
- Check lock status:
-
Permission denied:
- Check permissions:
ls -l - Verify groups:
groups newuser
- Check permissions:
Checking Logs for User-Related Activities
- Auth logs:
sudo less /var/log/auth.log
- System logs:
sudo less /var/log/syslog
Tip: Use journalctl -u sshd for SSH login issues.
Conclusion
User management and permission in Linux is a vast and powerful domain. From creating users to securing their accounts, this guide has covered it all—commands, examples, tips, and beyond. Whether you’re a beginner setting up your first server or a seasoned admin automating a fleet of machines, these skills will serve you well.
Written by Mohammad Aman + AI



Top comments (0)