SSL, Secure Socket Layer is a protocol created in order to place normal traffic between server and client in encrypted and protected wrapper, without any possibility of traffic being intercepted in between of transmission. SSL certificates encrypt a site information and create more secure and trusted connection. Certificates can show server's identification information to site visitors. Certificates Authorities like DigiCert , GoDaddy can issue the self-signed SSL certificates that verify the server information. In this guide I will cover how to create a self-signed SSL certificates for Apache on an Ubuntu Server which will encrypt traffic to your server. As we are generating SSL certificates are for testing purpose and not issued by any Certificates Authorities it will not provide third party validation of your server identity, but still it will help you to transfer information securely.
Prerequisites:
You need a Ubuntu server and a user with root / sudo privileges. You also need a Apache web server installed if its not there you can use following command to install Apache.
$ sudo apt-get update
$ sudo apt-get install apache2
Step 1: Enable SSL module in Apache:
In order to setup SSL certificates in Apache web server we need to enable the pre-installed Apache module. To enable SSL module in Apache use below command.
$ sudo a2enmod ssl
Once you enable the module we need to restart the Apache server for changes to be applied. Use below command to restart Apache:
$ sudo service apache2 restart
Now our server is ready to setup SSL.
Step 2: Generate a Self-Signed Certificates:
We will create a new directory where we will store server key and certificates.
$ sudo mkdir /etc/apache2/ssl
First you generate the keys for the Certificate Signing Request (CSR)
$ cd /etc/apache2/ssl
$ sudo openssl genrsa -des3 -out yourdomain.pkey 2048
It will prompt you to enter passphrase. Its up to you to enter a passphrase or not. If you do, every time you restart the Apache service you will ask for this passphrase. We will enter a passphrase and then will create a 'insecure' key from 'secure' one. Create a insure key without a passphrase form a secure key yourdomain.pkey.
$ sudo openssl rsa -in yourdomain.pkey -out yourdomain.key
And now we will create a CSR from the key file. With the CSR and key file a self-signed certificate can be generated.
$ sudo openssl req -new -key yourdomain.key -out yourdomain.csr
Once enter will ask you number of questions one most important is Common Name use your domain or IP of you server as a value.
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:US
State or Province Name (full name) [Some-State]:New York
Locality Name (eg, city) []:NYC
Organization Name (eg, company) [Internet Widgits Pty Ltd]:Organization Pvt. Ltd
Organizational Unit Name (eg, section) []:
Common Name (e.g. server FQDN or YOUR name) []:yourdomain.com
Email Address []:webmaster@yourdomain.com
Once we have CSR and key file now we can generate a self-signed certificate using following command
$ sudo openssl x509 -req -days 365 -in yourdomain.csr -signkey yourdomain.key -out yourdomain.crt
Step 3 : Configure Apache to use the Signed SSL Certificate :
Now that we have all our necessary certificates and key file available, now we can configure Apache to use these in VirtualHost. Next, add an entry to /etc/apache2/ports.conf for the domain you'll be using to host your SSL-enabled site.
NameVirtualHost yourdomain.com:443
Now create a Apache configuration file with VirtualHost entry for your site. Create a file yourdomain-ssl with below contain in /etc/apache2/site-available/folder of Apache.
<VirtualHost yourdomain.com:443>
SSLEngine On
SSLCertificateFile /etc/apache2/ssl/yourdomain.crt
SSLCertificateKeyFile /etc/apache2/ssl/yourdomain.key
ServerName http://www.yourdomain.com
ServerAlias yourdomain.com
DocumentRoot /var/www/yourdomain
<Directory /var/www/yourdomain>
Options Indexes FollowSymLinks MultiViews
AllowOverride All
Order allow,deny
allow from all
</Directory>
</VirtualHost>
Step 4 : Permanent Redirection to https :
To redirect your site permanently to https we will edit the VirtualHost entry for for 80 port which is in a file yourdominin /etc/apache2/site-available folder of Apache, or else create one with below contain.
<VirtualHost *:80>
ServerName http://www.yourdomain.com
ServerAlias yourdomain.com
DocumentRoot /var/www/yourdomain
Redirect / https://www.yourdomain.com
</VirtualHost>
Or else you can create .htaccess file in your site root folder for permanent redirection to https with below contain
RewriteEngine On
RewriteCond %{HTTPS} off [OR]
RewriteCond %{HTTP_HOST} ^yourdomain\.com$ [NC]
RewriteRule ^ https://www.yourdomain.com%{REQUEST_URI} [L,R=301]
Step 5 : Test your Apache config and activate the VirtualHost :
It is always a good practice to check your Apache configuration for any error before we activate the VirtualHost and restart the Apache service, cause Apache will not start if your configuration file has some errors. Run below command to test configuration
$ apachectl configtest
If your configuration is right then activate the VirtualHost using below command
$ sudo a2ensite yourdomain // Simple http configuration file
$ sudo a2ensite yourdomain-ssl // SSL configuration file
Now, restart the Apache service for changes to take effect
$ sudo service apache2 restart
Step 5 : Test your Setup :
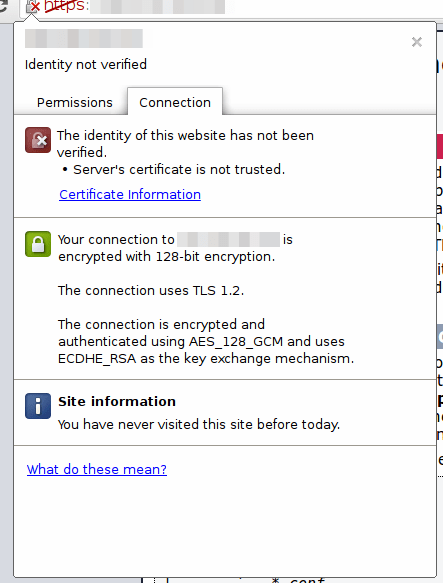
Now, that we have everything prepared and done you can try visiting your server domain name or public IP using the https protocol like this https://yourdomin.com. You will get a security warning from browser regarding your server identity because we are using self-signed certificates and it has been not signed by any certificate authority that browser trust.
Since this is expected you can move ahead, hit 'Proceed Anyway' button. Once Added Security Exception for your browser you will taken to the your site this time with encrypted traffic, check the SSL configuration by clicking on lock icon in address bar.
Hope you find this tutorial helpful. Feel free to ask questions! Don't forget to like or to leave a comment if its really help you.








Top comments (0)