Cloud Key Management Service (KMS) allows us to create, import & manage cryptographic keys and also perform cryptographic operations in a single centralized cloud service the same way on-premises. By using Cloud KMS, Cloud HSM, or Cloud External Key Manager or Customer-Managed Encryption Keys (CMEK integrations) we can encrypt, decrypt, and verify.
In this post, we are going to deal with Cloud KMS, Cloud Storage, Cloud SDK. Also, learn about encryption and manage encryption keys using KMS. So, let’s a drive-in. Sign-in to Google Cloud Platform (GCP) Console and Create a new project and activate our Cloud Shell.
Click Continue
Create a Cloud Storage Bucket
Create Cloud Storage Bucket, we can do that using gsutil, remember bucket names are globally unique. Run the following command in Cloud Shell to set a variable to our bucket name:
export CLOUD_STORAGE_BUCKET_NAME=put_our_unique_bucket_name
Now, just hit the following command, to create a new cloud storage bucket,
gsutil mb gs://${CLOUD_STORAGE_BUCKET_NAME}
Create a sample data
Create a simple file so that we can encrypt & decrypt that file, Open Cloud Shell and create a new file, Here, I’m using Vim console-based text editor. If we want, we can download the source file from another location. To create a new file, run the following command:
vi hello.txt
Input: to insert content press i,
Hello! From Cloud Storage KMS. We are going to encrypt and decrypt this file using Cloud KMS.
Note: To save that hello.txt file press Ctrl+c and type :wq . To read that file content hit below commands,
cat hello.txt
Output:
Hello! From Cloud Storage KMS. We are going to encrypt and decrypt this file using Cloud KMS.
Enable Cloud KMS Service
Before using Cloud KMS, we must need to enable that service. It could be done from Cloud Console UI and another is from gcloud CLI command. To enable the Cloud KMS Service, run the following command in our Cloud Shell:
gcloud services enable cloudkms.googleapis.com
Optional, this only needs to be done once per project
gcloud services enable cloudkms.googleapis.com \
--project "${GOOGLE_CLOUD_PROJECT}"
Create KeyRing and CryptoKey
In order to encrypt & decrypt data, we need to create a KeyRing and a CryptoKey. KeyRings are useful for Grouping keys. To create KeyRing for a global region:
gcloud kms keyrings create "our-keyring" --location "global"
Note: If we want to view that newly created key then Open Web UI.
Next, using the new KeyRing, create a CryptoKey
gcloud kms keys create "our-cryptokey" \
--location "global" \
--keyring "our-keyring" \
--purpose "encryption"
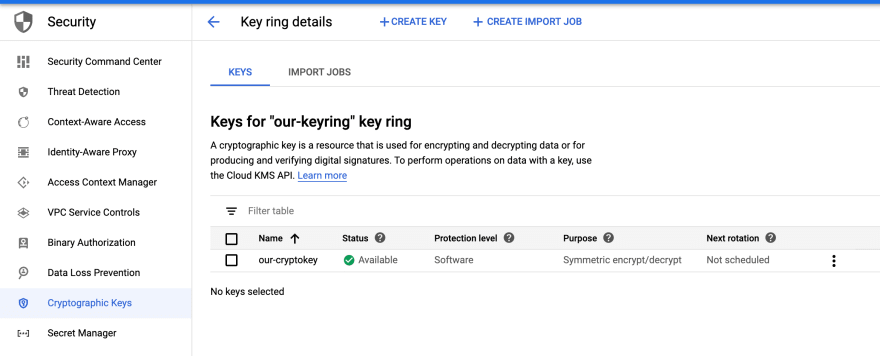
From Web UI We can view that Keys,
Click on our-keyring then we are able to see our-cryptokey, which is group together
Encrypt our file
Encrypt the hello.txt file contents using Cloud KMS. Here, I’m using the gcloud command-line tool. But we can also encrypt data using the Cloud KMS API.
gcloud kms encrypt --location "global" \
--keyring "our-keyring" --key "our-cryptokey" \
--plaintext-file ./hello.txt \
--ciphertext-file ./hello.enc
This will create a hello.enc file which will be encrypted. To open that encrypt file run:
cat hello.enc
Output: Cloud be like an unreadable hash like “6B!h>X7^RR*IRt;_*b~0IrP1<)]'ǞЉt c”
Now, we can upload that encrypted file to the Cloud Storage, run the following command
gsutil cp ./hello.enc gs://${CLOUD_STORAGE_BUCKET_NAME}
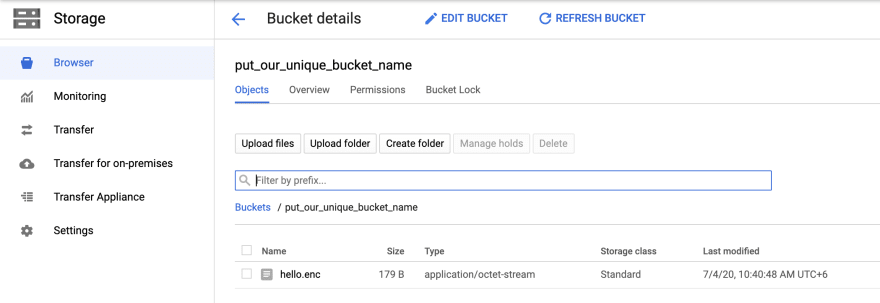
We can view our encrypted file which actually uploaded,
Decrypt our file
If we want to decrypt that hello.enc. Or, we have already encrypted data then we can copy that from Cloud Storage bucket by the following command,
gsutil cp gs://${CLOUD_STORAGE_BUCKET_NAME}/hello.enc .
Note: In this case, we don’t have to do that because we already have our hello.enc file.
Now, We can decrypt that file by the following command below,
gcloud kms decrypt --location "global" \
--keyring "our-keyring" --key "our-cryptokey" \
--ciphertext-file ./hello.enc \
--plaintext-file ./hello-decryped.txt
To open that hello-decryped.txt file run following command
cat hello-decryped.txt
Output:
Hello! From Cloud Storage KMS. We are going to encrypt and decrypt this file using Cloud KMS.
Cleanup environment
To delete cloud storage bucket, which we created earlier, run the following command
gsutil rm -r gs://${CLOUD_STORAGE_BUCKET_NAME}
Note: Cloud KMS resources can’t be deleted. However, we can destroy that by the following command
gcloud kms keys versions destroy "1" \
--location "global" \
--key "our-cryptokey" \
--keyring "our-keyring"
Congratulations
We have successfully encrypted and decrypt data using Cloud KMS and stored encrypted data in Cloud Storage. Thanks for time & passion. Feel free to ask me anything.
Say Hi to me on Twitter, Linkedin, and Medium where I keep on sharing interesting updates.






Top comments (0)