Introduction
Managing network traffic and ensuring secure internet access for resources in AWS is a critical aspect of cloud architecture. A Network Address Translation (NAT) Gateway plays a pivotal role in this. In this comprehensive guide, we'll explore what a NAT Gateway is, its features, and step-by-step instructions on setting it up in AWS using CloudFormation.
What is a NAT Gateway?
A NAT (Network Address Translation) Gateway in AWS allows resources within a private subnet to access the internet or other AWS services, while preventing the Internet from initiating a connection with those resources. It's used to provide internet traffic to EC2 instances in a private subnet in a secure manner.
Key Features of NAT Gateway
- Security: It allows instances in a private subnet to initiate outbound IPv4 traffic to the internet, while not allowing inbound traffic from the internet.
- High Availability: AWS NAT Gateway is designed to be highly available within an Availability Zone.
- Bandwidth Scaling: Automatically scales its bandwidth up to 45 Gbps without any manual intervention.
- No Need for Patching: Being a managed service, it does not require any patch management.
Prerequisites
- An AWS account
- Basic knowledge of AWS VPC, subnets, and CloudFormation
Step-by-Step Setup Using CloudFormation
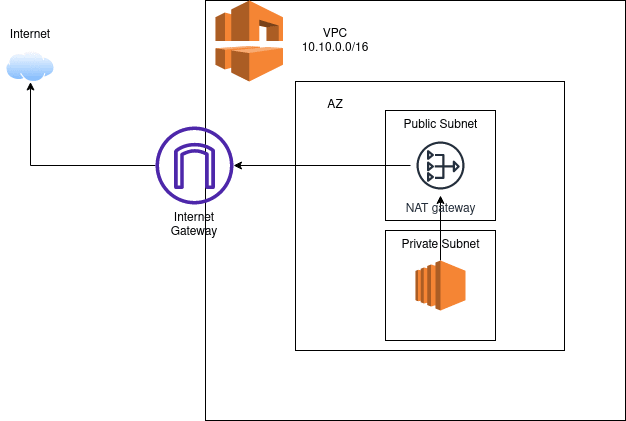
Step 1: Understanding the Architecture
The architecture involves a VPC with both public and private subnets. The NAT Gateway is placed in the public subnet, providing outbound internet access to instances in the private subnet.
Step 2: Writing the CloudFormation Template
Create a file named nat-gateway.yaml. This CloudFormation script creates the necessary components:
- VPC (MyVPC): This acts as the networking backbone.
- Subnets (PublicSubnet and PrivateSubnet): For segregating resources. The NAT Gateway resides in the public subnet.
- Internet Gateway (InternetGateway): To provide access to the internet for the public subnet.
- Elastic IP (NatGatewayEIP): A static IPv4 address used by the NAT Gateway for sending traffic.
- NAT Gateway (NatGateway): The managed NAT service.
- Route Tables and Associations: To route traffic appropriately from the private subnet to the NAT Gateway and from the public subnet to the internet.
AWSTemplateFormatVersion: '2010-09-09'
Description: 'CloudFormation Template for NAT Gateway Setup'
Resources:
MyVPC:
Type: AWS::EC2::VPC
Properties:
CidrBlock: 10.0.0.0/16
EnableDnsSupport: true
EnableDnsHostnames: true
PublicSubnet:
Type: AWS::EC2::Subnet
Properties:
VpcId: !Ref MyVPC
CidrBlock: 10.0.1.0/24
MapPublicIpOnLaunch: true
PrivateSubnet:
Type: AWS::EC2::Subnet
Properties:
VpcId: !Ref MyVPC
CidrBlock: 10.0.2.0/24
InternetGateway:
Type: AWS::EC2::InternetGateway
AttachGateway:
Type: AWS::EC2::VPCGatewayAttachment
Properties:
VpcId: !Ref MyVPC
InternetGatewayId: !Ref InternetGateway
NatGatewayEIP:
Type: AWS::EC2::EIP
DependsOn: AttachGateway
Properties:
Domain: vpc
NatGateway:
Type: AWS::EC2::NatGateway
Properties:
AllocationId: !GetAtt NatGatewayEIP.AllocationId
SubnetId: !Ref PublicSubnet
RouteTable:
Type: AWS::EC2::RouteTable
Properties:
VpcId: !Ref MyVPC
PublicRoute:
Type: AWS::EC2::Route
DependsOn: AttachGateway
Properties:
RouteTableId: !Ref RouteTable
DestinationCidrBlock: 0.0.0.0/0
GatewayId: !Ref InternetGateway
PrivateRoute:
Type: AWS::EC2::Route
DependsOn: NatGateway
Properties:
RouteTableId: !Ref RouteTable
DestinationCidrBlock: 0.0.0.0/0
NatGatewayId: !Ref NatGateway
AssociatePublicSubnet:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
SubnetId: !Ref PublicSubnet
RouteTableId: !Ref RouteTable
AssociatePrivateSubnet:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
SubnetId: !Ref PrivateSubnet
RouteTableId: !Ref RouteTable
Step 3: Deploying the Template
To deploy this template, navigate to the AWS CloudFormation console, choose 'Create stack', and upload the nat-gateway.yaml file. Follow the prompts to create the stack. You can also use the AWS CLI to deploy the stack.
aws cloudformation create-stack --stack-name my-nat-gateway --template-body file://nat-gateway.yaml
Conclusion
You have successfully created a NAT Gateway in your AWS environment using CloudFormation. This setup will enable your instances in a private subnet to securely access the internet while maintaining the security and privacy of your resources. The power of CloudFormation allows you to easily replicate this setup in different environments or regions, ensuring consistency and efficiency in your cloud infrastructure.



Top comments (0)