The benefits of this WordPress security guide are two fold:
- Learn exactly what you need to know about WordPress security in 2019. Understanding WordPress security helps you adopt a security-oriented mindset that will help you prevent and mitigate risks as you make day-to-day decisions.
- Get actionable, step-by-step instructions for securing your WordPress site. The steps you need to take aren’t particularly time-consuming, don’t require advanced technical knowledge, and the linked guides are vetted for clarity and completeness.
Of course, it’s impossible to cover every possible vulnerability and scenario. That’s why we also include the overarching “principles of WordPress security.” If you can follow these broad principles many of the minute details that are difficult to address in this type of post will take care of themselves.
Why is WordPress security critical?
It’s important you understand how big an issue WordPress security is so you give it the time and attention it deserves. Here are some sobering statistics:
- Google blacklists 10k sites a day for malware and another 50k for phishing each week. A blacklist from Google kills that source of traffic which can be highly disruptive to a business's revenue. Fixing and removing a blacklist can be a hassle, particularly if your server was used to send SPAM emails. A blacklist from email service providers harms your deliverability rate which undermines the effectiveness of your email marketing.
- In 2018, 90% of CMS hacks were WordPress. Granted, WordPress is the world’s most popular CMS with 34% of the web powered by WordPress, but this is still a disproportionate amount of hacks. For a variety of reasons, WordPress sites are targeted and exploited more than any other CMS.
- 60% of attacks target small businesses. You may think that hackers won’t bother with your site because you’re a small fish but “security through obscurity” does not exist on the web. No one is too small to be a victim of an attack.
- WordFence reports that there are over 97,978 attacks happening per minute. This is not a small, isolated problem. Large swaths of WordPress sites are being probed for weaknesses at any given time. Will you be ready if your site is targeted?
While these stats paint an intimidating picture of what you’re up against, it’s important you confront the realities of managing a WordPress site in 2019.
If your business relies on WordPress, security is not something you can afford to ignore. If you haven’t taken steps to secure your site, you’re vulnerable to attack. It could be only a matter of time until your site becomes compromised. This is one area where "an ounce of prevention is worth a pound of cure.”
The principles of WordPress security
Securing WordPress is more than checking off a list of boxes, it requires you to adopt a security-oriented mindset that guides your decision making. These principles will help you prevent mistakes as you make day-to-day decisions like adding new WordPress users, plugins, and themes:
Vulnerabilities are often introduced by WordPress users.
Vanilla WordPress that is kept up to date and uses strong passwords is relatively secure. It’s often the decisions made by WordPress users that create weaknesses that hackers exploit. This is why articles like this one are so important. It’s up to you to be educated on, and consistently follow, the WordPress security best practices outlined here.
Minimize plugins and themes.
New WordPress users are often overjoyed by the extensive ecosystem of plugins and themes available for Wordpress. This can lead to indiscriminate installation of plugins. But, each new plugin or theme adds code to your site that, potentially, adds new vulnerabilities. By minimizing the plugins and themes installed, you also minimize the amount of code your site uses, and, by extension, the number of potential security vulnerabilities. In general, if you can solve a problem without installing a plugin, that’s the best option.
Install updates as soon as possible.
Updates to the WordPress core and updates to plugins and themes often contain critical security updates. They should be installed as quickly as possible. If you have a good back up strategy in place, you can roll back to a previous version in the event the update causes issues.
Follow the principle of least privilege.
This is a core principle of cybersecurity in general and is not unique to WordPress. This is a fancy way of saying, “don’t give a user more privileges than they need because those extra privileges give hackers more power and access than they’d otherwise have if they compromise that account.”
Attacks can still happen.
You can try as hard as you can to cover all the bases and still fall victim to an attack. This is why regular, automated backups are critical. Do not ignore this advice. A hacked site can be disruptive but can generally be fixed with minimal cost and disruption, a hacked site without a backup to roll back to can be severely disruptive.
You are never finished with security.
Having a 100% secure WordPress site is an impossible task. You can’t accomplish complete risk elimination, so aim instead for ongoing risk reduction. This “risk reduction” mindset prompts you to continue taking steps to improve your security as part of an ongoing, never-ending initiative.
The most common WordPress attack vectors
Understanding the most common methods hackers use to exploit WordPress will help you understand how to address them and why the steps recommended later in this article are necessary:
Brute Force Attack
A cyber criminal uses trial and error to identify a password or pin. They use combinations of common usernames and passwords until they find the right one. It’s the equivalent of trying every key on a key ring to find the one that works. This is all done using a computer script so they can run thousands of combinations with very little effort. Given enough time, any account is hackable but strong passwords thwart this kind of attack.
SQL Injection
Malicious SQL code is injected into a database to gain access to database information that was never intended to be displayed. Depending on the hackers goals, this can lead to your database being deleted, customer information being stolen, or sensitive company information being accessed.
Malware
A virus or spyware is inserted using an expired theme or plugin. The attacker can gain access to your data, insert pages into your site for black hat SEO, and perform a number of other nefarious activities using your site.
Cross-site scripting
Javascript code is inserted which then collects data commonly used to exploit WordPress plugins. This can be used to redirect your site visitors to malicious content. also known as an “XSS attack.”
DDoS Attack
A Distributed Denial of Service (DDoS) attack floods a website with traffic which overwhelms server resources causing it to fail. Multiple machines send frequent requests to the server using malware installed on those machines for that purpose. The distributed nature of the attack can make it difficult to identify and block the sources of the traffic.
Now that you understand how hackers will attempt to breach your site security, let’s look at how we can block and prevent these attacks…
Steps to secure your WordPress site
In spite of the many ways your site can be compromised, it is possible to mitigate these risks and prevent many attacks. Here’s a list of recommended steps to protect your WordPress site from security attacks:
1. Force Strong Passwords
“81% of attacks are based on insecure or stolen passwords”
“It only takes about 10 minutes to crack a lowercase password that is 6 characters long.”
These two facts taken together make the case that you must use strong passwords for all Wordpress users. Strong passwords are long and use a combination of upper and lower case letters, numbers, and symbols. Longer is better but 20-characters is probably plenty.
Strong passwords are difficult to memorize, especially if you’re using unique passwords for each site (you should be!). This means a password manager, such as LastPass or Dashlane, is a critical tool. These apps make creating strong passwords easy, store them in a central location, and make logging into your websites easy by autofilling your passwords.
Here’s how to make sure all your WordPress users are using strong passwords.
2. Turn on automatic Wordpress Core updates
One of the advantages of using a popular CMS like WordPress is that there are many people with a vested interest in keeping it secure. Thousands of people are contributing to WordPress security by reporting vulnerabilities to the WordPress team. This widespread collaboration means most holes are patched relatively quickly. But, if the updates that contain those fixes are not applied, you leave your site vulnerable to attack.
The best way to ensure your WordPress core updates happen quickly is to turn on automatic updates. This way your WordPress site will be kept up-to-date without you having to do anything.
Here’s how to turn on automatic core updates by modifying your config.php file.
3. Stay on top of plugin and theme updates
You absolutely must keep your plugins and themes up-to-date. The importance of this cannot be overstated.
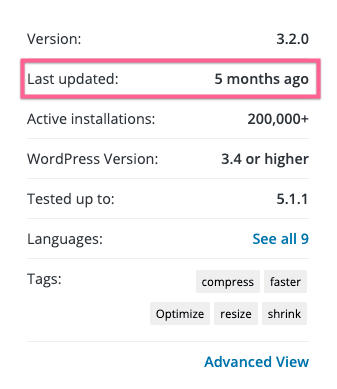
You’ll also want to be careful to use plugins and themes that are updated often. If you’re using a plugin or theme that has not received an update in months, it’s a good idea to check in with the developer or find a more frequently updated plugin that accomplishes the same goal.
When you search for a plugin in the WordPress plugin database, this information is provided in the sidebar:
4. Use Two-Factor Authentication (2FA)
Two-factor authentication adds a layer of protection to your WordPress site by making it nearly impossible for a hacker to log in to your site — even if they know your username and password.
You should set up 2FA for all WordPress users. 2FA can be set up quickly with simple, free plugins.
Here’s a list of available 2FA plugin solutions for WordPress.
5. Brute Force protection
Even with 2FA and strong passwords, it is good to setup brute force protection to help with overall performance on the server by reducing the amount of work PHP has to do.
Here’s how to protect your site from brute force attacks.
6. Create automated, scheduled Backups
In the event of an issue, there should always be recent database and file backups available. You should also create a backup before making any major changes to your site, such as installing plugin and theme updates. Many of the popular backup solutions take care of this for you.
Here’s a list of backup solutions for your WordPress site
7. Change your login pages
The default login pages for all WordPress sites are sitename.com/wp-login.php and sitename.com/wp-admin.php. Using these default login page URLs makes it easy for hackers to begin a brute force attack by trying combinations of usernames and passwords. By using a login URL that is difficult to guess, it makes it more difficult for hackers to begin the brute force attack because they don’t know where the login form lives.
Here’s how to change your login page URLs.
8. Use SSL
Secure Sockets Layer (SSL) encrypts all data sent from your website to the visitors browser obscuring potentially sensitive data. Using SSL has many benefits in addition to security. Google may rank your site higher in the search results and many browsers indicate whether a site is secured by SSL which can reassure them your site is trustworthy.
Here’s a tutorial on setting up SSL for your WordPress site
9. Don’t use the default database prefix
Using the default “wp_” database prefix makes it easier for a hacker to insert code into your database (SQL injection).
Here’s how to change the default database prefix for a new site and an existing site.
10. Check your folder and file permissions
File permissions define what actions can be applied to the files on your server. You should never set any WordPress file or directory to 777 permissions.
Instead, make sure your permission scheme is as follows:
Folders – 755 Files – 644
Here’s a guide to checking and fixing the permissions of your WordPress files and folders.
11. Disable pingbacks
WordPress pingbacks are enabled by default. But for most sites, they offer little benefit. But, they can be used to turn your WordPress site into an unwilling participant in a DDoS botnet.
To turn off pingbacks, you can go to “Settings –> Discussion” and uncheck the “Attempt to notify any blogs linked to from the article” box. It’s also a good idea to uncheck the “Allow link notifications from other blogs (pingbacks and trackbacks) on new articles” box:
12. Hide your WordPress version number
One of the ways attackers gain access to a site is by exploiting known vulnerabilities in outdated versions of WordPress. Hackers can scan your site and easily find out what version of WordPress you’re using. If that version has a known vulnerability then the hacker has a good idea of how to proceed.
The best way to prevent this is to keep WordPress up to date. However, you can also prevent a hacker from finding out what version of WordPress you’re running.
Here’s how to hide your WordPress version number.
13. Don’t use the admin username
Hackers can safely assume that a WordPress site is using the default “admin” username and that username will give them admin privileges so all they need to do is figure out the password. This gives them a direct path to gaining admin access to your site with a good probability of success. Eliminating the admin username makes it significantly more difficult to attack your site this way. If you’re already using the admin username, that’s okay, you can change it now.
Here’s how to change the admin username.
14. Use a secure Managed WordPress Host
A host that supports all the major CMSs will have difficulty staying on top of WordPress security. By specializing in the WordPress CMS alone, a WordPress hosting provider can devote the resources necessary to prevent many attacks.
A reputable Managed WordPress Host will have a security team dedicated to shielding your site from threats. They’ll handle many of the concerns raised above like taking care of WordPress updates, creating backups, and more. Here at Pagely we have a comprehensive suite of security features called PressArmor that handles both WordPress application security and server security.
Security questions to ask a potential managed WordPress host:
Is your hosting environment chrooted? If your host has multiple domains on the same server, check with them to ensure they use chroot to isolate each WordPress app. If one app is hacked, this would help prevent access to other apps on the server.
Is SSL included and easy to set up? A good WordPress hosting provider will provide SSL free of charge using a service such as Let’s Encrypt.
Do you actively monitor my site specifically for WordPress vulnerabilities? If you detect a vulnerability on my site, how will you inform me? A good WordPress host will stay on top of the latest threats to WordPress sites and constantly scan your site for those threats. If they find a vulnerability, they will work with you to address it.
Are you using a web application firewall (WAF) to protect my site? A WAF block malicious traffic before it reaches your site and can help prevent XSS attacks and SQL injections.
Here’s a list of important considerations for choosing a Managed WordPress Host.
Conclusion
WordPress security cannot be taken lightly and you must take steps to secure your site. Using a Managed WordPress Hosting Provider like Pagely is one of the best ways to improve your security because you will have an experienced team dedicated to protecting you.
Whether you choose to handle WordPress security yourself or leverage a host that specializes in WordPress, it’s important to treat WordPress security as an ongoing effort. You are never done with security but if you’ve taken the above steps you’ve protected yourself from many of the most common threats.








Top comments (1)
thanks for sharing #wordpress security