In my previous post, I explained how to access AAD protected Function App with AAD app client ID and secret.
You can protect your API endpoints by AAD that is much safer than Function key.

Access AAD protected Azure Functions
kemurayama ・ Oct 5 '20 ・ 4 min read
However, in previous scenario, you still need to manage AAD client ID and secret securely. As your service grow, your API will also increase and it becomes more difficult to recognize all secrets.
In such scenario, you can use Managed Identity to reduce your concern if your APIs/Apps are hosted on Azure Web Apps, Azure Functions or Azure Virtual Machines.
This post will explain how to set Managed Identity and access AAD protected app with it.
Prerequisites
If you are new to AAD, Azure Functions and Azure Web Apps, you can check tutorials first.
- What is Azure Active Directory?
- Quickstart: Create an ASP.NET Core web app in Azure
- Quickstart: Create a function in Azure using Visual Studio Code
In SPA scenario, you can check this repository
 Azure-Samples
/
ms-identity-javascript-angular-spa-aspnetcore-webapi
Azure-Samples
/
ms-identity-javascript-angular-spa-aspnetcore-webapi
An Angular single-page application that authenticates users with Azure AD and calls a protected ASP.NET Core web API using MSAL Angular v2 (Preview)
| page_type | languages | products | description | urlFragment | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
sample |
|
|
This sample demonstrates an Angular single-page application calling a .NET Core web API secured with Azure Active Directory using MSAL Angular v2 |
ms-identity-javascript-angular-spa-aspnetcore-webapi |
An Angular single-page application that authenticates users against Azure AD and calls a protected ASP.NET Core web API
- Overview
- Scenario
- Contents
- Prerequisites
- Setup
- Registration
- Running the sample
- Explore the sample
- About the code
- Deployment
- More information
- Community Help and Support
- Contributing
Overview
This sample demonstrates a cross-platform application suite involving an Angular SPA (TodoListSPA) calling an ASP.NET Core web API (TodoListAPI) secured with Azure Active Directory (Azure AD) using the Microsoft Authentication Library for Angular (Preview) (MSAL Angular).
Scenario
- TodoListSPA use MSAL-Angular to sign-in a user.
- The app then obtains an access token from Azure AD for the signed-in user.
- The access token is then used to authorize the…
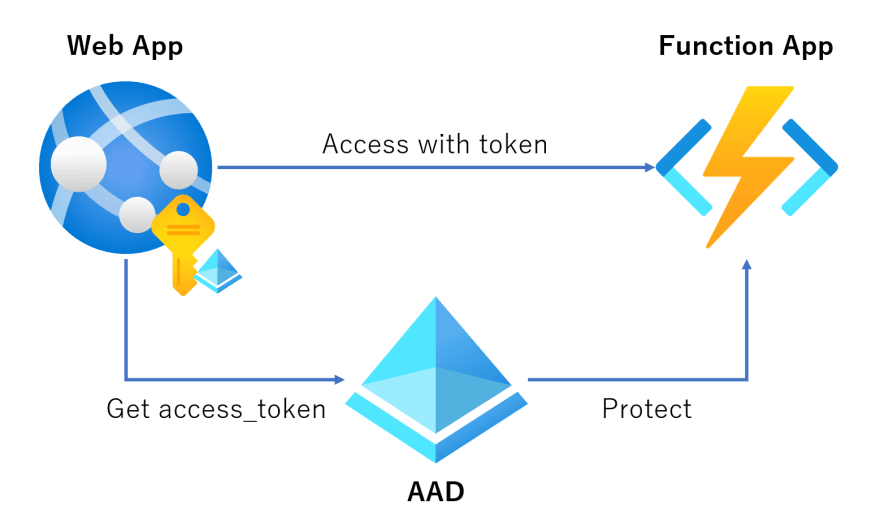
What is Managed Identity ?
Managed Identity is the feature of AAD. Imagine you use Azure Web Apps that call Function App which is protected by AAD.
Generally, you create AAD app for the Web App and get access_token with its ID and secrets to access the Functions App. With Managed Identity, you don't have to create AAD App and manage its secrets. If you host your application on specific services, AAD manage your app identity on behalf of you.
Managed Identity has two types. One is System-assinged, another is User-assigned.
System-assigned Managed Identity is one-to-one relationship between the service and ID. You can enable Managed Identity for the services. If you delete the service, Azure Platform automatically delete the ID at the same time.
User-assigned Managed Identity is similar to Azure AD App. You create Managed Identity as an Azure resource then assign it to cresponding services. The relationship is one-to-many and it will remain even you delete services. The difference between AAD App and User-assigned Managed Identity is you still don't need to manage secrets.
For detail explanation, check What are managed identities for Azure resources?
With Managed Identity, your app Blob Storage, SQL Database and more. Services that support managed identities for Azure resources
In this post, I use System-assigned Managed Identity to access Function App which is protected by AAD.
Setup Environment
I created sample apps for testing Managed Identity.
 kemurayama
/
azure-functions-python-samples
kemurayama
/
azure-functions-python-samples
Azure Functions v2.0 Python samples
Clone and run deploy.sh.
Make sure you have the permission to create AAD App and the subscription you use.
Create manifest.json to add permission to the App. Your App need User.Read API permission.
You should check your resourceAppId and resourceAcces id.
[
{
"resourceAppId": "xxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx",
"resourceAccess": [
{
"id": "yyyyyyyy-yyyy-yyyy-yyyy-yyyyyyyyyyyy",
"type": "Scope"
}
]
}
]
Test Managed Identity
After you deployed test application, you can access Web App /request_function. It calls Function App protected by AAD with Managed Identity.
Next Step
In SPA scenario, you can check this document.
With Managed Identity, you can authenticate PostgreSQL.


Top comments (0)