UBERHid is a Wifi keylogger with keyboard and mouse injection capabilities desinged and implemented by @kripthor. The project is still in early phases of development however it already allows on to perform keylogging and inject keyboard/mouse payloads. I had the opportunity to meet @kripthor during the BSides Lisbon 2019 and to get one UBERHid DIY kit.
Programmable HID (Human Interface Device) are, typically, microcontrollers programmed to act as a USB HID keyboard and mouse, and set to send certain keystrokes and mouse movement. These can work on a plug and deploy basis (e.g. the classic USB Rubber Ducky), can act when some variable changes (e.g. deploy a script when the ambient light goes bellow a given threshold) or be remotable accessible (e.g. WiFi).
The advantage of a USB HID is that it does not matter if autorun is disabled or not. By default, most operating systems seem to automatically install and configure USB HIDs as soon as they are inserted, regardless of the privilege level of the current user.1
Adrian Crenshaw has a article section on how to detect and mitigate this kind of malicious devices1.
As far as I could find there is only one solution in the market that does something similar and it’s too expensive ranging from 70 to 105 EUR: KEYVILBOARD. It has some extra features such as support for 2G communication.
Bill of Materials
| Qty. | Description | Obs. |
|---|---|---|
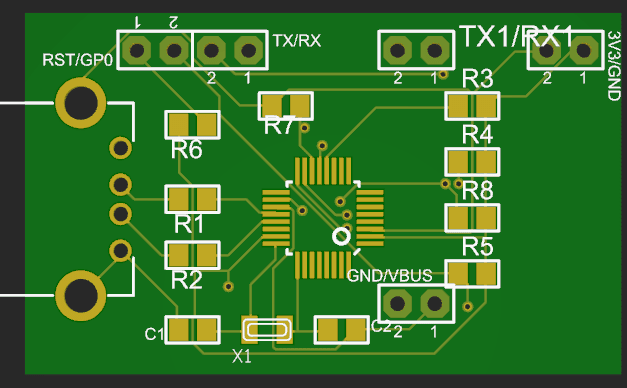
| 1 | UBERHid PCB | Designed by @kripthor |
| 1 | Arduino atmega32u4 | Board is designed for DM Micro AU version (Beetle with 18 pins) |
| 1 | ESP8266 ESP-12E module | Module to solder |
| 1 | MAX3421EEHJ+ USB | USB Peripheral Host Controller 32-Pin |
| 5 | 10kΩ Resistor | SMD. |
| 2 | 33Ω Resistor | SMD. |
| 2 | 18pF Capacitator | SMD. |
| 1 | XTAL TXC 12Mhz | SMD. |
| 1 | 2k2 Resistor | 2.2KΩ SMD. |
| 1 | FTDI FT232RL | USB to TTL Serial 3.3V/5V USB Adapter or equivalent. Used to program the ESP8266. |
- All the components can be found in the usual online stores such as Aliexpress and eBay.
Schematics
UBERHid PCB
UBERHid Schematic
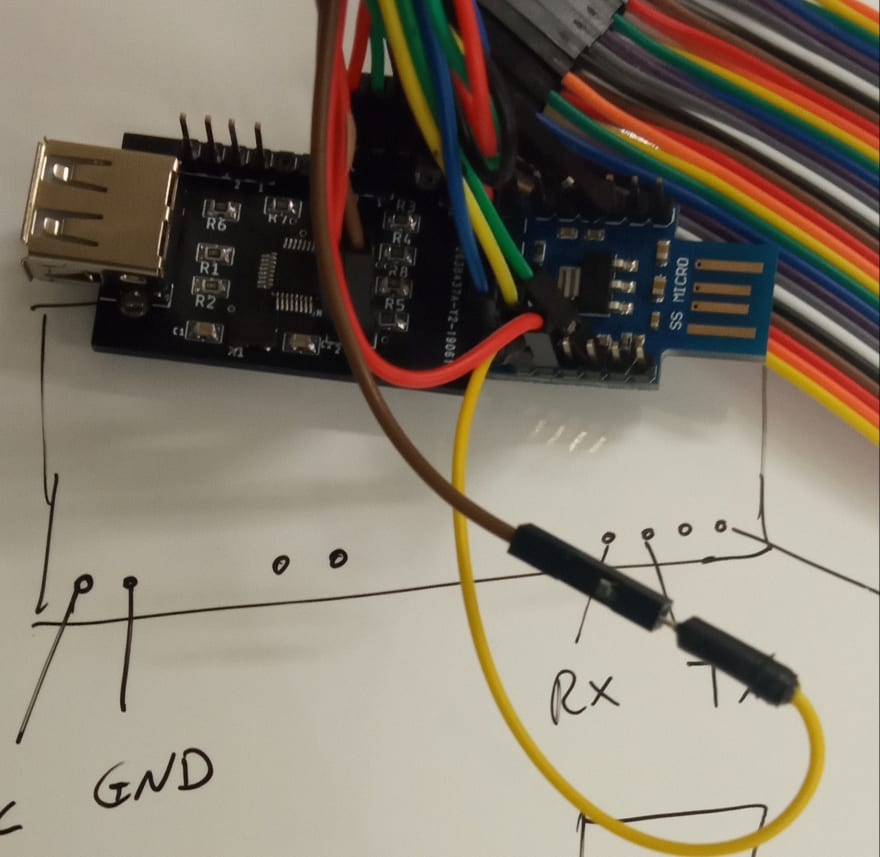
UBERHid Wiring
Details of the wiring between the ATmega32u4 and FTDI programmer. Note that the ATmega used in this case was an SS Micro version which does not have the same pinout as the recommended DM Micro AU Beetle Leonardo, which fits directly in the PCB pinout layout.
Soldering
The components must be soldered accordingly to the above schematic. Some extra details and protips:
- Start by sodering the smaller components, especially the MAX3421 chip, the SMD resistors and capacitors and the XTAL crystal.
- Two pins stay right bellow the ESP8266 chip. You have to be sure that these pins do not make any contact with the ESP8266 after the soldering is completed. I used a little of heat-resistant isolator tape to avoid any contact and soldered the pins on the other side of the board.
- Solder the ESP8266 before the remaining pinouts to have more space.
- Finish the soldering by adding the remaining pins and the USB port.
- The atmega32u4 can be soldered directly on top of the UBERHid PCB, although some jumper cables can also be used to make it possible to reuse it to other projects.
- Clean the board using isopropyl alcohol.
How to program the devices
Using Platformio
ESP8266
- Connect the FTDI to the PCB pins as depicted in the wiring scheme above.
- GPIO0 is needs to be grounded to get into programming mode.
- Uncomment the follwing lines in
platformio.ini:
src_dir = ${workspacedir}/firmware/UberHID-ESPUSB/.
data_dir = ${workspacedir}/firmware/UberHID-ESPUSB/data/.
-
$ platformio run -e esp12esanity check -
$ platformio run -e esp12e --target upload --upload-port <dev/ttyUSB*>uploads firmware- Replace
<dev/ttyUSB*>with your device, e.g.:dev/ttyUSB0
- Replace
-
$ pio run -e esp12e --target uploadfs --upload-port <dev/ttyUSB*>uploads filesystem (data folder)- Replace
<dev/ttyUSB*>with your device, e.g.:dev/ttyUSB0
- Replace
Arduino Leonardo (ATmega32u4)
- Plug-in the Arduino Leonardo in one of the computer USB ports.
- Uncomment the follwing line in
platformio.ini:
src_dir = ${workspacedir}/firmware/UberHID-Leonardo/.
-
$ platformio run -e leonardosanity check -
$ platformio run -e leonardo --target upload --upload-port <dev/ttyACM*>- Replace
<dev/ttyACM*>with your device, e.g.:dev/ttyACM0
- Replace
How to use it?
- Connect the device between a keyboard and a computer.
---------- --------- ----------
|Keyboard| <-> |UBERHid| <-> |Computer|
---------- --------- ----------
- Connect to the device access point.
- It can be visible or hidden depending on the configuration on file
Config.hinfirmware/UberHID-ESPUSB. Other configurations available are the access point name and password.
- It can be visible or hidden depending on the configuration on file
#define WIFISSID "UBERHID"
#define WIFIPASS "uberidiota"
#define WIFICHANNEL 7
#define WIFISSIDHIDDEN 0 // 0 for not hidden
Navigate to 192.168.4.1
- You can see the keystrokes in realtime and inject keyboard and mouse commands. Also, you can RickRoll your friends.
Final Result
I still need to reduce the jumper chaos with smaller jumpers or with the other version of the ATmega32u4 that plugs directly into the designed PCB. And a 3D-printed case!
There are still a lot of features under development, such as adding support for Wifi attacks that can be performed using an ESP82662,3.
References
Plug and Prey: Malicious USB Devices by Adrian Crenshaw] ↩ ↩2
ESP8266 Deauther 2.0 by @spacehuhn ↩











Top comments (0)