In this article, I will do my best to explain self-sovereign identity from the end-user perspective, without any technicalities.
Self-sovereign identity (SSI) is, simply put, a decentralized digital identity, but before we dive in, let’s look at what identity and digital identity actually means.
Identity
Identity is not only about a physical identity card issued by the government. An identity is a group of various attributes and relationships describing the existence of each individual. Some of these attributes we get assigned (like a name), some of them just happen (like date of birth). It could be our capabilities, our relationships, our biometric information, and our behavior. All these attributes belong to our identity. We can be uniquely identified based on some of these attributes in a given context. Sometimes our first name is good enough, sometimes we need our last name or date of birth. In a more formal context (communication with the government for example), we need an ID card with an ID number on it, which was given to us. On the other hand, our friends probably wouldn’t need to see our ID card but could be skeptical about our behavior, in both positive and negative ways. Remember when you did something unexpected and your friend was confused, asking “Who are you?”.
Nowadays, we usually use physical documents such as an ID card, driving license, birth certificate, university diploma, marriage certificate, and so on, to prove our particular identity attributes. How can we do the same thing in today’s digital world?
Digital Identity
You probably already have some sort of digital identity. Do you have an account on any social network? How many usernames and passwords do you have? I bet it’s plenty. Every username and password represent your so-called user account to access a specific software system (web or mobile application). Such system also keeps other information about us, like name, birth date, address. It sometimes also links your user account with other user accounts, representing your “digital” relationships with these users. As you can see it’s really similar to the identity description above. However, it has some problems.
Problems with Digital Identity
- It’s hard to reuse our data. There are systems that require more than just your e-mail (as username) and password. Such systems often require additional personal details like date of birth, residence address, and sometimes even more. This data is usually usable only on the specific software platform. You’re vendor locked-in.
- You have to provide this data all over again and you are actually not able to remember what you’ve shared with whom. It brings us to a problem where there is a large amount of duplicated data in the systems we’re using.
- We can partially solve this data reuse and duplication problem by using a mechanism called single sign-on. Single sign-on is when you see buttons like “Log in with Facebook” or “Log in with Google”. First, you log in with your Facebook username and password, then when you’re trying to log into another system, it asks Facebook who you are and creates your user account based on that. The benefit is that you don’t need to create yet another password. The problem is that it creates centralized silos of data. Let’s say you’re using Facebook as a single sign-on on every other web application. Your digital life becomes dependent on Facebook. You have to hope they won’t cut you off from their service (yes, they can do that) or you won’t have a reason to leave. Facebook also knows exactly when and where you’re logging in. If there is a data breach, your user accounts in other software applications are at risk. These centralized silos of data are problematic even without single sign-on. Services with a huge amount of users with one centralized database are honeypots for hackers.
- If you follow current security recommendations, you should use a new username and password for every new registration to an application. Even if you don’t use a new username, but you just create a new password and use your e-mail as a username, it’s still too many passwords to manage. You can solve this with a password manager, and you should (really, go and install one right now). However, using your e-mail as a username has its own issue. What if you want to change your primary e-mail address? I’ll let you think about the consequences of such an act :). It’s possible to get rid of all usernames and passwords with SSI. I’ll explain how later.
Decentralization
So far we’ve discussed identity and its digital representation. What about that decentralized part which is so crucial for SSI?
Let’s look at physical documents. These documents contain selected attributes about our identity attested and issued to us by an authority. They have signatures, stamps and other watermarks to provide tamper-proof and trust. Whoever trusts these signatures and authority, trusts the data on the document and doesn’t have to contact an issuer for every verification. We have it under control and in our possession, stored in a wallet or in other places. They’re already somehow decentralized. For example, my ID card contains my ID number, first name, last name, date of birth, and address. It’s attested by the government. I can use it to prove my age in a liquor store and the merchant doesn’t have to contact the government.
We can do the same with digital documents. Of course, we’re not able to sign it with a physical signature, so we need to use a digital signature. Instead of storing such documents in our physical wallet, we save them in a software wallet, which could be an application on our mobile phone, tablet, or laptop. These documents are called verifiable credentials and we can use them in both the digital and physical world.
Just Scan a QR Code
I’ll demonstrate some scenarios of how it could work in the real world. We start with a software wallet, most likely in the form of a mobile app that we can download from an app store. Then, we go to the government office just as we go there for a new ID card. A clerk will generate a QR code on a display. We scan it with our mobile app and get our government identity card in the form of a verifiable credential. Now, we can go to a bank website to open a bank account. The bank website shows a QR that contains the information they need from us to open the account. We will see the requested data in our mobile app. If we confirm this share request, the bank will verify the digital signature from the government, and if the bank trusts this they can open an account for us.
Verifiable credentials are not only about a digital identity card. You can have almost any document you can imagine in the form of a verifiable credential. It could be a bank account statement proving your income, certificate or diploma proving your education, or just an ordinary public transport ticket. Another example could be an application for a credit card. Let’s say you have a bank account in ABC bank and you want a credit card in XYZ bank. You go to the XYZ bank website, scan a QR code and share your ID number, last name, and address from the digital identity credential together with your income for the last 3 months from bank account statement credentials issued by ABC bank. No more filling sensitive data into endless forms again and again. Similarly, you can get a verifiable credential representing your university diploma and then share it with your new employer. This way, you are building your decentralized digital identity one credential at a time.
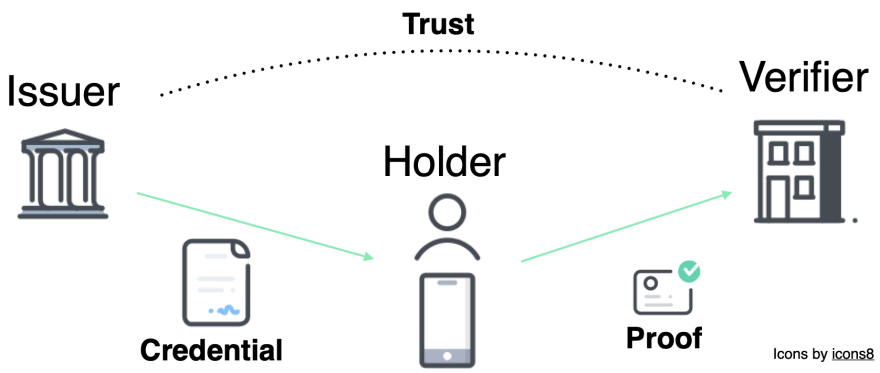
Roles of SSI
There are three basic roles in SSI. Issuer, verifier, and holder. The first scenario above described the government as an issuer, issuing an ID card credential, the bank as a verifier of the credential, and us, users, as holders of the credential. In the second scenario with a credit card, one bank was an issuer of a bank account statement and the other was a verifier. The reason I’m explaining these roles instead of just using government, bank, and user directly is because who is in what role depends on the exact use case. Let’s say I want to verify if an e-shop is a legit business by verifying its business license before I place an order. Then I can issue a credential to my friend to receive the delivery if I’m not at home.
Principles of SSI
Each party in the examples demonstrated above needs some software to participate in a credential exchange. This software doesn’t have to be from the same provider at all. If everyone is compliant with self-sovereign identity standards, we can use whatever vendor or platform we want and still be interoperable. This also allows for portability from one provider to another. Remember, we need to have data under our control and decide where it will be stored. Therefore we should be able to move our credentials from one mobile app to another, keeping all of them usable and valid.
The software wallet securely stores all credentials encrypted and accessible only via biometric or passcode authentication. Each credential exchange is done via a secure communication channel. It’s created when a user scans the QR code or reused if the channel with the given party already exists.
Last thing I kept intentionally until the end is minimal disclosure, the best of all these innovations brought by SSI from my perspective. With physical or ordinary digital documents we need to share the whole document even if another party asks us just for one attribute. Let’s look at the date of birth and liquor store use case again. We need to share the whole ID card with the merchant although they look at the date of birth only. With verifiable credentials, we can use modern cryptography to disclose just one attribute while preserving data integrity and signatures. We can go even further and disclose only that the required attribute is in a given range without revealing the exact value. Imagine proving you’re older than 21 without revealing your age, proving your income is higher than a specific amount without revealing your salary or that you live in a specific city without revealing your exact address.
That’s all for the introduction to SSI. I hope I got you excited about this amazing technology. I tried to keep it high level so I can imagine you have a lot of questions. If so, don’t hesitate to ask and stay tuned for other articles that will probably go deeper.



Top comments (3)
Very well written introductory article!
... and then revoke the credential when my friend betrays me and I don't trust them anymore :) Revocations are also important, cool and useful, maybe along with composability - that you can ask for and disclose attributes from multiple credentials at once (in a single proof).
Thank you for putting together this excellent introduction to SSI and the Principles of SSI.
The Sovrin Foundation has been working on Principles of SSI and some of the latest work is available from github.com/sovrin-foundation/possi...
This is the first time I am understanding SSI and you did really well to explain it, bro