Today's rapidly evolving enterprise networks are highly reliant on cloud-based applications to run a multitude of business operations and use cases. In addition, the growth in the need for connectivity for business use-cases and mobile/remote users has resulted in the traditional enterprise network expanding beyond the network edge, thus bringing in a challenge to guard, secure and manage the network edge against vulnerabilities. Therefore, it is imperative for network owners to keep up with the latest security practices, frameworks and tools, rendering VPN-only solutions obsolete.
For enterprises to remain safeguarded and competitive in today's network landscape with a zero-downtime, all network endpoints must be secured and managed with the same security and networking policies as their on-premises infrastructure. This is what makes a use case for SASE.
The term SASE was coined by Gartner in 2019 & was introduced to bring a highly customizable network with security services seamlessly stitched into the cloud platform. Secure Access Service Edge (SASE) architecture refers to a cybersecurity environment that brings advanced protection right out to the farthest edge of the network: the endpoints of users. In this SASE architecture definition, users are provided robust security features directly to their devices from the cloud, enabling them to connect securely from anywhere.
SASE brings multiple cloud-native security technologies together—Secure Web Gateway (SWG), Cloud Access Security Bearer (CASB), Zero Trust Network Access (ZTNA), and Firewall Solution as a service (FWaaS) with WAN capabilities to help users and systems connect securely to a service or any application; anytime and anywhere. Furthermore, since there is a need to make the ecosystem operations agile, the network's security is delivered as a service from a centrally managed cloud.
Market Predictions for SASE
With a 20% adoption rate expected by 2023, Gartner claimed that the demand for SASE capabilities would "redefine enterprise network and network security architecture and reshape the competitive landscape". While SASE frameworks won't be implemented in a day, the route to SASE is gaining speed and urgency. Another research by Palo Alto Networks and Gartner predicts the following for the future of SASE:
- By 2025, 80% of enterprises will have adopted a strategy to unify web, cloud services and private application access using a SASE/SSE architecture, up from 20% in 2021.
- By 2025, 65% of enterprises will have consolidated individual SASE components into one or two explicitly partnered SASE vendors, up from 15% in 2021.
- By 2025, 50% of SD-WAN purchases will be part of a single vendor SASE offering, up from less than 10% in 2021.
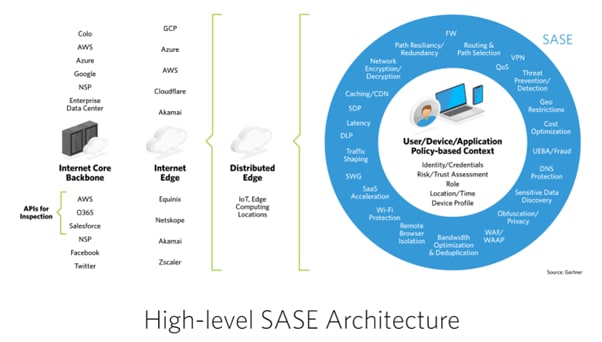
SASE Architecture and Components:
SASE network architecture provides cloud security to the farthest end of the network without relying on specific infrastructure. It allows users to connect directly to the cloud while enjoying security running on their devices. It enables a secure connection and decrease in latency resulting from backhauling to the data centre's firewall.
SASE services involve cloud-hosted security, zero-trust network access (ZTNA) components, and network services components.
Cloud-hosted Security:
Cloud-hosted security enables devices to be independent of relying on security hosted on a physical data centre.
- Firewall-as-a-Service (FWaaS): FWaaS provides standard hardware firewall services using software in the cloud. Users do not have to connect to a physical firewall & data transmissions are protected through the cloud-hosted software.
- Secure Web Gateway (SWG): Secure Web Gateway blocks unauthorized traffic from getting into the network, thus protecting the network from intrusions. In SASE architecture, an SWG is implemented for every device connected to your network.
- Cloud Access Security Broker (CASB): CASB is positioned between the user and the cloud-based application they are trying to access. It monitors, implements and enforces an enterprise's security policies.
Zero-trust Network Access (ZTNA) Components:
Zero trust network access (ZTNA), also known as the software-defined perimeter (SDP), is a set of technologies and functionalities that enable secure access to internal applications for remote users. It operates on an adaptive trust model, where trust is never implicit, and access is granted on a need-to-know, least-privileged basis defined by granular policies.
- Authentication: Authentication involves verifying the user and device they claim to be. This is usually achieved using multi-factor authentication (MFA).
- Authorization and Control: Authorization involves choosing where a user is authorized to access a network. Control includes restricting their movement within the network's environment.
- Monitoring: Monitoring in a SASE architecture is critical to security. It involves checking which devices are connected, their activity, quality and volume of data exchange using those devices, etc.
Network Services Components
Network services components facilitate optimized path selection and application-based routing within the SASE architecture.
- Optimized Path Selection: Optimized path selection involves ensuring the paths of different traffic brackets are directed to the right resources at the appropriate times. This is usually achieved using an SD-WAN solution that can decide the network traffic routing and its management to ensure low latency and a high-efficiency network.
- Application-based Routing: Application-based routing gives the user access to the specific applications they need access to complete their designated work. This allows a SASE architecture to provide seamless & safe remote access to workers anytime and anywhere.
Benefits of SASE:
Traditionally, network security was hosted on the network edge within the corporate perimeter and the data centre, with all traffic routed through the data centre for validation and check. A SASE-based approach moves these capabilities to the cloud, where multiple applications are hosted, reducing the latency between the user and application and backhaul requirements.
- Higher Efficiency in Hybrid/Remote Work Model: The legacy and traditional remote security models are increasingly becoming outdated and vulnerable to hackers due to broad use. A unified security service over a single cloud platform eliminates delays as traffic 'trombones' between different point security solutions.
- Higher IT Operational Efficiency: One of the benefits of SASE is that IT teams no longer need VPN licenses for each user and troubleshoot network security hardware or provide different security access systems within the same network. This increases the IT team's operational efficiency.
- Reduce Hardware Costs: Buying network security hardware is expensive as a standalone device as purchasing network firewalls and DDoS mitigation boxes do not help. The costs incurred are always on the higher side with CAPEX and OPEX involved (installation, warranties, repairs, patch management, updates, etc.). These costs can be eliminated by moving network security to the cloud can create additional savings.
- A centralized policy with local enforcement: SASE enables Cloud-based centralized security management with distributed enforcement and decision-making for the network stakeholders and users.
- Network Agility & transparency: SASE promises a consistent application experience anywhere & on any device. It also reduces operational overhead by recognizing and updating new threats and policies without new hardware or software.
The approach to adopting SASE:
Juniper Networks recommends the following approach for the adoption of SASE:
- Data distribution model: Looking at the data holistically as the data would likely be stored in multiple places.
- Protection for data in transit and at rest: Ensuring consistency in policies and procedures over data within the environment (both edge and at rest). Access control, encryption and segmentation of data.
- Centralized visibility and policy control: A transparent approach to documenting people within the network, the data shared by them, the connections accessed by them, access authorization, policy towards handling noncompliance, etc. Ensuring attention is focused on the entire network and not just the edge.
- Improvement areas, addressing efficiency: Looking cohesively at the current projects & if they would need to accommodate cloud-hosted services in the next 2-4 years, backup services considerations (local or cloud-based), dealing with sensitive services.
- Data segmentation over data centre and multiple public clouds: Handling security mishaps at the edge. Adopting a fool-proof approach to protect sensitive data residing at the data centre. Keeping visibility throughout the environment, not just at the edge, keeps the data protected.
- Data flow path and migration: Inspecting the current data flow in the organization's on-premises deployment and ensuring smooth flow by making appropriate changes. A comprehensive plan to identify how the data would move to ensure its integrity across environments.
Conclusion:
The focus on adopting SASE and Secure Edge within organizations continues to grow, pushing a broader basket of integrated cloud-based cybersecurity technologies into a more consumable form. The industry would see some consolidation, integration, and M&A in the SASE market over the years as the number of players in the SASE market continue to grow globally. SASE promises to handle vulnerabilities at every network edge: data centre, branch, cloud & mobile. Currently, these solutions come from varied vendors; hence interoperability will be critical for all vendors. This could also drive their consolidation approaches from enterprises & demand for the adoption of unified SASE solutions.



Oldest comments (0)