In this blog, I will demonstrate how to automatically delete S3 buckets in all AWS regions based on a pre-defined schedule using EventBridge and Lambda.
1. Problem statement
We have many S3 buckets in several AWS regions in our account. Due to some reasons, our task is to delete all those S3 buckets in a pre-defined schedule such as once per week, once per month. A manual deletion using AWS management console will be a burden and time-consuming job. So, we have to figure it out in automatic way, which help us save our effort. Currently, AWS provides services that help us out.
2. Solution
We will use 02 services to automatically delete all existing S3 buckets in all AWS regions in a schedule. The workflow is shown as below:
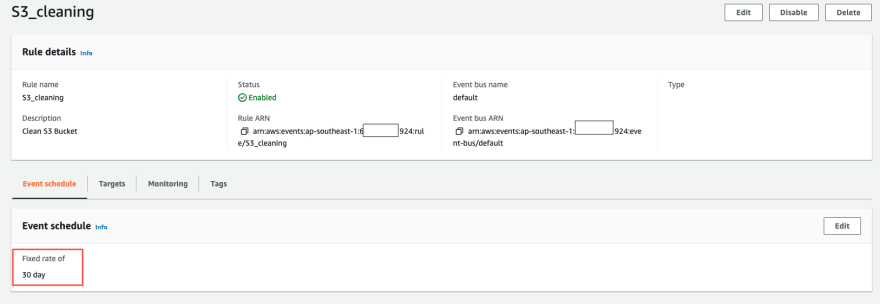
- EventBridge: A serverless event bus that let you receive, filter, transform, route, and deliver events. EventBridge can be considered a rule-driven router, which allows to define event patterns based on the actual content of the events to decide that targets receive each event passing through the bus. A target can be Lambda, AWS SNS, AWS SQS, etc. A rule in EventBridge that run on a schedule by using rate expression or cron expression can trigger a Lamda function to do a specific job. The following show a rule, which will run each 30 days using rate expression.
- Lambda: A serverless service that run a custom code to delete all S3 buckets in all regions. It will be triggered periodically to run the function by a given EventBridge rule.
In order to delete a S3 bucket, all resources inside the bucket such as object, access points, etc. must be deleted in first. For multi-region access points, because all requests to create or maintain will be routed to the us-west-2 (Oregon region), the lambda function, which runs code to delete S3 buckets, should be deployed in us-west-2.
Refer to this for more information.
Lambda deployment:
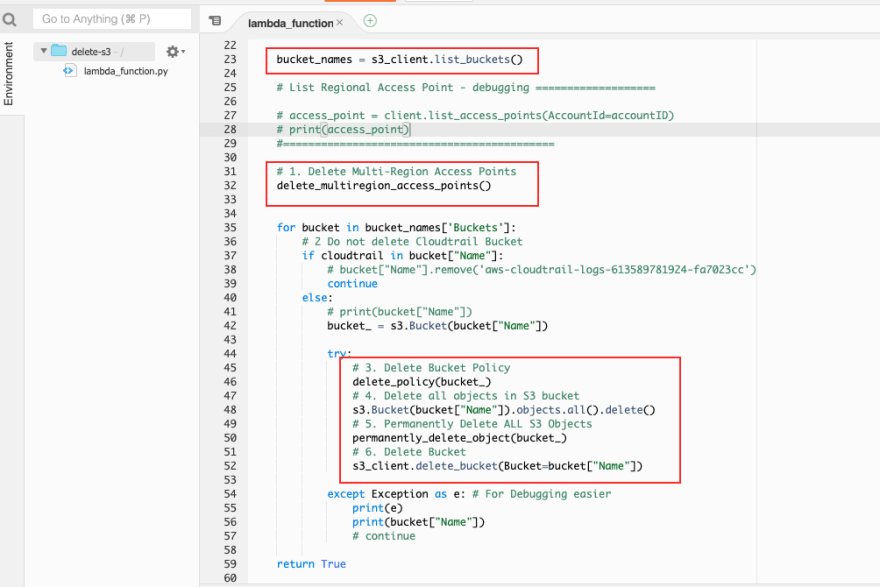
My colleague and I wrote a Lambda function using Python to do the following steps:
List all bucket names in all regions.
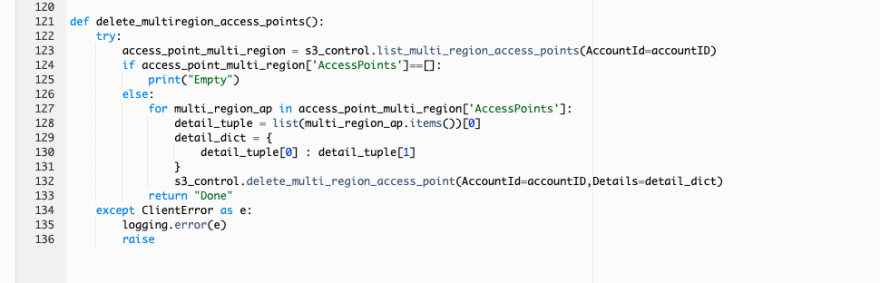
Delete all multi-region access points.
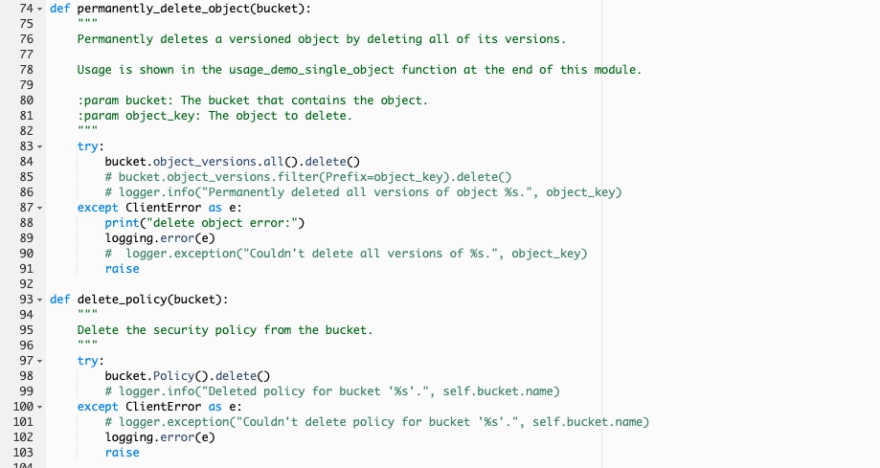
Delete other resources (bucket policy, objects) and then permanently delete S3 buckets except the bucket name including a string "cloudtrail".
P/s: Bucket name, which contains a string "cloudtrail", stores the CloudTrail logs for our security audit. So, do not delete this bucket.
For source code reference, you can refer to this repository.
3. Conclusion
In this post, I showed a method that automatically delete all existing S3 buckets in all AWS regions in a specific schedule. Thanks @natsu08122 for your source code contribution. I hope this blog will be helpful for you. Should you have any question, feel free to leave your comment. Thank you for your reading!



Top comments (0)