Environment
Cloud
- CIDR : 172.31.0.0/16
- Public : X.X.X.X
On-Premise
- CIDR : 172.16.0.0/16
- Public : Y.Y.Y.Y
# How To
## Part of AWS
- Create Customer Gateway (CGW)
#### Create CGW
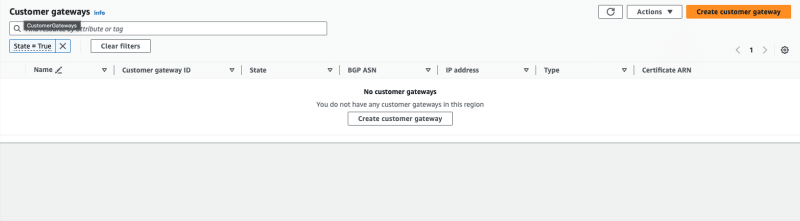
Enter Name tag, GP ASN, Certificate ARN
- Create Virtual Private Gateway (VGW)
#### Create VGW

Enter The Name, And Choice ASN


Attach VPC

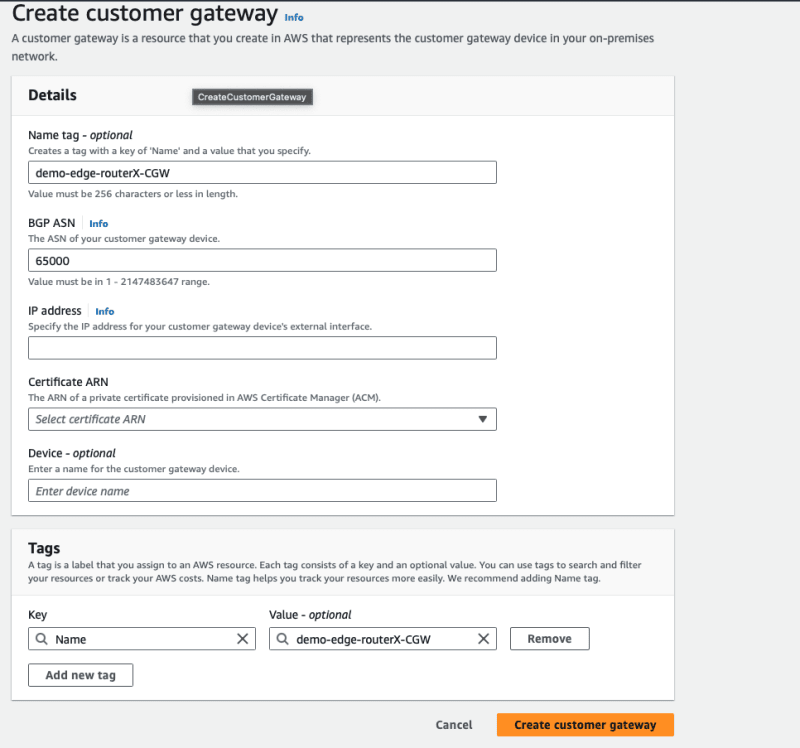
Enter, Choice VPN Tunnel Information

Enter Tunnel Options
After Create Then Wait

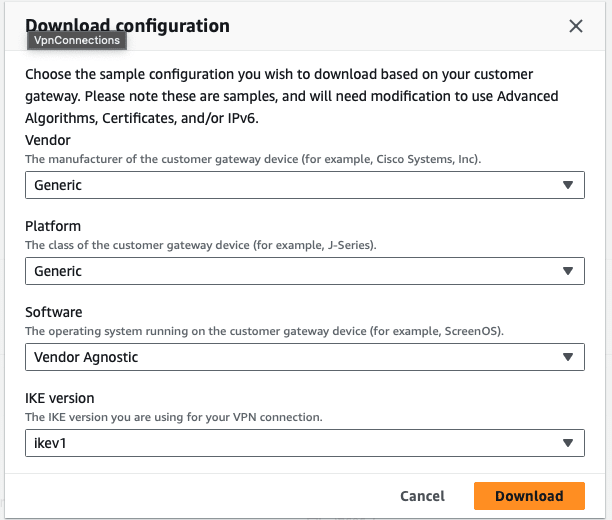
Download Conf If Needed
Part of Edge Router X
ssh adm@fw
# Conf mode
configure
# Enable the auto-firewall-nat-exclude feature which automatically creates the IPsec firewall/NAT policies in the firewall.iptables
set vpn ipsec auto-firewall-nat-exclude enable
# Create the IKE / Phase 1 (P1) Security Associations (SAs) and enable Dead Peer Detection (DPD).
set vpn ipsec ike-group FOO0 key-exchange ikev1
set vpn ipsec ike-group FOO0 lifetime 28800
set vpn ipsec ike-group FOO0 proposal 1 dh-group 2
set vpn ipsec ike-group FOO0 proposal 1 encryption aes128
set vpn ipsec ike-group FOO0 proposal 1 hash sha1
set vpn ipsec ike-group FOO0 dead-peer-detection action restart
set vpn ipsec ike-group FOO0 dead-peer-detection interval 15
set vpn ipsec ike-group FOO0 dead-peer-detection timeout 30
# Create the ESP / Phase 2 (P2) SAs and enable Perfect Forward Secrecy (PFS)
set vpn ipsec esp-group FOO0 lifetime 3600
set vpn ipsec esp-group FOO0 pfs enable
set vpn ipsec esp-group FOO0 proposal 1 encryption aes128
set vpn ipsec esp-group FOO0 proposal 1 hash sha1
# Define the first AWS peer address
set vpn ipsec site-to-site peer <VGW_IP> authentication mode pre-shared-secret
set vpn ipsec site-to-site peer <VGW_IP> authentication pre-shared-secret <Secret_From_Download_File>
set vpn ipsec site-to-site peer <VGW_IP> connection-type initiate
set vpn ipsec site-to-site peer <VGW_IP> description ipsec-aws
set vpn ipsec site-to-site peer <VGW_IP> local-address <Your_Pub_IP>
# Link the SAs created above to the first AWS peer and bind the VPN to a virtual tunnel interface (vti0).
set vpn ipsec site-to-site peer 192.0.2.1 ike-group FOO0
set vpn ipsec site-to-site peer 192.0.2.1 vti bind vti0
set vpn ipsec site-to-site peer 192.0.2.1 vti esp-group FOO0
# Configure the RFC 3927 IP addresses on the virtual tunnel interfaces
set interfaces vti vti0 address 169.254.x.x/30
# Lower the TCP Maximum Segment Size (MSS) on the vti interfaces to 1379.
set firewall options mss-clamp interface-type vti
set firewall options mss-clamp mss 1379
# Set route table
set protocols static interface-route 172.31.0.0/16 next-hop-interface vti0
# Apply conf & save conf
commit ; save
# Verify ike
show vpn ipsec ike-group FOO0
dead-peer-detection {
action restart
interval 15
timeout 30
}
ikev2-reauth no
key-exchange ikev1
lifetime 28800
proposal 1 {
dh-group 2
encryption aes128
hash sha1
# Verify esp
show vpn ipsec esp-group FOO0
compression disable
lifetime 3600
mode tunnel
pfs enable
proposal 1 {
encryption aes128
hash sha1
}
# Verify ipsec
show vpn ipsec site-to-site peer
peer <AWS_VGW_IP> {
authentication {
mode pre-shared-secret
pre-shared-secret <AWS_Secret>
}
connection-type initiate
description ipsec-AWS
ike-group FOO0
local-address <Local_Pub_IP>
vti {
bind vti0
esp-group FOO0
}
}
Wait To Tunnel Up

Verify





















Top comments (0)