NoSQL Injection Attacks
NoSQL databases, by virtue of their flexible schema and JSON-like data structures, often give a deceptive perception of being more secure against injection attacks. This is a grave misconception. A detailed post on Guided Hacking delves into the mechanics of NoSQL Injection Attacks. The underlying premise is that unlike SQL, which has a standard query language susceptible to SQL injection, NoSQL databases use a variety of query languages. Therefore, NoSQL injection attacks require a more nuanced approach. For instance, attackers might exploit the $ne operator in MongoDB to create queries that return more data than intended. The takeaway here is that NoSQL databases have their own unique set of vulnerabilities that deserve equal, if not more, scrutiny.

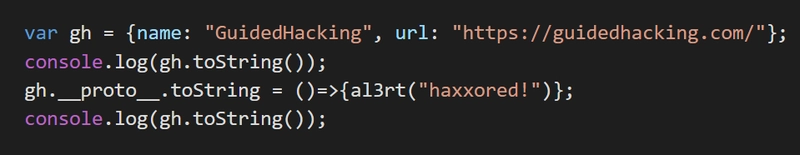
Prototype Pollution Attacks
JavaScript, being the omnipresent client-side scripting language, has a unique attack vector known as "Prototype Pollution." It's a fascinating exploit, where an attacker can manipulate the prototype properties of JavaScript objects. What makes it insidious is that it allows properties to be added to object prototypes globally. This leads to unexpected behavior, and in the worst case, can even lead to remote code execution. A thoroughly researched article on Prototype Pollution Attacks reveals the nuances and methodologies for exploiting this quirk. Understanding this attack can be crucial if you're working on a JavaScript-heavy project, as the exploit's potential consequences are far-reaching.
Type Juggling Vulnerabilities
PHP, a language that powers a significant portion of the web, is notorious for its type juggling vulnerabilities. This odd feature of the language can be manipulated to allow unauthorized access or data manipulation. Specifically, if a comparison operator is misused, it may result in unexpected type coercion. This may lead to logical bugs that can be exploited in various contexts, including authorization checks. To delve deep into this vulnerability, the article on Exploiting Type Juggling Vulnerabilities in PHP is a quintessential resource. It covers potential pitfalls and best practices to avoid falling into this trap, making it indispensable for anyone engaged in PHP development.
PHP Deserialization Attacks
Continuing on the topic of PHP, another intriguing vulnerability is related to object deserialization. PHP's unserialize() function can instantiate an object and execute its methods automatically. However, this convenience comes at a cost: a well-crafted payload can be used to execute arbitrary code. In essence, the attacker manipulates serialized data to exploit vulnerabilities in the PHP code. An in-depth tutorial on PHP Deserialization Attacks demonstrates the practicality and the severity of this issue. What makes this particular post invaluable is its focus on the application of these attacks in a real-world context.
Software Vulnerabilities will never go away
The rapid proliferation of diverse technologies has led to the rise of increasingly sophisticated attack vectors. Consequently, it becomes indispensable for software engineers to stay informed and vigilant about potential vulnerabilities. While one might be tempted to confine such concerns to the domain of cybersecurity professionals, the reality is that it's the collective responsibility of the development ecosystem. A solid grasp of potential vulnerabilities at the software engineering level can significantly mitigate risks, streamline debugging, and improve overall code quality.




Top comments (0)