CapitalOne was recently victim to a leak that may have affected 100 million individuals in the US. This post will not go into the unethical intent of the accused or the affect of private information being leaked, but rather the technical aspects and securing your AWS environment. If you'd like to read into it further, this document does a fair job at explaining it.
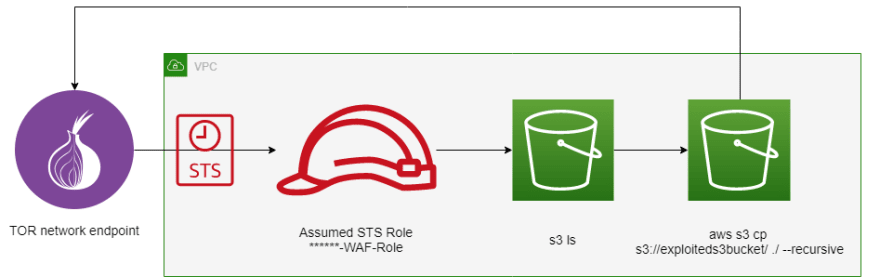
The diagram below is my understanding of how the CapitalOne S3 data was compromised. Background information about the accused also states that she worked for Amazon Web Services from 2015-2016 in the S3 division. Knowing that she worked for Amazon Web Services for a period of time very well may have affected her ability to compromise CapitalOne.
There seems to be still unanswered questions, such as:
- What credentials were exploited for the accused to assume the STS role to gain access?
- Why wasn't AWS GuardDuty's trusted list being maintained?
- Why was the STS role that was assumed allowed access to the S3 bucket? A strict bucket policy with allowed ARN's should've been used.
What is your opinion on the technical aspect of the exploitation and securing an AWS environment?


Top comments (0)