Introduction
Traditional security cannot keep pace with DevOps’s lightning-fast software development cycles. Organisations need to inject continuous security and automated testing throughout the software development process to improve security. Secure DevOps—that is, DevSecOps—is about making security central to development and operations. Building security into every stage of the software pipeline fills long-standing gaps between IT and Security. DevSecOps approach helps spot software security issues faster and alleviates security bottlenecks. And, it preserves the rapid development pace that DevOps makes possible. This post will show you how to do implement DevSecOps CI/CD using AWS CodePipeline.
Before DevSecOps
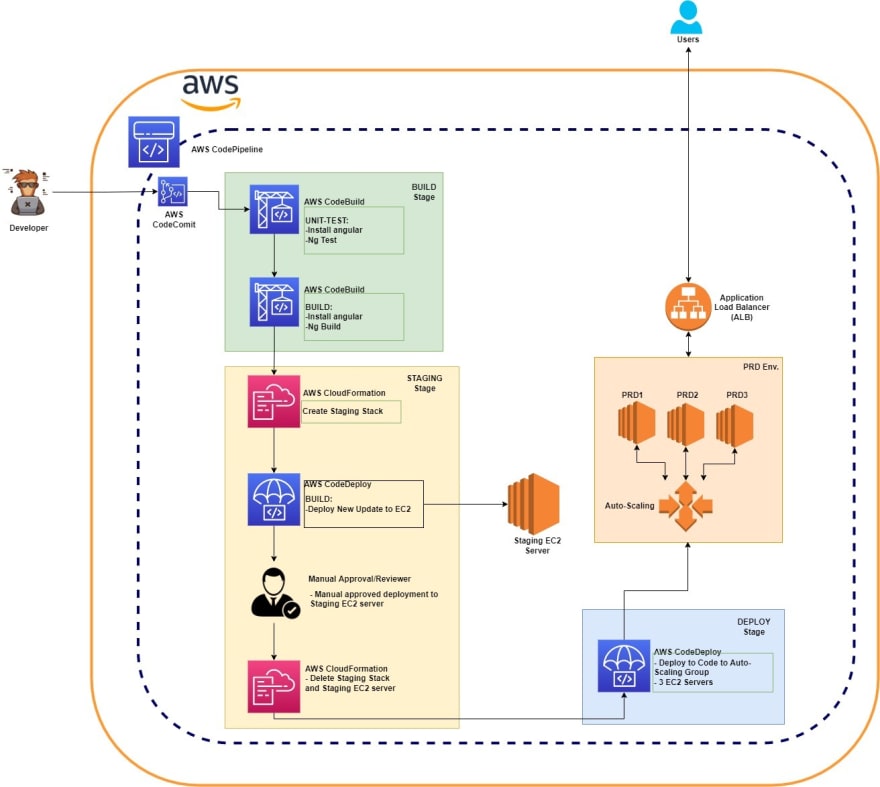
Above is normal Angular website which the flow like below:
- Developer/Programmer wil commit the new updated code to AWS CodeCommit Repository.
-
AWS CodePipeline **automatic triggered from the CodeCommit updated code in **SOURCE stage below:
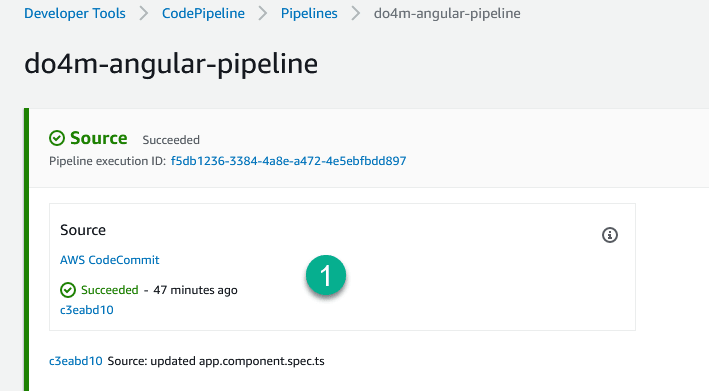
- Then it's goes to BUILD stage started the Unit-Test action group using "ng-test" command from "unit-test-buildspec.yml" file we set.
- Then it goes to Build process by using "ng-build" via buildspec.yml file we set.

- We have dynamic Staging EC2 server by using AWS CloudFormation which we only provision Staging server whenever we have new updated code.
- Once we provisioned Staging server then we deploy to EC2 server. We also passed CodeDeploy parameter which new Staging URL for manual approval or reviewer to evaluate our staging environment/server.
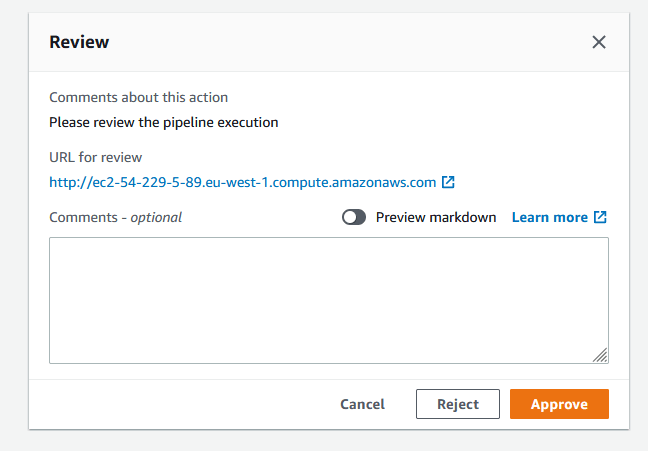
- Once the Approver approved and reviewed our Staging environment, we will delete our Staging CloudFormation Stack.
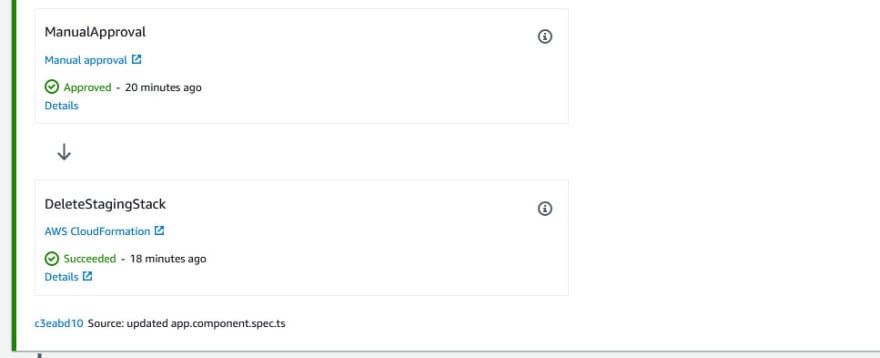
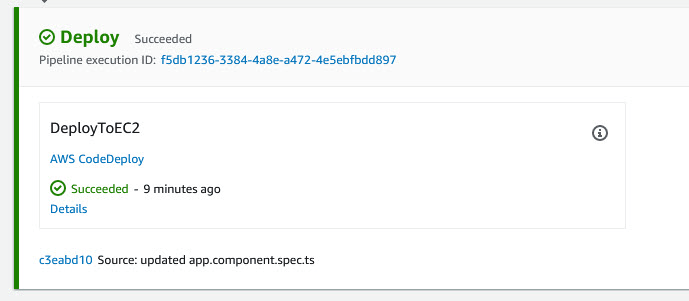
- Lastly, we deploy to Production environment which we using AWS CodeDeploy
*From DevOps to DevSecOps *
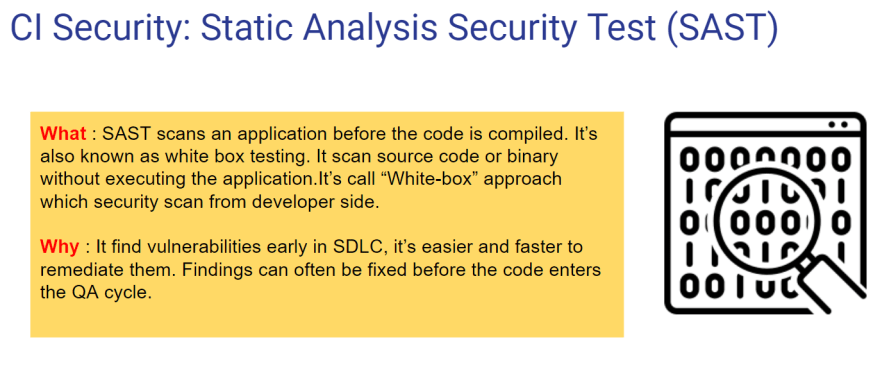
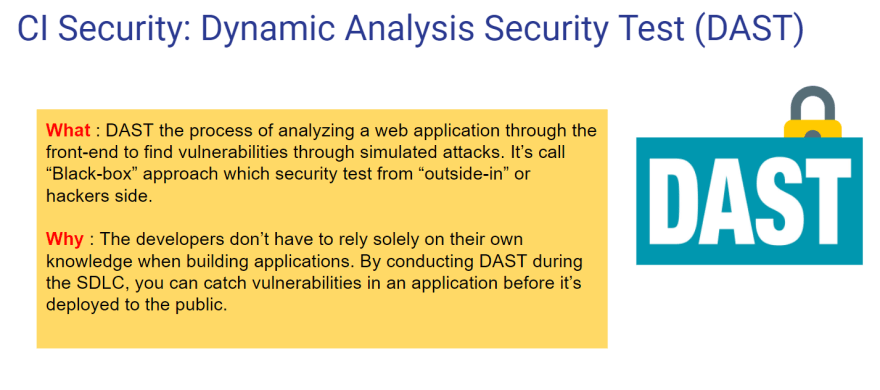
Now we can introduce the DevSecOps tools to use "Shift-Left" approach which added security scanner in BUILD, STAGING and PRD stage like below.
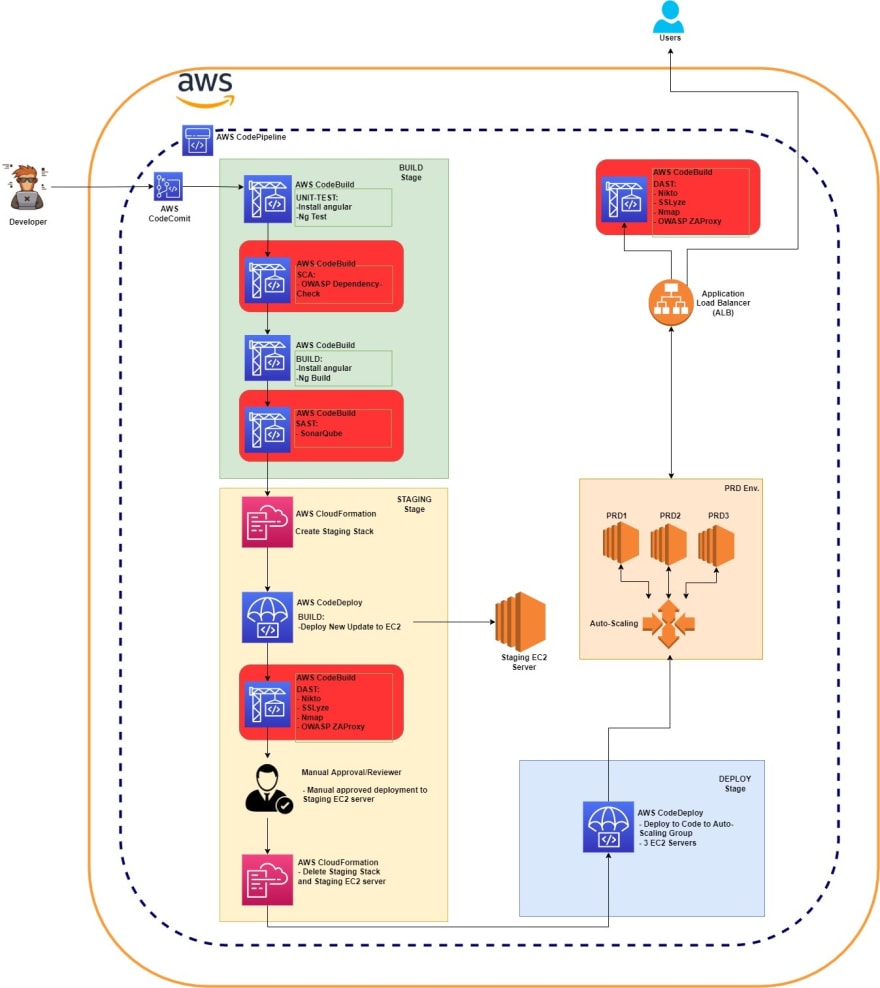
How to optimize your DevSecOps Pipeline
- Everyone should understand failures quickly
- CI job output with key messages
- Use colored error messages with emojis ✅
- Hint and link troubleshooting docs
- Always use exactly the same environment
- A CI/CD pipeline can’t be reliable if a pipeline run modifies the next pipeline’s environment.
Each workflow should start from the same, clean, and isolated environment.
Document the pipeline design
In your repository use Markdown docs to describe what you do on your CI/CD pipeline.
You also can use Wiki Page or Confluence to make everyone in the team know better about CI/CD process.
Communication
Human communication, collaboration, and teamwork are examples of factors that do not rely on automation.
In the absence of these three factors, success will be extremely hard to achieve.
It's crucial to optimize communication and transparency in your CI/CD pipeline workflow if you want it to succeed.
Conclusion
- Shift-Left + DevSecOps I think that everyone in the organization must make an effort to "Shift-Left" to a DevSecOps culture or methodologies and come up with a multidisciplinary security team.
- Agile + DevSecOps DevSecOps must be fed by Agile software development. Security user stories must be part of each sprint.
- Automation is the key Security and test automation can reduce delivery time, improve quality and security, and eliminate human error



Latest comments (0)