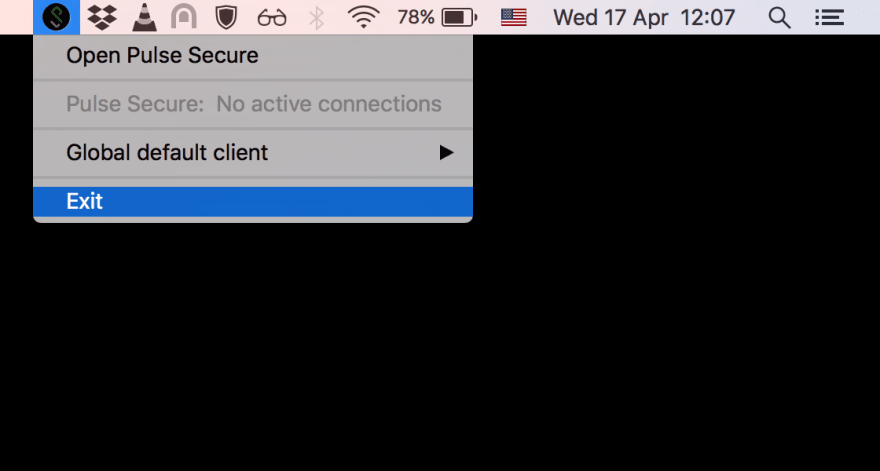
I got a new corporate VPN tool the other day. It's called Pulse Secure. It worked fine, thank you very much, no complains there. But then I tried to quit
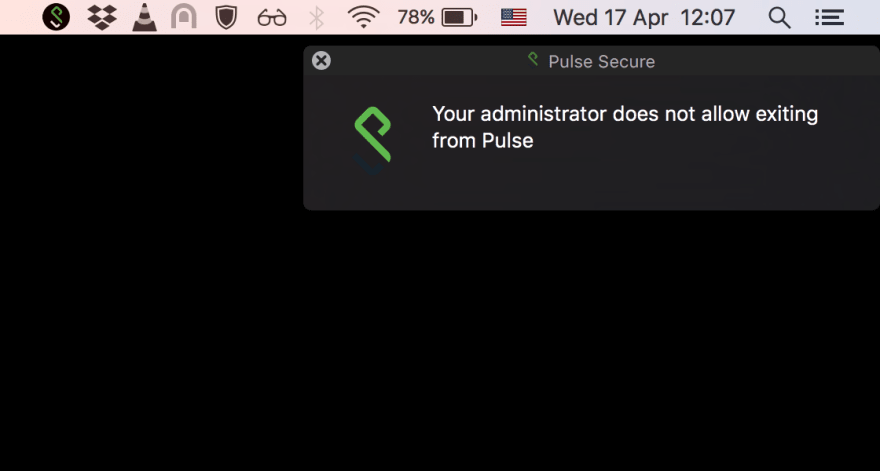
and I got this
That pissed me off right then and there. Why would any remote admin tell me what to do on my local machine? Even if it's a company machine. When I do not use the VPN or maybe I'm not even connected to any WiFi, why should I have this running? It's just silly to try to prevent me from doing something on the machine where I have the root access. When this gets pushed onto a developer's laptop (as opposed to an accountant or an HR clerk) it simply becomes a challenge.
It has no impact on the security of the machine or the corporate network when it's simply running in the background. This is not anti-virus software. It has an impact on the battery life and other resources like RAM and CPU though. And I need those. It's exactly this type of programs that don't exit, hang around and prevent me from running yet another Electron app on my laptop. Sometimes one is not enough, you know.
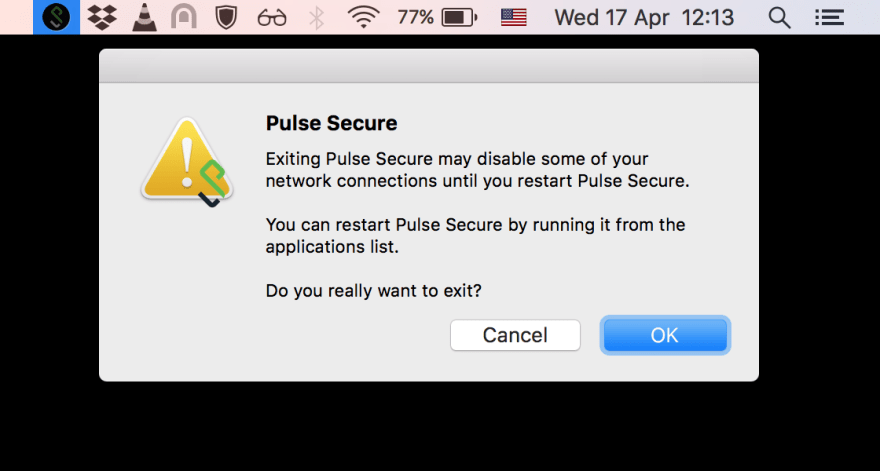
I guess I'd have to get my hands dirty instead of doing something I was actually going to do. Simply killing it from the command line didn't work. It just starts over. Investigation it is, then.
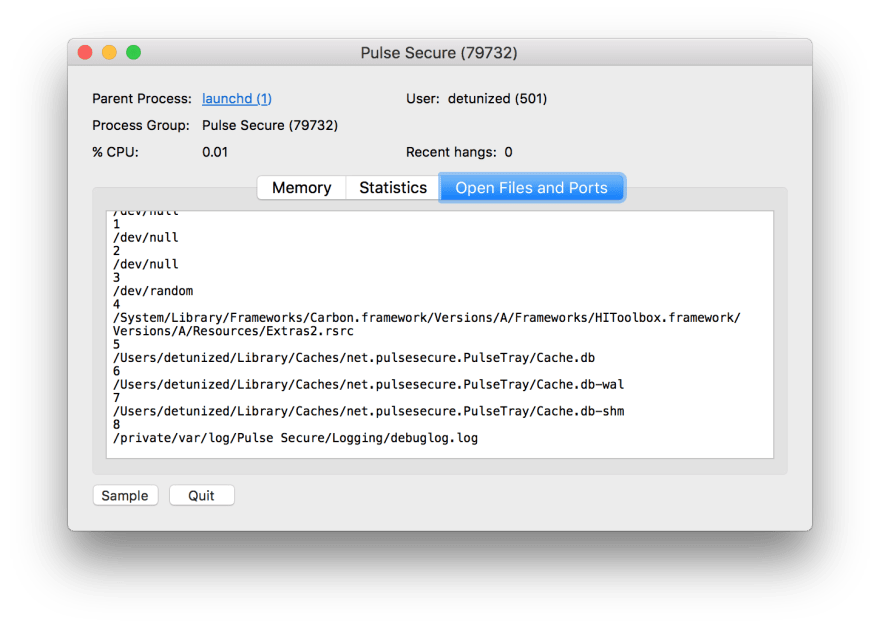
First, I took a quick look at the list of the open files from the Activity Monitor. There I found a log file (bottom row):
The tool developers were very kind and dumped about half a meg of stuff on every restart cycle into the log. So it's wasting my disk space as well then. Amongst thousands of lines, I found a reference to /Library/Application Support/Pulse Secure/Pulse/connstore.dat. It sounded promising. After poking around in that file and trying this and that, I found a parameter that is responsible for that.
ive "921sn438-qoo8-4pp4-85p7-68q5s2592o32" {
...
connection-policy-override: "false"
...
}
When this parameter is changed to true and the tool is restarted I was able to quit. Voilà!
Yes, I do.
And here the script that automates the whole thing:
cd '/Library/Application Support/Pulse Secure/Pulse'
sudo sed -i '' \
s'/connection-policy-override: "false"/connection-policy-override: "true"/' \
connstore.dat
sudo killall PulseTray 'Pulse Secure' dsAccessService
Dear developers and sysadmins, please don't do that again. You're just wasting everybody's time. Rather put your efforts into making the software more reliable, less resource hungry, more secure.
Originally published on detunized.net



Top comments (9)
I wish my company would agree on this, but they will never.
We also have Websense and we all HATE it. It caused lots of serious trouble to all the developers in my company (lately they force-installed a google chrome extension for it, but I figured out how to delete it :D).
Thx a lot ! I m feeling less alone !
I will bring your story to my sysadmin
I hope it works. From my experience, though, sysadmins are pretty stubborn people. Wish you luck. Or you could just patch the config file.
Thanks for your reply. I'm going to talk to the admins about this. TBH I don't expect a quick resolution here. Our company is quite large and these things take a while usually.
Some comments may only be visible to logged-in visitors. Sign in to view all comments.