We are pleased to announce the general availability of ThreatMapper 1.3.0! Highlights from this latest release include:
- Secret scanning at runtime
- Runtime Software Bill of Materials (runtime SBOM)
- A new approach to vulnerability scanning
- Enhanced Attack Path Visualizations
Continue reading to learn all about the new features and how to get started.
Key Features in TheatMapper 1.3.0
Scan for Secrets in Production
In this release, we’ve integrated the open source project called SecretScanner into ThreatMapper so that now you can scan for both vulnerabilities and secrets in production, assess the risks associated across all potential issues, and then prioritize remediation accordingly.
With ThreatMapper, you can scan filesystems and container images looking for over 140 different secret types, including unprotected keys, tokens, and passwords. With this new capability, you will get a complete list of all sensitive secrets in your production environment, including those missed by traditional shift left scans performed during development. This is important because pre-production scans aren’t able to find secrets in host operating systems and third-party containers powering your applications in production, or legacy workloads created before your shift left measures were in place:
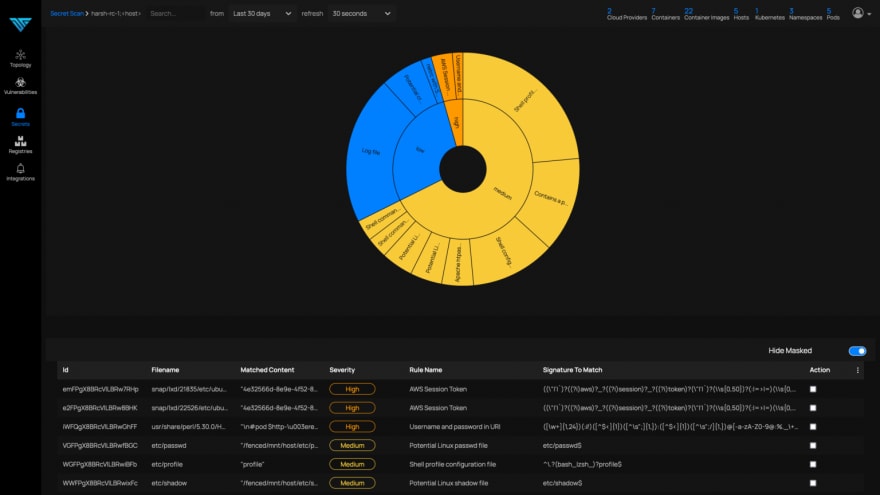 ThreatMapper 1.3 can identify more than 140 different secrets types
ThreatMapper 1.3 can identify more than 140 different secrets types
The integration of SecretScanner into ThreatMapper provides better defense against sophisticated multi-stage attacks. After an initial exploit, attackers seek ways to spread laterally and gain control of more hosts and workloads before reaching their final target. Sensitive secrets, like encryption keys, authentication tokens, or passwords, offer attackers ways to move laterally once they’re in.
While no one purposely hands over the proverbial keys to the castle, secrets sometimes make their way into production. Developers might use temporary secrets to generate build processes, but then forget to delete them after the image is built. Or, they might unknowingly apply weak security policies that embed overly permissive authentication tokens. It’s also common for workloads to acquire secrets dynamically when they are in production. Regardless of how they got there, it’s essential to find and fix sensitive secrets that make it into your production environments.
 A full explanation of each result allows you to determine if it is a false positive (as in this case), or an issue that requires remediation
A full explanation of each result allows you to determine if it is a false positive (as in this case), or an issue that requires remediation
Generate a Runtime SBOM
Maintaining SBOMs for running applications and infrastructure is key to securing the software supply chain through increased transparency and information sharing. Standards and tooling are emerging that can process SBOM data for a variety of purposes. However, as we well know, not all runtime assets go through a formal CI process, so SBOM coverage is far from complete.
ThreatMapper 1.3.0 calculates runtime SBOMs for scanned workloads and makes these available for inspection through the UI and API. The runtime SBOM enumerates all of the packages and software items deployed in the workload, which may drift from the at-build-time SBOM. This new feature helps eliminate potential blindspots by identifying what goes into production and what changes during production. By tracking components and applying runtime context, the new runtime SBOM capability provides you with:
- Smaller and more actionable asset inventories
- More clearly defined attack surfaces to protect
- Another way to detect threats based on deviations from pre-production SBOMs
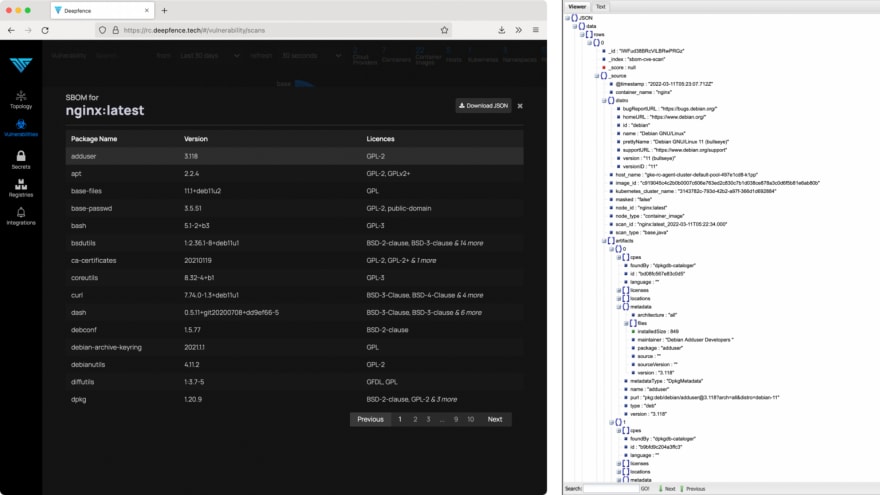 The runtime SBOM can be inspected or downloaded as a JSON document
The runtime SBOM can be inspected or downloaded as a JSON document
We’ll continue to build out the new runtime SBOM capabilities, working with emerging standards and tools and enhancing the static SBOMs with additional information that can only be obtained at runtime.
Experience New Vulnerability Scanning
Part of what enables ThreatMapper to generate runtime SBOMs is linked to a modification in how it scans running operating systems, applications, containers, and serverless workloads for vulnerable software components. In this release, we incorporated two new open source tools– Syft and Grype – into ThreatMapper. Although these are backend changes, they will open up new benefits for users, including:
- Support for additional host operating systems
- Faster initialization times, smaller data transfers from ThreatMapper’s lightweight sensors to the management console, and faster scanning to improve overall performance, particularly for large deployments
- Integrations with many CI tools and two user communities
See Enhanced Attack Path Visualizations
We’ve extended our signature Attack Path Visualizations in this release. ThreatMapper now provides you with additional context about the most vulnerable attack paths in your environment by specifying each path’s exposure to the internet.
By categorizing paths with direct and indirect internet exposure, ThreatMapper helps you narrow down from thousands of potential issues to a handful that need fixing immediately.
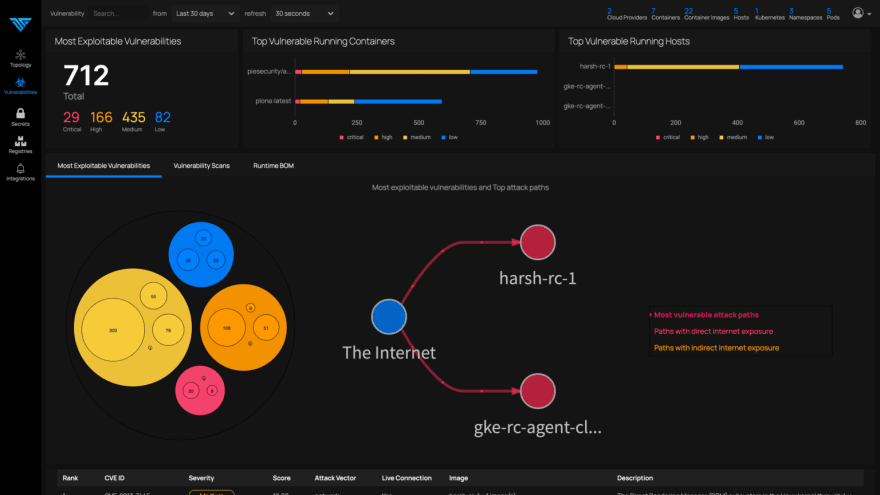 See attack paths with direct and indirect internet exposure
See attack paths with direct and indirect internet exposure
This enhancement provides visual context about the depth of visibility that ThreatMapper offers. It exposes the easier-to-find attack paths with direct internet exposure along with the hard to find paths further downstream, hidden behind proxies and exposed to potentially malicious traffic indirectly.
Get the Latest!
We hope you’re as excited as we are about all the latest updates and improvements to ThreatMapper! It is our intent that ThreatMapper becomes an open platform on which users and partners continue to build integrations and solutions. Check it out and let us know what you think.
- To install or upgrade to ThreatMapper 1.3.0, please refer to the detailed installation instructions.
- Share your feedback by joining us in the Deepfence Community Slack.
- Learn more in the upcoming webinar on March 29 at 10:00 AM PT.
Finally, a huge thank you goes out to our amazing community. Your ongoing feedback and contributions help us continue to shape ThreatMapper and unlock even more use cases.
...
Deepfence is dedicated to helping organizations secure their infrastructure and applications across the cloud native continuum. ThreatMapper open source scans, maps, and ranks vulnerabilities in running containers, images, hosts, and repositories. ThreatStryker elevates these capabilities by providing runtime attack analysis, threat assessment, and targeted protection.
Interested in learning more? Schedule a consultation with one of our security experts today.



Top comments (0)