Cybersecurity attacks only continue to increase and in 2021, supply chain attacks are expected to grow by 400% according to the report ENISA Threat Landscape for Supply Chain Attacks. Security minded companies are quickly making supply chain security a main focal point - but the software supply chain is still considered the weakest link by threat actors.
The increase is well in-line with how often we read about new ransomware and malware attacks. Just recently there were account takeovers on the popular packages ua-parser-js, coa and rc with a combined average of 30 million weekly downloads.
If your organization is exposed to a malicious version, a compromised system means anything would be possible for attackers - installing backdoors, crypto miners, keyloggers and extraction of data. All bad and increasingly public, causing substantial monetary and reputational loss. Don’t think that JavaScript/npm is unique in this regard - the same problems exist in other ecosystems like Maven, Nuget and Python.
One single bad dependency, out of the probably hundreds or even thousands of dependencies you are using, can put your whole business at risk. Failure to protect the supply chain is not an acceptable option.
Even though the metrics are not the most uplifting, the great news is that with proper supply chain security you can mitigate threats and protect your organization. Stop the lurking big fish before it’s too late!
This article will guide you through the difference between an insecure and secure supply chain setup to prevent supply chain attacks.
Why are supply chains so insecure?
With ecosystems like npm it’s so easy to get caught in the dependency trap using external code for everything - even when in some cases components are one-liners. The more dependencies you use, the higher is your inherited risk. And from an attacker’s perspective it’s the more the merrier - as you’ll have more risk exposure.
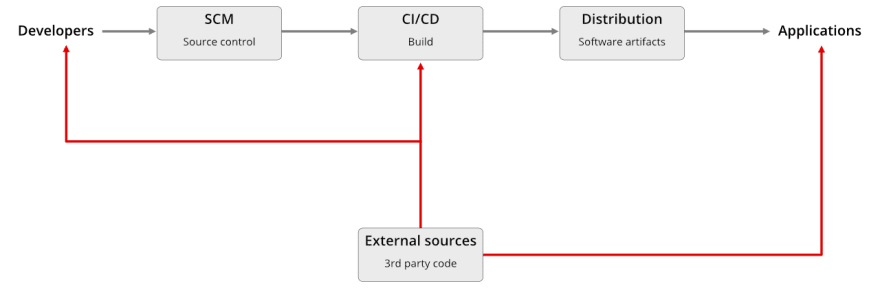
The reason why many organizations’ supply chains are considered insecure is the fact that Developers and CI/CD (build environments) have unfiltered access to the full universe of dependencies - directly from external sources.
If your development pipeline is similar to this, you should pay extra attention to this article. Don’t worry, you are not alone and reading this article is a great first step.
When developers and CI/CD are able to install components directly from external sources there are no safeguards to protect you from malicious versions or vulnerabilities.
Even though you benefit from rapid and creative development, you have no way of enforcing policies and controlling what dependencies are used in your organization. If you’re interested in reading up on the security risks related to the large dependencies trees, check out this article.
How to avoid “Oops, we’ve had a security breach”
Waking up and realizing that you’ve been compromised is a nightmare. And knowing it could’ve been prevented doesn’t help in afterthought. The fundamental thing to do is to adopt a secure software supply chain and protect your organization - now, before it’s too late.
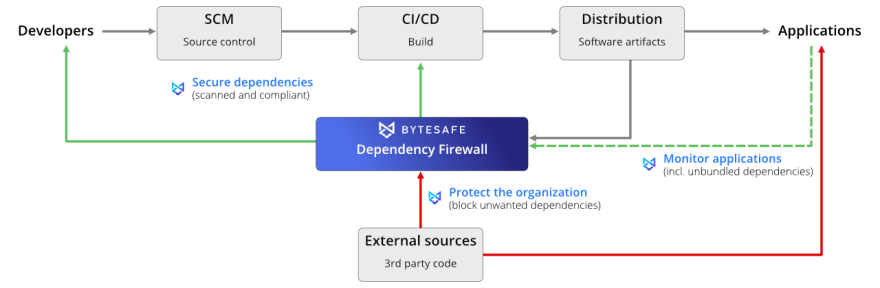
A secure software supply chain is about knowing what dependencies you’re using, keeping them secure and to be able to control workflows - across every developer workstation and automated environment within the organization. This includes an end-to-end security approach and enforcing the business policies you’ve decided at every step.
Steps to secure your supply chain
We fully recognize that for many companies security is a journey, and knowing where to best get started can be a difficult decision and a barrier to properly addressing issues.
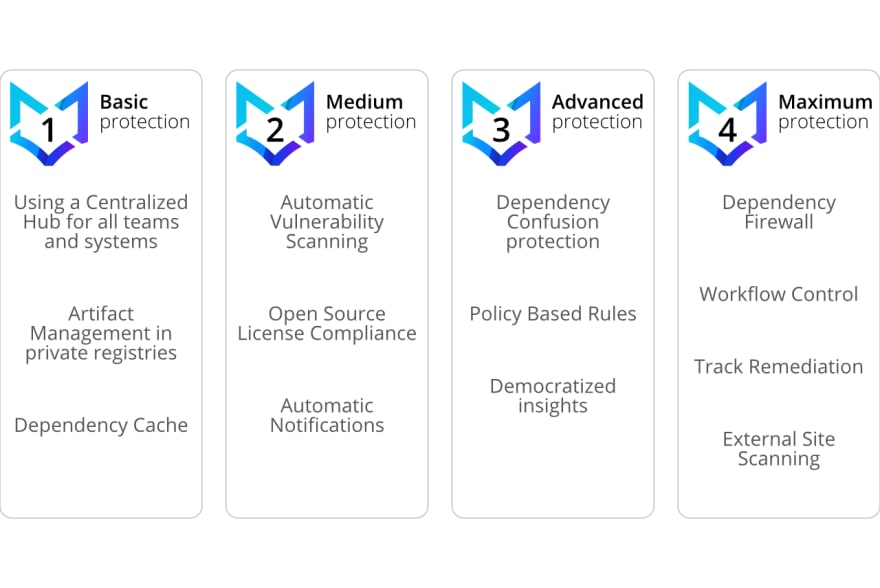
To help out, we’ve compiled a shortlist of security steps to take your organization from basic protection to the maximum protection of the full Bytesafe Dependency Firewall.
Basic - Protect your organization with a central dependency source
Make sure every piece of your supply chain is sourcing data from a centralized internal source that you have control over, with known and allowed components.
Remove direct links to unsecured dependency sources or else you run the risk of installing compromised and vulnerable dependencies.
Medium - Scan, identify and remediate issues
Identifying issues early, reduces risk exposure and also saves both time and money. Continuously monitor the dependencies in your supply chain for security and license compliance issues.
It’s important to use up to date and secure components, but patches should be applied intelligently and not instantly to avoid zero-day attacks.
Advanced - Protect and Block
Enforce your business policies. Set up policies to do the work for you and shift responsibility from individual-level to company-level.
Protect internal packages from attacks like Dependency Confusion.
Unifying everyone under the same level of protection (avoiding misconfiguration, which is a common source for attacks).
Maximum - Control workflows & verify deployed applications
When improving cybersecurity protection, maximum protection includes being able to control workflows, check components for security and compliance issues and to verify the actual deployed applications.
Bytesafe Dependency Firewall will automatically quarantine unwanted packages so that they will be isolated from use in your organization. Like a chain supply guard, Bytesafe won’t let your organization use the unwanted packages.
JavaScript dependencies are often bundled in your CI/CD environment, but dependencies can also be included in web applications using the <script> tag.
Checking what has actually been deployed to production is a necessity for end-to-end security and for maximum protection.
Be sure that you are able to freeze the universe and versions of dependencies you are using and that your registries/repositories you’re using can be adapted to your agile process - regardless if you have daily, sprint releases or monthly releases.
Thanks for reading!




Top comments (0)