Currently, IoT (Internet of Things) technology, which is beginning to change its terminology to IoE (Internet of Everything), is transforming the way companies manage their devices and sensorize their warehouses and offices. As for vehicle or fleet management, telematics systems have become an essential tool for monitoring and control.
To connect these vehicles, the general public is familiar with the possible hardware devices that, in some cases, are installed in the vehicles. It is even common for our vehicles to have apps with which we can control them.
The great unknown, in many cases, both for the public and for developers, is the communication protocol used.
What does this mean? It refers to how the telemetry device in our vehicle, for example, is able to travel and transmit the read information, and how we can view that information in the app on our smartphone or in a cloud service.
In this article, we will explain and explore the different features of the MQTT (Message Queuing Telemetry Transport) protocol, which is considered the communication protocol par excellence in telemetry applications in vehicles, IoT, IoE, and M2M.
We will also analyze why the use of MQTT optimizes IoT device communication compared to protocols such as Kafka, HTTP, HTTPS, or CoAP UDP.
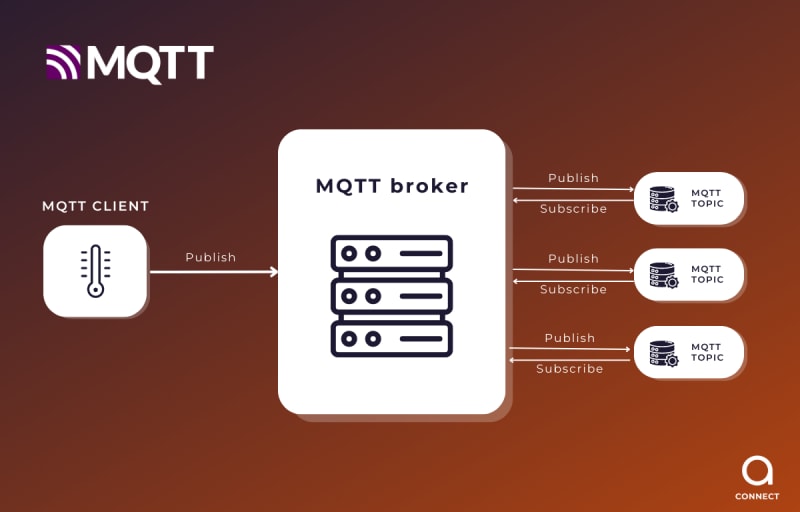
What is MQTT?
MQTT is an application layer communication protocol based on TCP/IP. It is used for communication between IoT devices and utilizes a publish/subscribe model, where devices subscribe to a topic and only receive relevant messages from their broker.
It was developed by Andy Stanford-Clark and Arlen Nipper in 1999 and designed for data transmission in network environments with limited bandwidth and resources, such as sensors and actuators.
Advantages of MQTT over other communication protocols:
MQTT vs Kafka
MQTT and Kafka are two popular technologies for IoT device communication. Although both are used for transmitting data between devices, there are some key differences between them.
MQTT is a lightweight and efficient messaging communication protocol designed specifically for IoT and M2M devices. It uses a publish/subscribe model, meaning that devices communicate by publishing messages to a channel (topic) and other devices can subscribe to that channel to receive the published messages.
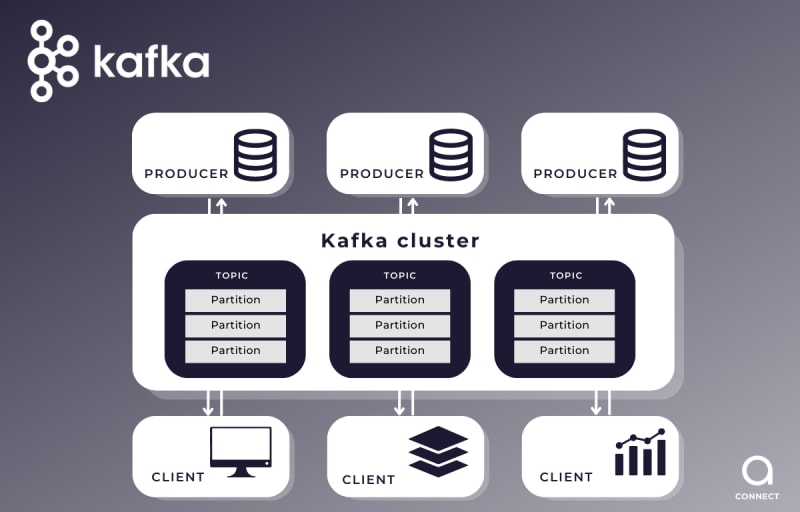
On the other hand, Kafka is a distributed messaging system used for the transmission of large volumes of data in real-time. It is an application layer communication protocol that uses TCP/IP and is used in high-performance environments.
Although Kafka is a solid solution for transmitting large volumes of data, there are several disadvantages compared to MQTT.
- Firstly, Kafka is more complex to implement and configure than MQTT. Kafka requires a cluster system, while MQTT can operate on a simple network architecture.
- Secondly, Kafka is not as efficient as MQTT in terms of network usage and IoT device power. Kafka continuously sends and receives data, whereas MQTT, with its subscription/publication model, only receives relevant messages for these devices.
- Thirdly, in some cases, MQTT is considered more scalable than Kafka due to its decentralized architecture, which allows multiple devices and brokers to connect. This increases the processing and message distribution capacity on the network.
As previously mentioned, MQTT uses a pub/sub model. This means that devices send messages through specific channels (topics) and other devices interested in those messages subscribe to those topics. This model allows for the connection of multiple devices and brokers, increasing message processing and distribution capacity in the network.
Moreover, MQTT is a lightweight and efficient messaging protocol that consumes very few resources and bandwidth. For this reason, it is ideal for IoT devices with limited resources.
On the other hand, Kafka is a distributed data streaming platform designed to handle large volumes of data in real-time. Kafka is based on a cluster architecture, consisting of a set of Kafka brokers that are distributed and scaled horizontally to handle large amounts of data. Kafka uses a publish/subscribe model similar to MQTT, but also allows for real-time data processing through the use of data streams and the event processing API.
Although Kafka is highly scalable and can handle large volumes of real-time data, its centralized architecture can present scalability limitations when using large clusters, as is often the case in IoT device and network use cases. Increasing the number of brokers can lead to network overload and reduce overall performance.
In brief, MQTT is a more suitable option for most IoT device use cases due to its specific characteristics, such as its light weight, scalability, ease of deployment and security. Although Kafka is a more powerful technology and can handle large volumes of data, in most IoT device use cases, MQTT is a better choice due to hardware limitations and the usual low cost of these devices.
MQTT vs HTTP/HTTPS
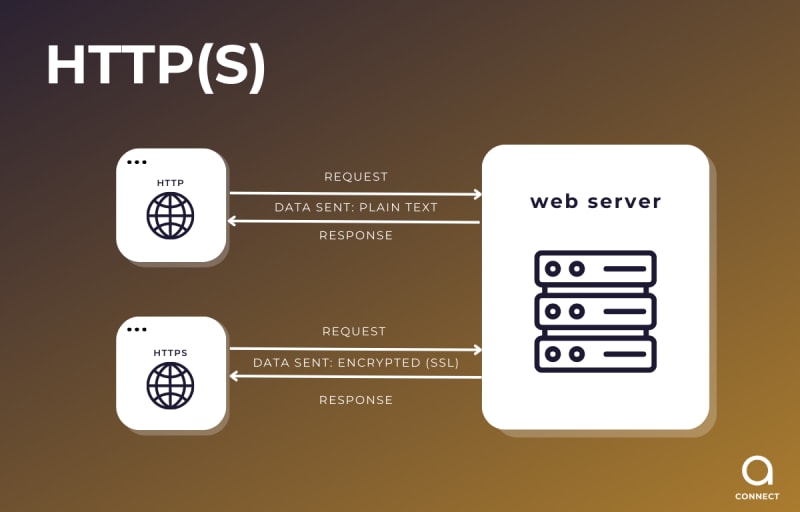
HTTP/HTTPS (Hypertext Transfer Protocol/Secure Hypertext Transfer Protocol) are communication protocols used in IoT applications, but they have some key differences compared to MQTT in terms of performance and functionality.
- HTTP/HTTPS is a web-based communication protocol designed to transmit data over the World Wide Web. It is commonly used in web and mobile applications and can be used in IoT applications to send and receive data. HTTP/HTTPS uses a request-response model, meaning devices send data at regular intervals, regardless of whether there are changes in the data.
- HTTP and HTTPS are more suitable for data transmission over the web, while MQTT is more suitable for real-time data transmission between IoT devices. Therefore, in M2M or IoT device use cases, MQTT is a much more energy-efficient protocol.
- In terms of scalability, HTTP and HTTPS are less scalable than MQTT. HTTP and HTTPS are designed for data exchange over the web and are not optimized for real-time data transmission between IoT devices.
- On the other hand, something we haven't mentioned before is that MQTT is a highly reliable protocol. It is capable of handling unstable connections and data losses, making it a very fault-tolerant option.
MQTT vs CoAp UDP
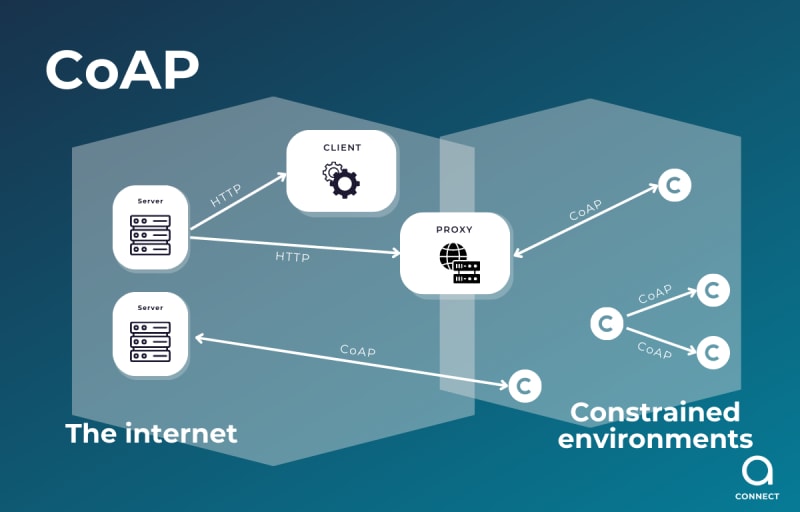
CoAP (Constrained Application Protocol) is a communication protocol widely used in IoT products. It works over the UDP layer.
Comparing it with MQTT, we can observe certain differences:
- MQTT is a much more efficient protocol than CoAP in terms of energy consumption. MQTT uses a subscription/publication model, which means that devices only communicate when new data is available. On the other hand, CoAP uses a request/response model, which means that devices have to constantly communicate to check if new data is available.
- MQTT is highly scalable thanks to its subscription/publication model. This means that devices can send data to many subscribers simultaneously, which is ideal for applications that require multiple devices to participate.
- MQTT is a more flexible protocol than CoAP. For example, MQTT supports multiple Quality of Service (QoS) levels, allowing devices to control the number of acknowledgements they wish to receive. In this way, we can also flexibly configure their power consumption.
- MQTT offers more advanced security features than CoAP, such as end-to-end encryption and device authentication. It supports Transport Layer Security (TLS), which provides end-to-end encryption and ensures that data cannot be intercepted or tampered with.
Telemetry, MQTT and Security
Security is a major concern in any vehicle telemetry system or IoT device. These systems collect and transmit sensitive data, such as vehicle location and driving data. MQTT is a secure protocol that can be used with different levels of security, such as authentication and encryption.
In MQTT, there are different encryption methods that can be used to ensure the privacy and security of the transmitted data. The most common encryption methods in MQTT are described below:
- TLS (Transport Layer Security) is a security protocol used to protect the connection between MQTT clients and brokers. TLS uses symmetric and asymmetric encryption to ensure that the data transmitted between clients and brokers is private and secure. To use TLS, it is necessary to configure certificates and encryption keys on both the broker and MQTT clients.
- SSL (Secure Sockets Layer) is a security protocol similar to TLS and is used to protect the connection between MQTT clients and brokers. SSL also uses symmetric and asymmetric encryption to ensure the privacy and security of transmitted data. However, SSL is considered obsolete and has been replaced by TLS.
- Certificate-based authentication is an encryption method that uses digital certificates to authenticate and authorize MQTT clients. These digital certificates serve to verify the identity of both the client and the MQTT broker before allowing connection and data exchange.
- Username and password-based authentication is an encryption method that uses authentication credentials to allow access to MQTT clients. Clients must provide a username and password to connect to the MQTT broker and access transmitted data.
It is important to note that the choice of encryption method in MQTT will depend on the specific security and privacy requirements of each application, as well as the hardware used.
Hardware limits the ability of devices to perform encryption and decryption operations due to resource limitations, especially in IoT devices with limited resources such as connected vehicles.
With less processing power and memory, IoT devices may struggle to perform the encryption and decryption operations necessary to secure MQTT communication. Therefore, appropriate encryption methods compatible with the device's limited resources should be selected.
One way to reduce the load on hardware is to select less resource-intensive encryption methods, such as symmetric encryption instead of asymmetric encryption. Both TLS and SSL use both types of encryption, and while they offer a high level of security, they can be cumbersome for resource-constrained devices.
Another method to reduce the load on hardware is to use end-to-end encryption instead of encryption at the broker. End-to-end encryption means that data is encrypted at the sending device and decrypted at the receiving device, eliminating the need for the broker to perform encryption and decryption operations.
In summary, resource constraints on IoT devices imply the need to carefully select the encryption methods used in MQTT. It is important to consider both security and compatibility with the limited device resources. The security of MQTT communication should not be compromised due to lack of resources, so appropriate measures should be taken to protect the privacy and security of data transmitted on IoT devices.
MQTT & mobility communications
MQTT's ability to connect and communicate devices efficiently has led to smarter vehicle fleet management. Through its publish/subscribe model, MQTT enables vehicles and related devices to transmit and receive relevant data in real time. This has driven the implementation of mobile applications that facilitate vehicle monitoring and control from the convenience of a smartphone. From astara Connect we offer this data for any developer who has in mind to develop a mobility APP, always using the most optimized protocols for each case.
It is interesting to note that MQTT has been widely adopted in the mobility sector due to its technical advantages compared to other protocols. MQTT stands out for its efficiency, scalability and ease of implementation as we have discussed above, which makes it especially suitable for a mobility telemetry system such as astara's with which we ensure that the scalability and volume of data are safe in a system like this.
MQTT has been a key catalyst in the evolution of mobility for people and vehicles, providing a solid and secure technological infrastructure for the effective management and control of fleets in real time. At astara Connect we are developing a telemetry system based on MQTT. Its efficiency, scalability and focus on security allow us to enhance the user experience, making mobility smarter and more connected than ever before. As technology continues to advance, MQTT will continue to play a crucial role in transforming the mobility and driving landscape, facilitating a more efficient and safer future for all. And we will provide much-needed data, always using protocols that ensure the privacy and security of Connect users' data as MQTT does.
In short, in IoT applications with a large volume of devices, we can only say:
we love MQTT!



Top comments (0)