One of the principal actions over the internet is authentication. Authentication, not to be mistaken for authorization, is the process an application goes through to confirm that a supposed user is actually who they claim they are.
Basic authentication (pun?) involves the user providing a combination of username and password. Sometimes email address is used in place of username. These username/email and password combination are provided during signup.
If a user ever forgot their username or password, a way to get them back into their account is to confirm if the user have access to the associated email address.
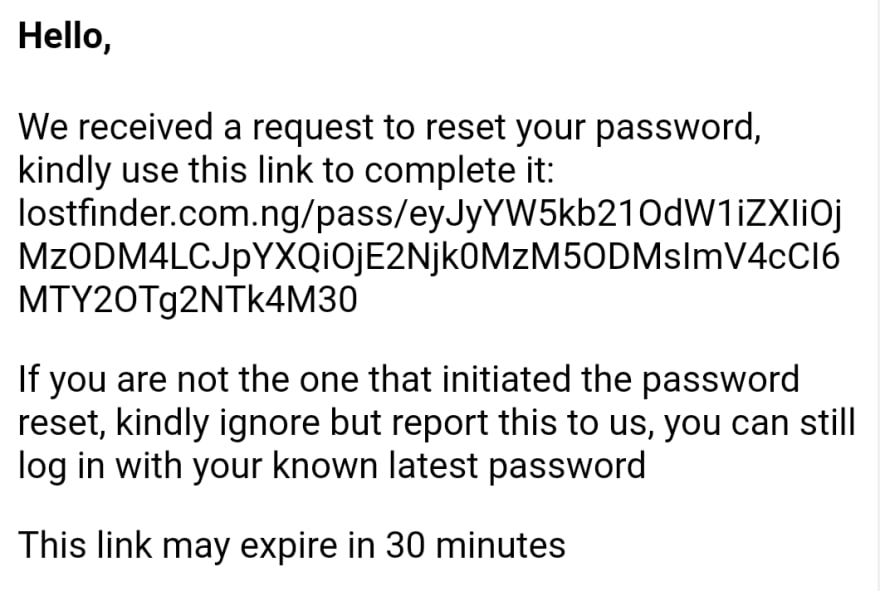
To do this some platforms send a reset link to the email, expecting the user to click and thereby get confirmed to be the legitimate account owner and thereby allowed to reset the password.
Another way is that OTP is sent to the email address and the user is expected to enter it correctly into a form on the platform.
I have built solutions that employ both methods and from my experience with web security and vulnerabilities I will say OTP is the better option. Why?
With reset links some email clients will not make it clickable by default, leaving your users stranded but for a few that understand that they can copy it.
Unless there's a kind of that has to be performed on the page the link directs to, then we cannot be so sure of who clicked, and why it was clicked - it might be a wrong email and the receiver mistakenly pressed the link from mailbox.
Receivers of link are susceptible to being phished, and some conscious users would be reluctant to click.
OTPs are discrete, they cannot be broken like links, and the platform can be so sure that the verification was accurate to the tune of 98%>
Which one do you prefer?


Top comments (2)
Personally, I prefer clicking on a link, it's just more comfortable. I'm always annoyed to retype numbers in classic 2FA. Or even better: "no password at all" ;)
That said, it's funny how you distinguish between links with looooonnng codes and OTP codes with a handful of digits. Basically, they are the same. You could even write mails with both, like:
Click here: direct-link?code=123456
Or type 123456 on the confirmation page.
The thing is, from a security point of view, short codes are weaker. You have one in a million change to guess it right for 6 digits! ...now, this might not sound like a lot, but for machines which can send thousands of requests per minute, it's another deal. In other words, you will have to pay more attention on the server side to prevent attacks like brute forcing (trying lots of code for an account) or spraying (trying a few codes for lots of account).
On the other hand, "long codes" are virtually impossible to hack which prevents the previously mentionned attacks and puts you automatically on the safe side.
That's also why short codes are typically not sent per e-mail, because they are vulnerable. They are typically only sent in the "secondary" authentication in 2FA, once the first e-mail check or password check has been verified, not before since this would make them vulnerable to "mass guessing".
This is insightful. Thanks for the contribution.