Passkeys are a big step towards a passwordless future.
Allowing users the ability to sign in with their device or biometric data, passkeys provide a streamlined and convenient way of logging into supported services. And while convenient, they are also very secure thanks to the underlying tech that makes it possible: public-key cryptography. Interested in learning more about passkeys and how they work?
In this article, we’ll discuss what passkeys are, as well as some of the benefits they provide.
What are passkeys?
Passkeys are a method of signing into websites and services using cryptographically generated keys which are often stored on physical devices such as hardware tokens and modern smartphones.
When a passkey is created for a user account, the device that is being registered for the passkey will generate two keys: a public and a private key. The public key is sent to the service where the passkey is being registered, and the private key is stored securely on the device.
These keys are then used to securely sign into the service where the passkey is registered.
When the user tries to sign in using a passkey, the client will request a challenge from the server. The client then signs this challenge with its private key and sends it to the server. Once received, the server checks that the signature is valid using the public key it has.
Provided the signature is valid, the user is then signed into the service without having to enter any information manually.
- User device requests a challenge from the server.
- Server sends a challenge back, which goes to the authenticator
- The authenticator checks with the user that they are trying to sign in.
- On confirmation, the authenticator signs the challenge using the private key and sends it to the server
- The server validates the signature with the user’s public key
- If valid, the server completes the request and the user is signed in
The use of passkeys creates a passwordless experience that is both convenient and secure for the user signing into the service.
How does public key crypto work?
To understand the magic behind passkeys, it's worth understanding how public-key cryptography works.
Public-key cryptography works by using a pair of keys in order to securely store, sign, or transmit data. The private key can be used to encrypt or decrypt data, as well as generate a signature based on the data. The private key should always be stored securely since anyone who has the private key can also sign and decrypt data.
The public key can be used only to encrypt data, or to validate a signature from the private key. The public key can be distributed without risk as its primary utility is to secure data before sending it to a destination that has the private key.
Because this system uses two different keys, it is also referred to as asymmetric cryptography.
A practical use of public-key cryptography
While passkeys are relatively new, public-key cryptography has been around since the 1970s and has a wide number of applications and use cases. One such application that demonstrates these concepts well is end-to-end encrypted messaging.
Let’s say Ava and Brent use a secure chat app to communicate regularly. They each have a set of public and private keys. When they first connected, Ava would have sent her public key to Brent, and Brent would have sent his key to Ava.
When Ava sends a message to Brent, her device encrypts the message using Brent's public key and the encrypted data is transmitted over the internet to Brent. When Brent receives the message, his device would use his private key to decrypt it before displaying it.
Now let’s say Charlotte tries to intercept the messages Ava is sending to Brent. Because the messages are encrypted and Charlotte does not have Brent's private key, the data being received is unreadable.
Even though this example uses a chat application to demonstrate how public and private keys work together, the same can be applied to the login process for passkeys.
How are passkeys more secure than a username and password?
Passkeys are more secure than using a traditional username and password for a few reasons.
Convenience
There is often an indirect relationship between how secure something is and how convenient it is. Passkeys however have the benefit of being convenient for users to take advantage of by providing a very streamlined experience to signing in to a service.
People tend to gravitate towards solutions that are easier to use. Combining the high security of public key crypto with the simplicity of just signing in by tapping a button, users of passkeys get the best of both worlds.
Password reuse
Reusing passwords across services is a bad security practice. If one password gets compromised, whether it's your fault or theirs, any service where that password is also used should now be considered compromised as well. This can be a nightmare if you use the same password across dozens of services!
With passkeys, each service automatically gets a unique key pair. This means that if one service does lose control of its secrets, any other accounts you have that use passkeys are still secure, eliminating the work needed to cycle your passwords in the event of a breach.
Credential strength
One strategy for hacking an account is by repeatedly guessing a password until the correct one is discovered. This is known as brute-forcing, and password length is often the biggest determining factor on how realistic it is to brute-force a password. The longer the password, the less chance it can be guessed.
A 16-character/byte password is often considered very secure, but passkeys are approximately 100-1400 bytes according to the Electronic Frontier Foundation, which means they are nearly impossible to determine with this approach.
Built-in MFA
Multifactor authentication (or MFA) is the use of multiple methods to verify that the user attempting to sign in is who they claim to be. Common factors used are something you know, something you have, or something you are.
For instance, if you sign into a service with a username and password, those are considered a single factor since you know both of those pieces of data (and one is often public). Adding an authenticator app or hardware token adds an additional factor since it utilizes something you have.
With Passkeys, MFA is built in. The device (along with the public/private key pair it generates) is one factor, and since biometric data is often used to unlock the device, that's a second factor.
Eliminates phishing attempts
Phishing is where an attacker creates a look-alike website and attempts to trick users into entering their credentials. For example, a user might receive an email that appears to be from Amazon stating they are going to place an order that was never approved and telling the user they can manage it using a link embedded in the email. Instead of this link going to "amazon.com", it may go to "anazon.com" or another similar domain.
Since the domain looks close enough to the real one, the user may click on it and enter their credentials, which are then stolen by the attacker.
Since the passkeys generated on a device are specific to the domain for which they were created, this removes phishing as an attack vector. If an attacker does mimic a website and tries to get the user to log in, the device will understand that the domain is incorrect and will not offer the option to sign in. This also includes domain names that contain non-standard characters that appear to look the same.
Clerk supports passkeys
Passkeys are an officially supported authentication method for services secured with Clerk.
You can enable passkeys just like you would any other login method for your users.
Once enabled, your users can add passkeys through their User Profile.
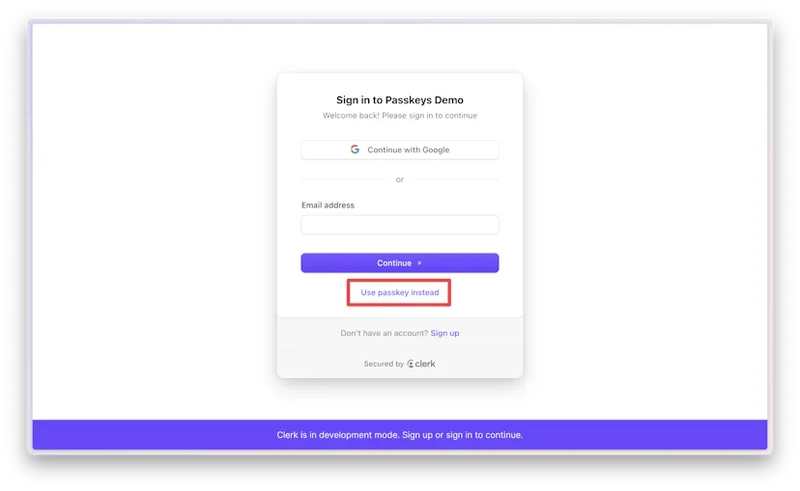
When signing in, they’ll be presented with the option to use a passkey.
For more information on using passkeys with Clerk, check out the passkeys overview in our docs.









Top comments (3)
Very good demonstration you can find here webauthn.me/
And try all parameters here webauthn.io/
I strongly recommend require use User Verification for all passkeys, because without it your YubiKey will not require a pincode and it's not 2FA
For nice summary, but I miss here a little bit how to backup these pass keys, what happens if the user lost the device the passkeys are stored on.
Maybe a topic for another article?
That's definitely a concern with passkeys since they are tied to the hardware. I know Clerk only allows you to add passkeys to an existing account which prevents this kind of lockout issue. Otherwise using a third party solution to store passkeys like Bitwarden (my preferred solution and not necessarily suggested by Clerk) is probably the way to go.