Published as part of BlockRelations’ BlockBit series
Authored by Brian Hough, Block Relations Business Intelligence Bureau
Amid all of the news related to the pandemic, COVID-19, and global fears about the future of our planet, something that managed to break the news around the world was a global hack on Twitter’s platform.
We often put our social platforms and our accounts on a pedestal of untouchable, unreachable bounds, and it’s hard not to think that these days. We live in an age of multi-factor authentication (MFA), encryption keys, voice-authorized authentication, AI/ML, and even retinal scans, finger prints, and biosensors.
Unfortunately, we find that it’s far too easy to forget that these services and technologies that we depend on around the clock are human too. Or at least, the people who built them are only human. It’s easy to forget that hacks can, and do, happen regularly, and Twitter’s hack was a big wake-up call for many on the Internet.
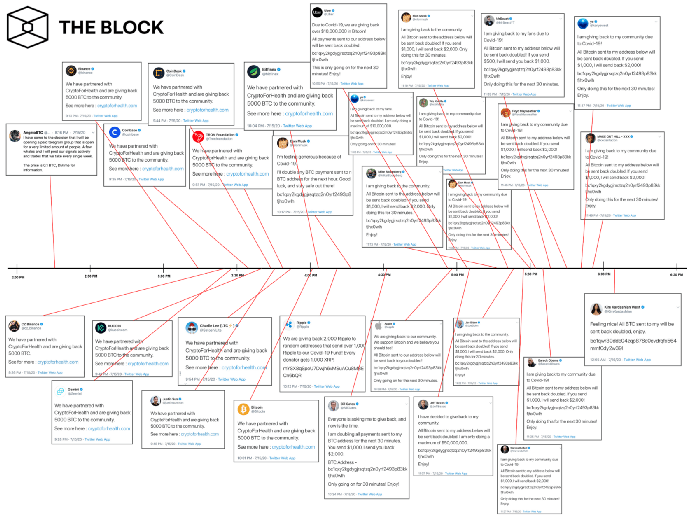
On July 15, simply within a span of two hours, numerous high-profile Twitter accounts were compromised in a wide-ranging cyberattack. The hacked accounts ranged from the likes of former President Barack Obama, former Vice President Joe Biden, TV personality Kim Kardashian, rapper Kanye West, Microsoft + Open Source co-founder Bill Gates, and entrepreneur Elon Musk. These accounts, collectively totaling multiple millions of followers, were used to post Tweets encouraging followers to send Bitcoin (Bitcoin Magazine) to various addresses after having had access to the accounts for some time.
A graphic from AnChain.Ai, demonstrating how the hackers have begun to distribute the money they took from Twitter users who were hoping to receive Bitcoin from celebrities or companies (Source: AnChain.Ai)
According to Larry Cermak’s reporting from The Block, Twitter reported that the cyberattack targeted Twitter employees “with access to internal systems and tools and then change the email addresses associated with those accounts.”
By manipulating Twitter’s own to facilitate such a wide-sweeping attack, the hackers proved how the walls of security can be breached through human intervention and infiltration.
A timeline of the compromised Twitter accounts (Source: The Block)
To round out this tumultuous month for Twitter, Sean Hollister broke the news on July 31 in The Verge that the FBI, IRS, US Secret Service and Florida law enforcement had placed a 17-year-old from Tampa, Florida, under arrest.
According to the article, the hacker was accused of being the culprit of the “biggest security and privacy breach in Twitter’s history.” Additionally, the Department of Justice formally charged two others in the hack, a 22-year-old from Orlando and a 19-year-old from the UK.
In the affidavit, the hacker claimed that he worked in Twitter’s IT department and tricked an employee at the company that they should give him various credentials, inevitably providing unfettered access to the subsequently compromised accounts.
Aftermath and Effects:
Following the hack, many people were drawn to the Bitcoin, hack, and scam buzzwords, but what has been largely absent from the conversation is what the hack actually means.
Redacted screenshot of the leaked Twitter administrative panel used to conduct the scam (Source: VICE)
By entering a full administrative mode, we know that the hacker was able to post on behalf of the accounts that were compromised, but they were most likely able to see private account information as well. This could range from email addresses and phone numbers to passwords, direct messages, saved Tweets, lists, and other account-specific information. Especially if the Twitter account was used to log into other online accounts, this could lead to further account-based hacks.
What this means is that this series of hacks could potentially have been more malicious than simply logging into Twitter and posting on behalf of them. In addition, it reveals the susceptibility of web platforms — how “hackable” they truly are — and not just from a firewall privacy perspective, but also from an infiltration standpoint.
This begs the question…
How can we ensure that our identity is completely decentralized and secure so that no one can pretend to be anyone other than who they are?
Blockchain is sure positioning itself as the necessary solution to this egregious problem, given the ability to authorize access on behalf of the user, only when the user grants/permissions this access.
Centralized centers of data, information, and system governance — particularly seen in web2 platforms and protocols — are highly susceptible to hacks, break-ins, and bypassed firewalls because of the data existing in a single location.
With blockchain technology however, data is distributed across the public or private chain, making the information infinitely more difficult to compromise.
By integrating a decentralized user authentication protocol, web2 platforms can adopt a new way of user authentication with web3 capabilities to keep their users and their platform’s data more secure…
I’ll have more to come on this…
Thanks for reading!
—
If you got value from this article, please LIKE 👍, COMMENT 📝, and SHARE ↩️ this post with your network, as well as FOLLOW 📲 my Twitter, Medium, and LinkedIn accounts for further insights on technology, innovation, and our digital world. See you next time!





Oldest comments (0)