In today's world of identity and security, there is a big push for passwordless authentication. However, even when you enable passwordless, there is always the option to fallback to entering a password when using Azure Active Directory (AAD).
For those who have not randomised their AAD password when going to passwordless, there is still a risk your account can be targeted using this traditional authentication method; leaving you liable to the already established social engineering tactics.
Of course, this does not just land itself to passwords and passwordless. When I enrolled two factor authentication (2FA) with GitHub, I was given a set of recovery keys. A great initiative in order to allow users to gain access to their account should they not be able to use that mechanism anymore... but this relies on one important thing:- those security keys being stored securely. Too many people without cyber security awareness will simply copy those keys, paste them into a txt file and name that file " account recovery keys" meaning that the enhanced security on your account is just a facade should an attacker have access to your files.
Even if we are cyber conscious, there are often controls outside of our control enforced on our authentication experience. Some companies specify if you add Microsoft Authenticator as an authentication method, you must also add a second authentication method, often this is forced to be SMS/Phone based.
Your account is only as secure as your lowest authentication method rating.
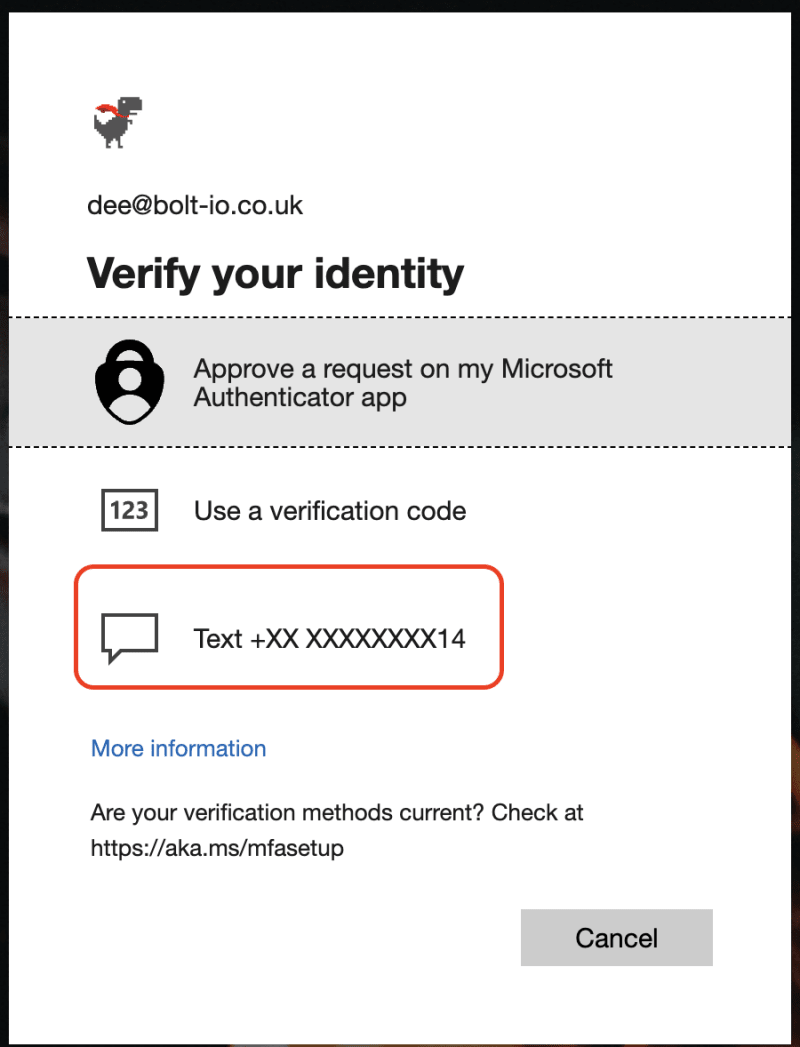
What do I mean by this? Let's say you had just password authentication, this is probably bottom tier in terms of account security hygiene. Well, if you add two-factor authentication (2FA) with an SMS/Phone based one-time password (OTP), your account is undoubtably more secure than it once was but there are SMS intercept attacks that can allow attackers to have unauthorised access to your account.
Okay, so password and 2FA with SMS is insecure, so I've enrolled time-based one-time password (TOTP) to my account. Well, you're still susceptible to the SMS intercept attacks if you kept your phone authentication method on your account as a back-up authentication system; since the point of back-up authentication methods are to allow you to use that method to gain access to your account if you can't get a TOTP. Therefore, those organisations that force you to have a SMS/Phone call based back-up method are lowering your account security rating! I challenge you to take that to your security team.
My final notes on this topic:
- Never use the same password across multiple accounts.
- Always aim for the strongest authentication method available.
- If you have recovery keys to store, make sure they are stored and secured properly.
- If you enrol a stronger method then check to see if other, more susceptible, methods can be removed.
- Challenge the policies in your company if you think they can improve their security posture.


Oldest comments (0)