Hi! I’m Ben Greenier — I’m an engineer at Microsoft working to create awesome open source projects with our partners. We get to create software to help solve really tricky problems, and share our stories as we go. This means that as part of my job I get to play with lots of new technologies, learn how to use them, and help other folks do the same.
I'm currently working on an Azure App that runs in Azure App Services and uses EasyAuth to validate Azure AAD B2C credentials before allowing a user to access the app. Overall things work pretty well for users, but it's come time to add some integration testing, and I need an automated way to retrieve a user credential so that the testing can authenticate to the service.
To allow automated authentication without a browser, I've created a separate B2C user-flow with ROPC authentication enabled. I'm then able to issue a simple POST request from my test runner, and retrieve a token! I thought I was done, but the test was still failing even when using this token - weird.
I loaded both a user token and an automated token into JWT.io and realized they had different issuers - what a pain! Since I had EasyAuth configured to verify that the issuer of all tokens matches a specific issuer (and only one issuer is supported) I'm stuck again.
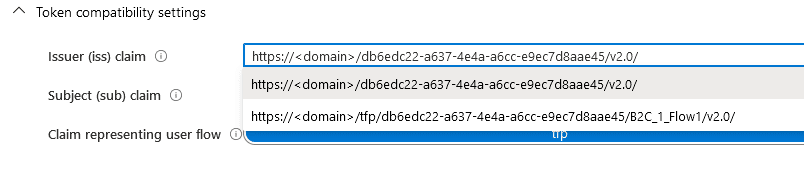
To get unstuck, I went spelunking in the Azure B2C portal to see if there's a way to control the issuer for different user-flows. As it turns out, there is! In the portal, you can pick one of two values for the issuer. One that is unique to the user-flow, and one that is unique to the B2C instance.
It turns out that the user-flow that my actual users leverage was using the value unique to the flow. In order for EasyAuth to validate that both tokens are issued by the same issuer, I set both user-flows to use the issuer that is unique to the B2C instance. Since both flows are in the same instance they then have the same issuer. You can see the difference in the URIs here:
Issuer that's unique to the B2C instance:
https://authsucks.b2clogin.com/db6edc22-a637-4e4a-a6cc-e9ec7d8aae45/v2.0/
Issuer that's unique to the user-flow:
https://authsucks.b2clogin.com/tfp/db6edc22-a637-4e4a-a6cc-e9ec7d8aae45/b2c_1_flow1/v2.0/
After updating both user-flows to have the issuer https://authsucks.b2clogin.com/db6edc22-a637-4e4a-a6cc-e9ec7d8aae45/v2.0/, and configuring EasyAuth to use that same value for verification, tokens from both flows validated successfully and my tests started to pass!
Thanks for reading - If you'd like to further support me and see similar content, follow me on twitch and/or twitter. If you're stuck on a similar problem, or you were and this helped, I'd love to learn more about that situation - leave me a note in the comments.
💙🌈
-Ben
P.S: Header photo by Chris Barbalis on Unsplash







Top comments (0)