Password strength, password management, password memorization, password bla bla bla. We spend half a day writing (or saving in browser) password for any damned service we use online. And we always use the same passwords, because surely we know that is a bad (ugly!) habit, but we really can't memorize so many abstract things.
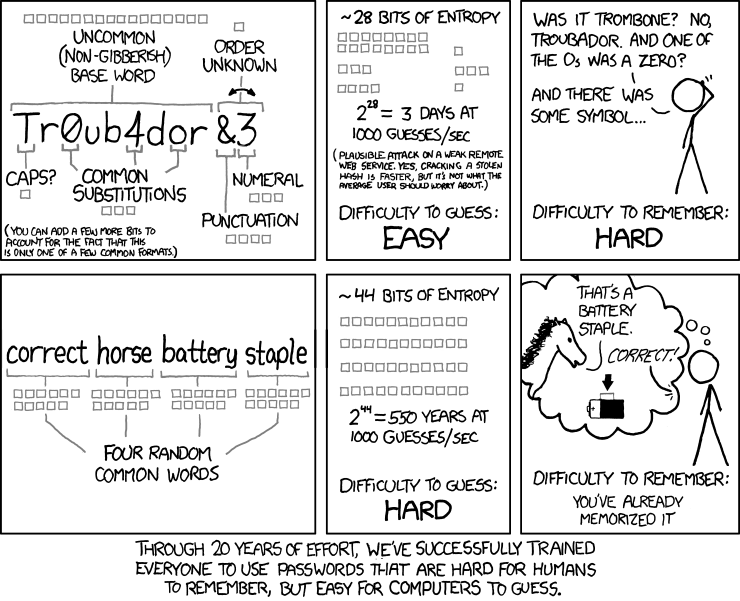
A lot of articles has been written ont this argument. A lot of good advices have been adviced. XKCD has suggested, in my humble opinion, one of the best methods to generate a single, long, secure password:
But still, this is a good method to remember... one? three? six? different password. If you try to set a different password for every service you'll quickly have a lot of possible permutations to remember: «So, for gmail was correct horse battery staple, for github wolf cucumber pencil mug, then for slack is penguin banana honey bacon? Or it was honey wolf banana honey?»
So, my personal solution is simple. Aren't we developers? Aren't we everyday managing algorithms? Aren't algorithms our daily tool to resolve problems? So, why don't we use an algorithm to generate a unique password for every site?
The algorithm has to be simple, because we'll have to run in in our brain. For example:
- The first three letters of the second level domain, in NATO phonetic alphabet, camel cased
- An open square bracket
- The length of second level domain, in letters
- The lenght of the first level domain, in number
- A square bracket closed.
Obviously I've made up this algorithm for this post, so don't try it on my accounts! :-) By the way, it's complex but can be easily remembered, and generates different passwords for every site:
| Site or service | Generated password |
|---|---|
| dev.to | DeltaEchoVictor[three2] |
| gmail.com | GolfMikeAlfa[five3] |
| github.com | GolfIndiaTango[six3] |
And so on. Obviously everyone can improve his algorithm as he wish: adding other symbols depending on any parameter, inverting the order of characters, adding a simple Caesar encryption... There are no limits, just the mental complexity everyone decide is affordable.
For the most paranoid ones (and when we talk about security we surely should be all paranoid), the algorithm should be quite robust also if a single password gets violated. Il some bad hackers should violate github and in some way get our password, a human being reading GolfIndiaTango[six3] could understand the phonetical part, and think about the possibility of an algorithm approach, and try it on other services we use. I think it's a remote possibility, because it can happen only if someone is targetting exactly you, and normally this isn't the case. But still is a possibility, so every one must choose his algorithm carefully.
I've never read anything about this algorithmic approach, but I've not searched about either, so as we say in Italy maybe "I've discovered the hot water". But I really love reading your considerations about.



Top comments (14)
Hmm, what about password managers? They'll generate passwords with much higher entropy. I'd rather stick to them.
Sure, if you always work on the same pc. But if you have to login on a foreign computer, or you don't have your phone at hand, you are lost.
On the other hand, if you have your memory wiped, you have far more problems than logging on GitHub! 😁
What about LastPass ?
It's an online password manager, also includes plugins for different browsers (so you don't have to "copy & paste" password nor username from your local password manager).
I've been using it for a long time and I'm very satisfied with it
I'd prefer 1Password, but it is not free (i.e. gratis).
Online password manager need you to trust them. I use Chrome password management, because I think Google is big enough to keep an "evil legal" alignment. Smaller companies... well, I don't trust them. But it's just my opinion :-)
Don't forget the cli
Sometimes you need password not only for web pages/services. Chrome won't help you with that.
Yes, that's why I always have encrypted pw database back-up on USB drive :)
But I understand the issue with mobile devices and foreign computers, that is valid point.
Remember a friend from college had a similar strategy.
Start with the name of the site (take dev.to), put your finger on the "d" and then do a dance on the keyboard:
As long as you remembered the dance, you had a password.
*This was before password managers were a thing.
And as long you stay on QWERTY…
With #MessagEase you are lost!! 😂
Has anyone out there seen The Bank Dick with W. C. Fields. In the movie, they had to rehire him because nobody could find anything in his files. The difficulty in finding information in my house is similar. So I have to wonder how much effort it would take to break into my house, go through all my papers, and find the desired information. So what I aim for is a system that will take far more effort to hack than my information is worth. It's not really all that difficult. Everybody talks about the possibility of a reverse dictionary attack, but that is only usable if they can obtain a copy of the hashes of the passwords. That is why UNIX put in the shadow password file. Where the password file was public, the shadow file was not and that is where the sensitive information was placed. Since most systems limit the number of accesses a second, the movies where a hacker tests a billion passwords a second just isn't practical. Also, many systems allow you to change passwords with your email account and phone number. Malicious actors are generally looking for a very low cost per account. So I'm not that worried about the password managers so long as I use reputable ones. If you have really sensitive information, you shouldn't be relying on passwords or two-factor authentication alone.
I would highly recommend using a verified online password provider such as LastPass, 1Password and so on. These offer significant value above and beyond simply remembering your passwords for you, such as knowing which have been compromised, and filling them in (only on the right site, too).
The best password is what no one knows, not even yourself. Use a password manager and generate long passwords.
If you use a scheme then you weaken your passwords and giving a chance to break them.
I used to have a similar process to create my passwords.
I had issues with these passwords: some site doesn't allow the special character I used, some other site thinks that my password is too long and so on, there are many different ways where my scheme didn't work. So I needed to add exceptions, change the algorithm and after all it was hard to use my own scheme.
Now I only use randomly generated passwords, I adjust it's length and character set to the site if needed.
One more important thing is that with a scheme it's hard to change the password. For one domain you have one password or need to alter your scheme but often it's still won't work. You know there are different checks that my new password should not be similar to the previous.
But worth mentioning that it's still better than using the same password everywhere. It's not tied to birthday or pet name, but there are weaknesses too.
Last year I wrote a package based on BIP39 that generates private keys based on 12+ easy to remember words, used for crypto wallets, it was fun.
Passphrases are harder to crack and easier to remember (than "regular passwords"), but most websites enforce to stupid arbitrary rules to have special characters that are anti-humans, so I use OpenID providers as much as I can.
And Chrome now recognize register forms and recommend passwords like a manager.
Amazing how security-aware people recommend password managers as a service, that are a single point of failure and a place with all your passwords. For me sounds the opposite of safe, but in the end so is the Chrome password manager or a notebook ...