How to use Azure App Service managed certificates
Securing your App Services
As you know, it is important to secure your applications. One of the security measures that you need to take is to protect traffic to and from your web application. You can do that by encrypting traffic with SSL certificates so that traffic will always go through the HTTPS protocol.
Azure App Service makes it very easy to protect your application that has a custom domain, with SSL certificates. You can bring your own certificate, buy an App Service Certificate and now you can use a free App Service Managed Certificate. Each of these can be used for different requirements as you can see in the table below:
| Requirement | App Service Certificate | App Service Managed Certificate |
|---|---|---|
| Protect www domain (i.e. https://www.microsoft.com) | X | X |
| Protect naked domain (i.e. https://microsoft.com) | X | |
| Protect wildcard domain (i.e. https://azure.microsoft.com) | X | |
| Certificate is exportable | X | |
| Certificate Issuer | GoDaddy | DigiCert |
| Costs | \$69,99 (standard) - \$299,99 (wildcard) / year | Free |
In this post, we'll protect an App Service Web App with a free App Service Managed Certificate.
Prerequisites
If you want to follow along, you'll need the following:
- An Azure subscription (If you don't have an Azure subscription, create a free account before you begin)
- An existing Azure App Service Web App with a valid custom domain coupled to it
Protect an App Service Web App with an App Service Managed Certificate
Standard Azure domains (yourwebsite.azurewebsites.net) are already SSL protected by default, but custom domains aren't. So let's use an App Service Managed Certificate to protect a Web App with a custom domain.
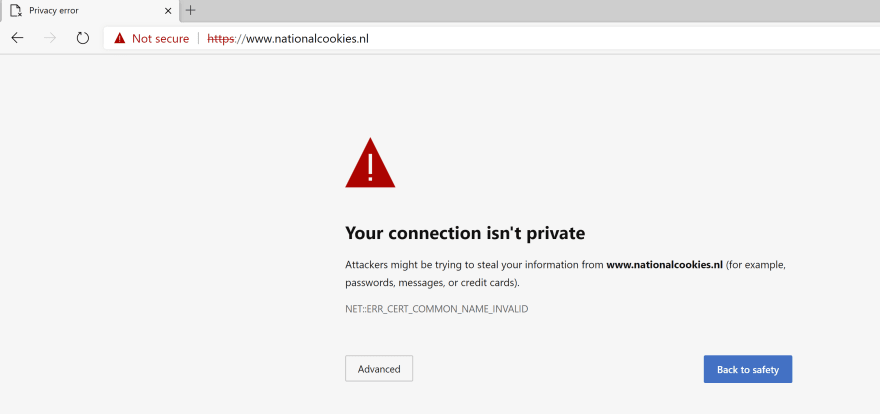
I start out with a website that runs in an Azure Web App under a custom domain and doesn't have any SSL bindings configured. When I navigate to this website, my browser warns me that my connection isn't private. Let's fix that.
(Website without SSL)
- Go to the Azure portal
- Open your Web App that has a valid custom domain coupled to it
- In order to use custom domains and protect them in Azure App Service, your App Service need to run in the B1 service tier or higher. You can check if this is the case by taking a look at your settings in the Scale-up (App Service Plan) menu in the Web App
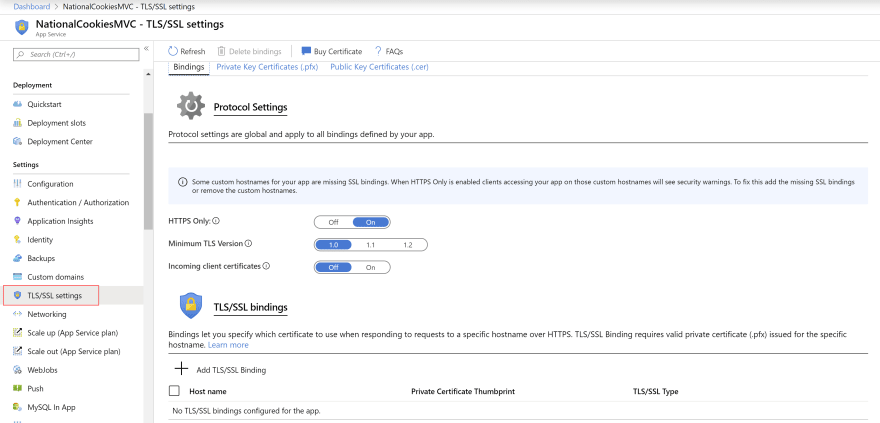
- Go to the TLS/SSL settings menu in the Web App. Here, you can see that there are no SSL bindings for the custom domain yet
(TSL/SSL settings menu in a Web App in the Azure portal)
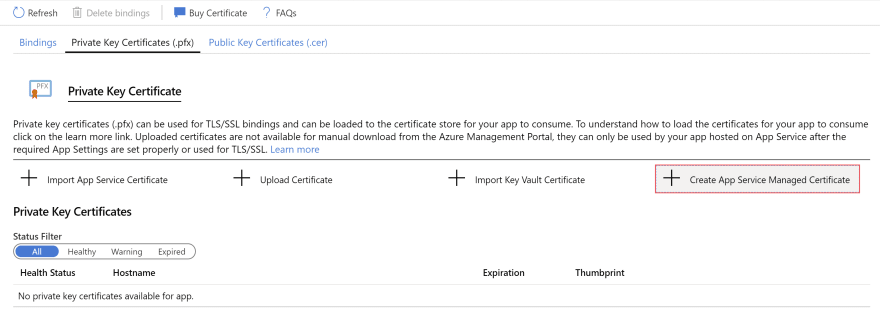
- Click on the Private Key Certificates (.pfx) button. This opens the Private Key Certificate blade
(Private Key Certificate settings in the Azure portal)
- In the Private Key Certificate blade, there are no certificates yet, so let's create one. Click on Create App Service Managed Certificate to start creating one
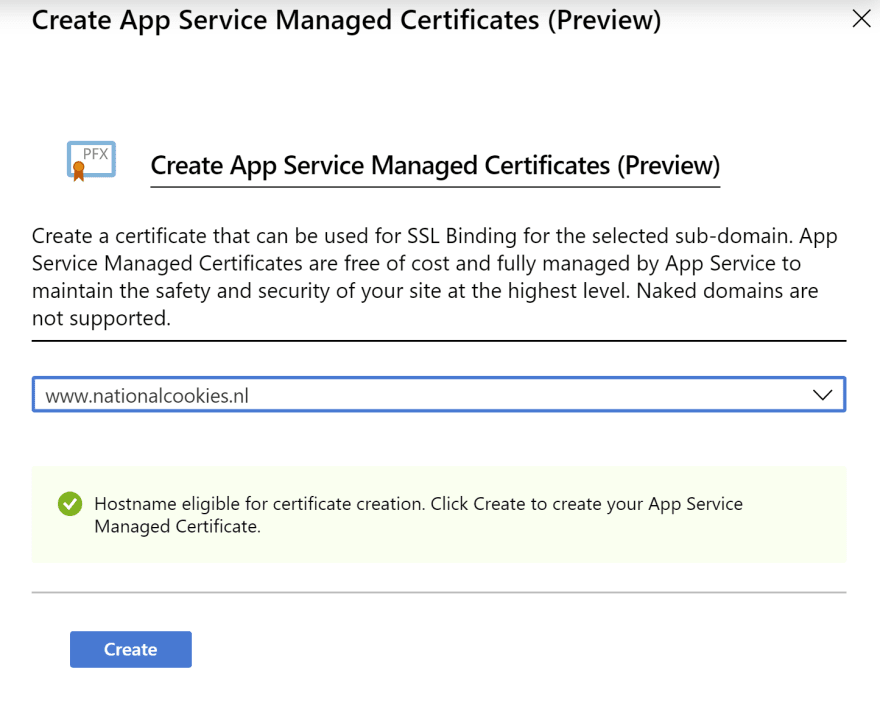
- Select the custom domain name to create the App Service Managed Certificate for and click Create to create it. Remember that you can only use managed certificates for www domains, not naked domains
(Create App Service Managed Certificate in the Azure portal)
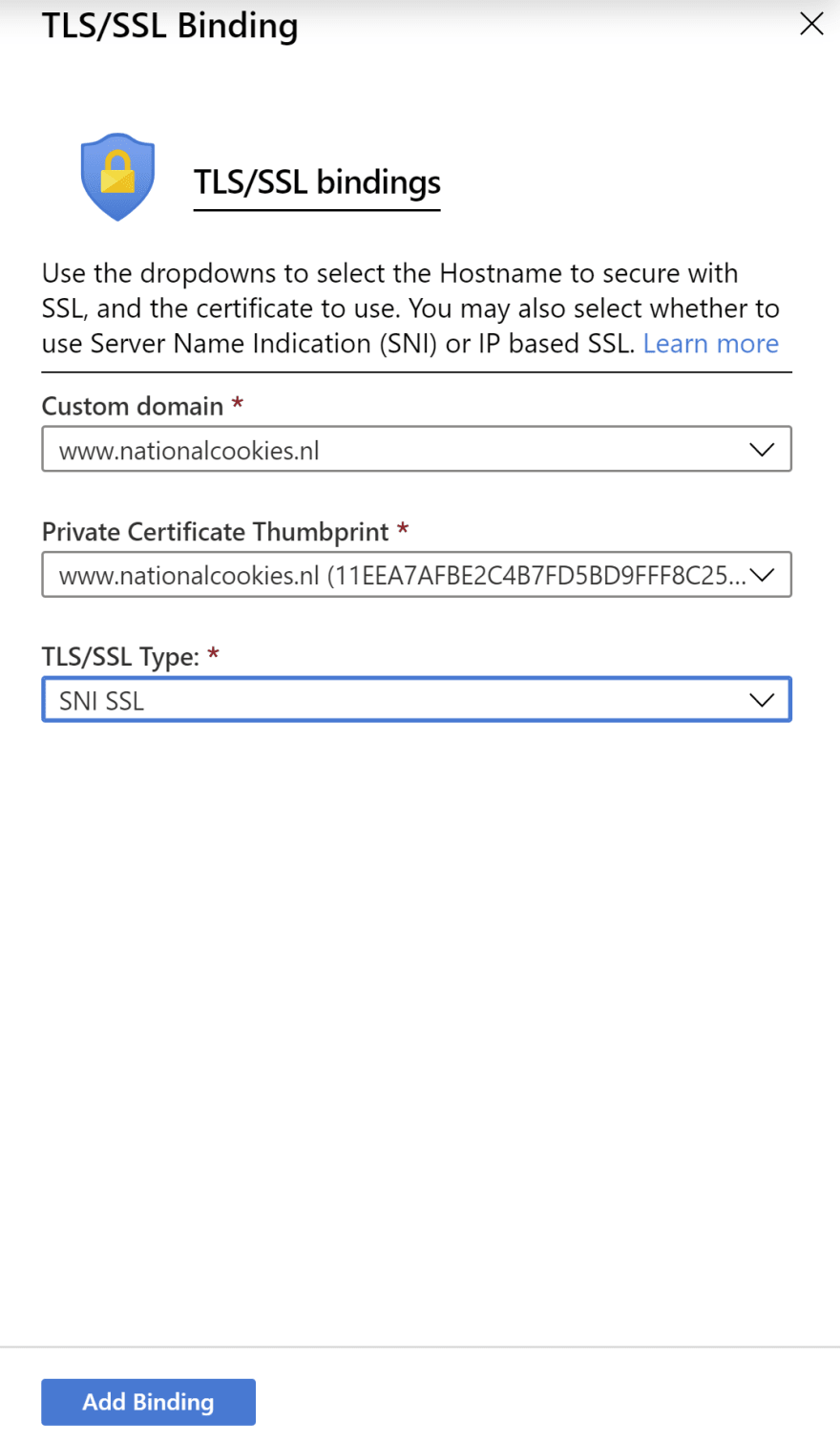
- When the certificate is created, go back to the Bindings blade. Here, you need to create a binding between your domain and the certificate. Click the Add TLS/SSL Binding button in the bottom of the blade a. Select the Custom domain to create the binding for b. And select the Certificate that you've just created c. Also select the TLS/SSL type. In this case, only SNI SSL will be available d. Click Add Binding to add the binding
(Add TLS/SSL binding in the Azure portal)
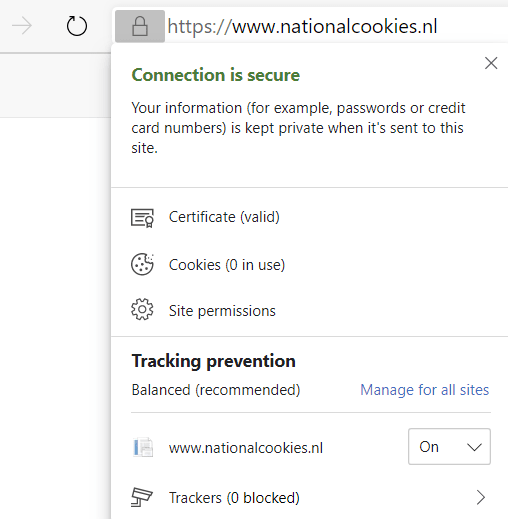
That's it! Now, when you navigate to the website, the warning will no longer be visible. Instead, you'll see a green lock next to the URL. And when you click on it, you can see that the connection is secure and that the certificate is valid.
(Website with SSL)
Conclusion
Azure App Service Managed Certificates provide a great way to implement basic security for your application. It is free and once you've generated a certificate, it will renew itself, so you don't have to think about it. Read more about it here and check it out!



Top comments (4)
Unfortunately, it only works if you have primary domain cert from Digicert.
Azure app certs are GoDaddy and managed cert now is Digicert. It is confusion for deployment and implementation when services are featured as Azure product and behind the scene it is not actually AZ services. I tried using it to create and failed as I have GoDaddy cert from KV which does not allow managed domain implemented by Digicert
Looks quite easy but only for www subdomains? For me this looks a bit too constrained isn't it?
This worked for me - thanks!
The free managed cert didn't renew for us, after the validity expired!