What happens when the very antivirus designed to keep you and your organization safe becomes a threat vector for the attackers to exploit?
Yesterday, I broke the news story on Bleeping Computer about a remote code execution vulnerability which was recently discovered and disclosed by security researcher and blogger Wladimir Palant.
Palant explained how the vulnerability, CVE-2020–8102, impacted BitDefender versions up until the one released recently: “An automatic update to product version 24.0.20.116 or later fixes the issue,” stated the company in an advisory.
Vulnerability Identifier: CVE-2020–8102
Date disclosed: June 22nd, 2020
Impacted components: Bitdefender Safepay
CVSS Score: 8.8
CVSS 3 Metrics: CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H
The vulnerability when successfully exploited can let attackers execute remote code on a Bitdefender user’s machine from any malicious website they control!
Vulnerability origins
Like many leading antivirus products and in an effort to provide overall system security, BitDefender acts as a Man-in-the-Middle (MitM) proxy intercepting and inspecting encrypted HTTPS connections.
Most of these products have a component geared towards online security, referred to by Safe Browsing, Safe Search, Web Shield, etc.
The vulnerability stems from the fact how BitDefender handles SSL certificates. When an invalid SSL certificate is presented by a website, most modern browsers let the user decide: to accept the certificate at their risk, or to navigate away. Likewise, BitDefender in an effort to offer safer browsing experience to users, provides its customized version of such a webpage:
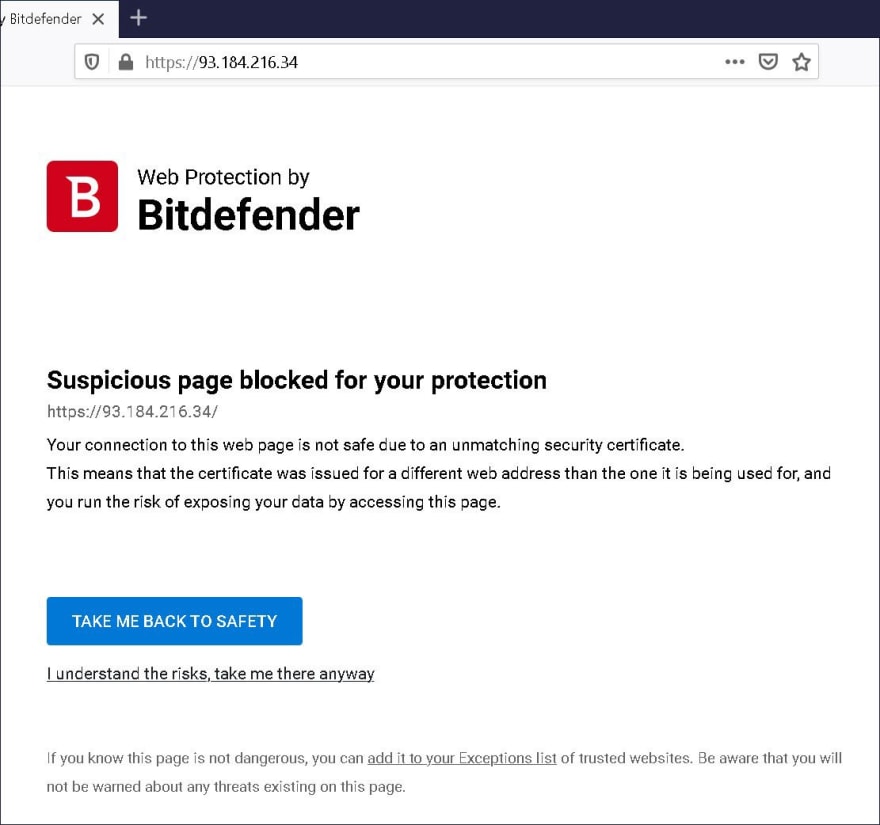
Image: Invalid certificate error page generated by Bitdefender (Source: Wladimir Palant)
If a user still ignores HSTS warnings and continue to access the website at their own risk, that often poses no issues.
But, a key finding here, as Palant pointed out, is the URL itself within the address bar of the web browser remains constant. This causes Bitdefender Safepay to share security tokens between that (potentially malicious) page and any other website hosted* on the same server *and being accessed within Bitdefender’s Safepay virtual browsing environment.
Shared session tokens
Ideally these session tokens should not be shared between websites.
“The URL in the browser’s address bar doesn’t change. So as far as the browser is concerned, this error page originated at the web server and there is no reason why other web pages from the same server shouldn’t be able to access it. Whatever security tokens are contained within it, websites can read them out — an issue we’ve seen in Kaspersky products before,” Palant stated in his report.
Palant was able to verify this behavior by running a PoC. He setup a local web server and accessed it via Safepay. Initially, the server was designed to present a valid SSL certificate, but switching to an invalid one shortly after.
Once the certificate was switched to an invalid one, an AJAX request was made to download the SSL error page. Now, the same-origin policy in any web browser would naturally allow this request if it felt the same-origin was maintained, and so did Bitdefender Safepay.
“This allowed loading a malicious page in the browser, switching to an invalid certificate then and using XMLHttpRequest to download the resulting error page. This being a same-origin request, the browser will not stop you. In that page you would have the code behind the 'I understand the risks' link," Palant explained.

Image: The security tokens injected during a website by Bitdefender Safepay (Wladimir Palant)
These “security tokens” are hardcoded values that don’t change during a session; which is alright, but the same tokens are shared between different websites due to this bug, which is a problem.
Additionally, Safe Search and Safe Banking features of the component don’t implement any further protections, “As it turns out, all functionality uses the same BDNDSS_B67EA559F21B487F861FDA8A44F01C50 and BDNDCA_BBACF84D61A04F9AA66019A14B035478 values, but Safe Search and Safe Banking don't implement any additional protection beyond that," said Palant.
Remote code execution
This means, if a victim is tricked into accessing an attacker-controlled website via Safepay, the attacker can now have visibility into these tokens. And because these tokens are shared between the “isolated” banking websites accessed during a session, the attacker now has the ability to compromise those sensitive websites running in the same Bitdefender Safepay browser session.
But it doesn’t stop here. the attacker-controlled site can abuse the same token functionality to execute arbitrary code remotely on the victim’s machine, via a crafted AJAX request.
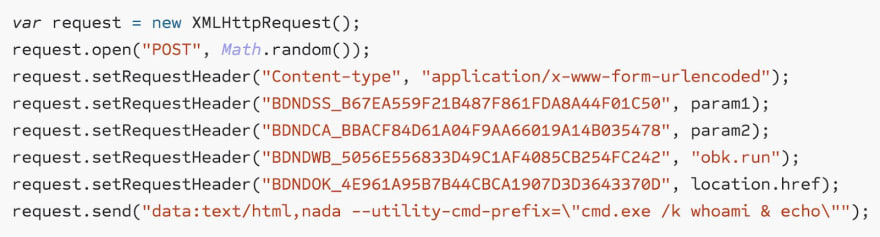
Image: Script to perform remote code execution (Source: Palant)
In just one example, Palant demonstrated how an AJAX request with a “data:” URI could be used to instruct the victim’s machine to launch a command prompt window running “whoami”:
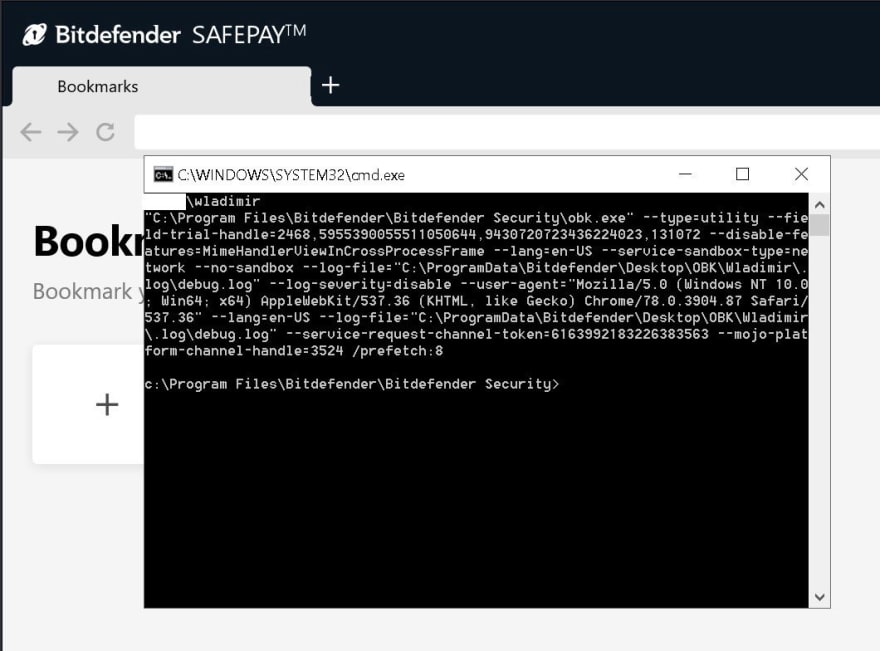
Image: Remote executable downloaded and executed (Source: Palant)
Bitdefender has issued an automatic security update in version 24.0.20.116 and above to patch this vulnerability.
Yes, a fix has been released to safeguard affected users, but vulnerabilities like these pose a greater question: how secure are antivirus products themselves?
In spite of best intentions, such as providing a secure browsing environment, what happened here certainly wouldn’t sit well with Bitdefender users.
Unless one is super-duper sure when playing Man-in-the-Middle (MitM), it is probably best to leave encrypted connections alone: just as they were meant to be.
Originally published at https://securityreport.com on June 23, 2020.



Top comments (1)
When it comes to cybersecurity I try to do the best with it. I had many problems because I didn't use antiviruses and I don't wanna make the same mistakes. That's why I read more Norton Antivirus review and other articles and bothered myself with PC protection. You know it's definitely worth it. Better safe than sorry after all.