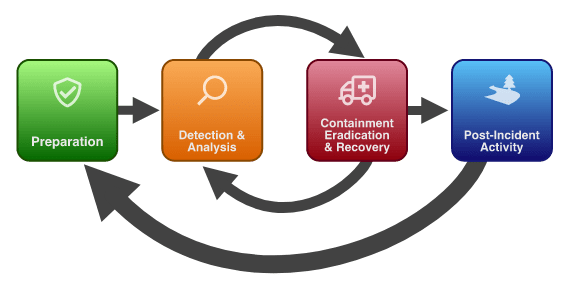
We covered how Steampipe can assist with Detection and Analysis in Enrich Splunk events with Steampipe. Today we’re going to look at how leveraging Steampipe relationship graphs can assist in the Containment, Eradication, and Recovery phases of the incident response cycle.
Let's say you have evidence a cloud host was compromised. One of the key questions you need to answer is, “What could that attacker have done while inside our network?”
Steampipe’s new relationship graphs are one method to determine the compromised host’s connectedness and Lateral Movement possibilities.
Start with EC2 Instance Detail
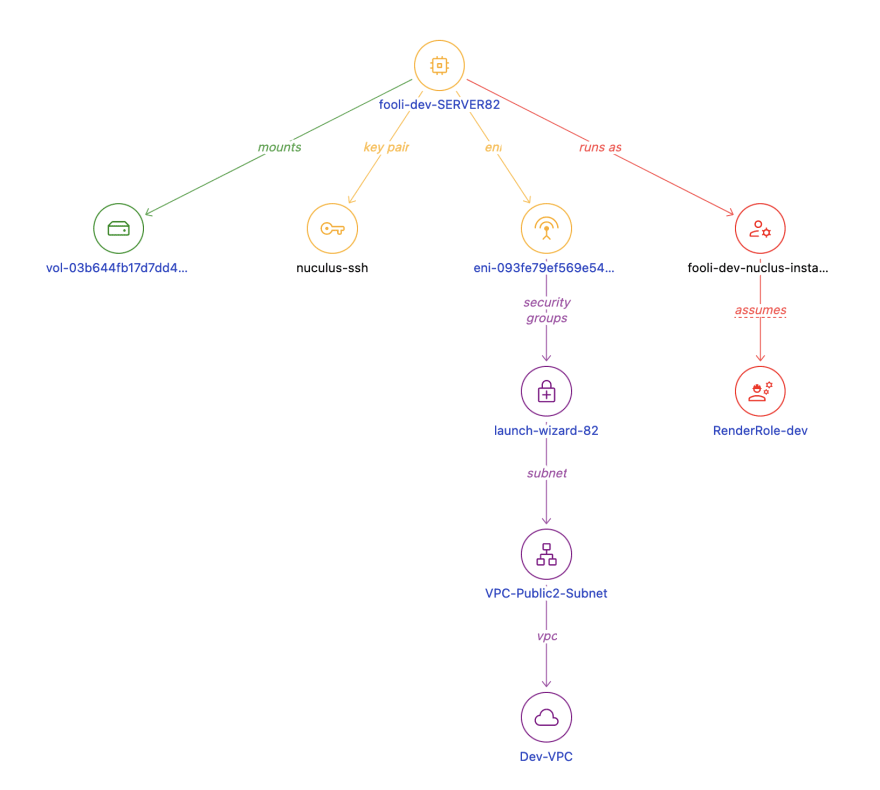
A typical incident starts with an event, and that event is often associated with an EC2 Instance. We can select the suspected compromised host via the AWS EC2 Instance Detail. In addition to details about the instance size, IP address, and tags, you can see several related resources including the SSH KeyPair used to launch the instance, the EBS Volume, and most importantly the IAM Instance Profile and VPC Information.
Here we see that the compromised instance has the RenderRole-dev IAM role and is located in the VPC-Public2-Subnet in the Dev VPC.
Dive into the Render Role
Click RenderRole to visit the AWS IAM Role Detail dashboard.
The IAM Detail relationship diagram shows us the attached policies, along with the EC2 instances and Lambda function that use the role. These are the permissions that the attacker could get from the EC2 Metadata Service.
Dive into the Dev VPC
In addition to viewing IAM actions an attacker might have had access to, you probably also want to know what network resources the compromised host could connect to. From the original EC2 Detail, we can also click into the AWS VPC Detail for the Dev VPC.
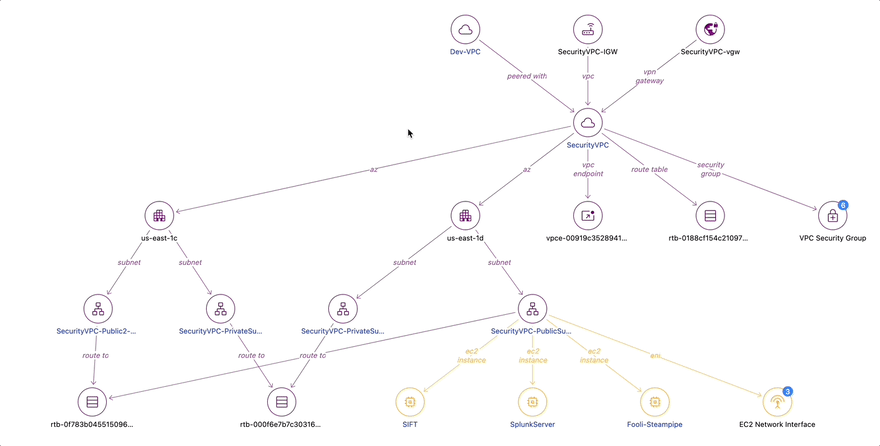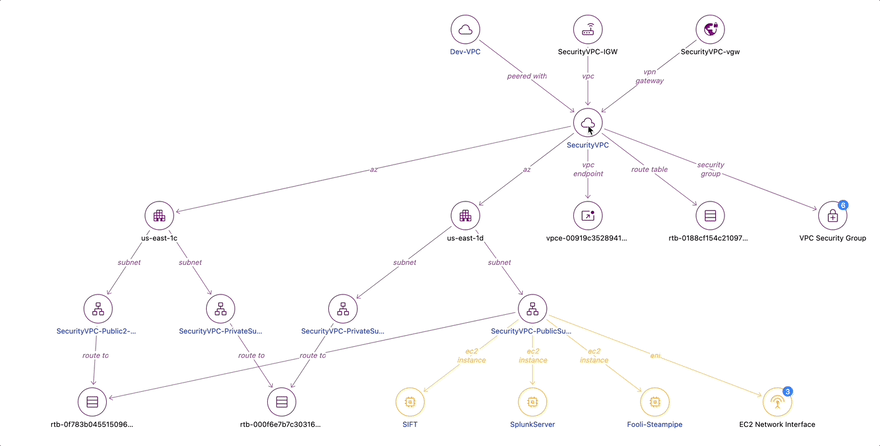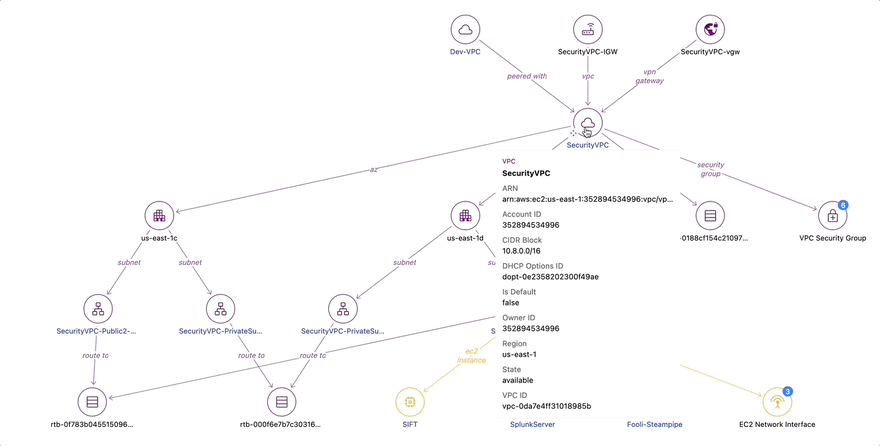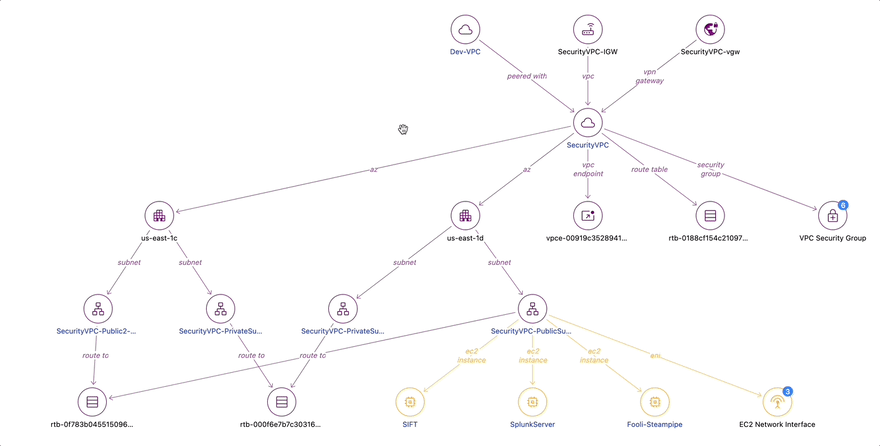
The relationship diagram shows us that in this VPC was an RDS database, a mail relay server, and a payments server. Critically, there were also VPC peering connections to two other VPCs: the Security VPC and the Meme Factory VPC. Let’s click on the Security VPC to see what is in there.
Dive into the Security VPC
Because Steampipe was configured to scan the entire AWS organization, we can pivot our view across multiple AWS accounts without logging in to the AWS console a second time. When investigating an incident, a responder often has multiple browser windows open to investigate, and this can lead to mistakes. Relationship graphs are an easier and more reliable way to explore the entire cloud network.
In the Security VPC, we find the SIFT forensics server, the Fooli Organization Steampipe instance, and Splunk, which is used as the Fooli SEIM.
Preparation
For incident response, preparation is vital. In order to be ready to use Steampipe to investigate an incident, you need to ensure everything is set up properly.
- Follow the guidance on Using Steampipe CLI with AWS Organizations
- Download the AWS Insights Mod for Steampipe
- Run the Steampipe CLI with
steampipe dashboard - If using Steampipe Cloud, simply install the AWS Insights mod in your workspace to get started.
Let's go exploring!
Once you’ve set up Steampipe or Steampipe Cloud to investigate resources, there are many other exciting things you can identify visually that you might miss in a tabular report.
The Steampipe ecosystem now offers more than 90 plugins; each provides several, dozens, or even hundreds of tables. You've always been able to use SQL to join those tables, not only within an API family like AWS, but across diverse APIs. Now you can also use SQL to build relationship graphs across APIs and cloud tenants. Imagine an always accurate network map that links your AWS and Azure VPCs with the firewalls in your data center. The sky's the limit, and we look forward to hearing about your discoveries in our Slack community.









Top comments (0)