Accessing databases can be a cumbersome process, often requiring VPNs, jumping through bastion hosts, and shared credentials. It doesn’t need to be hard though! The Border0.com integration with AWS RDS offers a seamless, passwordless experience using IAM-based authentication. This integration simplifies access and enhances security, visibility, and control.
IAM-Based Authentication for RDS
IAM-based authentication for RDS allows database access by integrating with AWS’ Identity and Access Management (IAM) system. This eliminates the need for traditional password-based logins, thereby enhancing security by ensuring that no static credentials are required. This way, the risk of credential compromise is significantly reduced, as users and systems can access RDS instances using their existing AWS IAM credentials. This approach not only simplifies the user experience but also adds an extra layer of security.
Better together: RDS IAM and Border0
Border0 integrates with and elevates the capabilities of IAM-based authentication for RDS by serving as an advanced, fine-grained database proxy that seamlessly integrates with your Single Sign-On (SSO) systems and RDS instances. This setup also provides a rich set of policies that allow administrators to define who should have access to the database by defining a set of granular conditions. And with our database level security rules for MySQL, it even provides an L7 database firewall, all in one solution!
One of the standout advantages of combining Border0 with RDS IAM authentication is the provision for passwordless access, where neither the clients nor the Border0 connector need to store database credentials, thereby enhancing security. As an additional bonus, Border0 also takes care of accessing private RDS instances, so there is no need for a VPN. Let’s take a look at how to set this up.
Setting Up IAM-Based Auth on RDS
Setting up IAM based authentication for your RDS cluster is easy, simply follow our docs here. For this example, we assume you already have a Border0 connector installed in your AWS environment. If you haven’t done so already, I recommend using either the aws installer, or the Terraform example.
Step 1: Enable IAM Authentication
Ensure IAM-based authentication is enabled for your RDS cluster.
Step 2: Configure MySQL to accept IAM authentication
Execute the following MySQL queries to enable IAM authentication.
CREATE USER Border0ConnectorUser IDENTIFIED WITH AWSAuthenticationPlugin AS 'RDS';
GRANT ALL ON MyAwesomeDatabase.* TO 'Border0ConnectorUser'@'%';
FLUSH PRIVILEGES;
Step 3: Create a Border0 Database Socket:
Create a Database Socket in the Border0 portal and link it to your Border0 connector and select IAM authentication.
Finally, make sure the connector has the proper AWS credentials. If you used the AWS installer (border0 connector install — aws) or our terraform example, then the IAM credentials will already be taken care off. Otherwise, make sure the connector host has rds-db:connect IAM permissions like below:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "rds-db:connect",
"Resource": [
"arn:aws:rds-db:*:*:dbuser:*/Border0ConnectorUser",
]
}
]
}
For a detailed guide, refer to the Border0 documentation.
Testing Access
Once set up, you can test the access through Border0’s client portal or use your preferred database client. Border0 offers close integration with a variety of popular database clients such as MySQL Workbench, DBeaver, MySQL, mycli, psql, and DataGrip.
Session and Query Logs
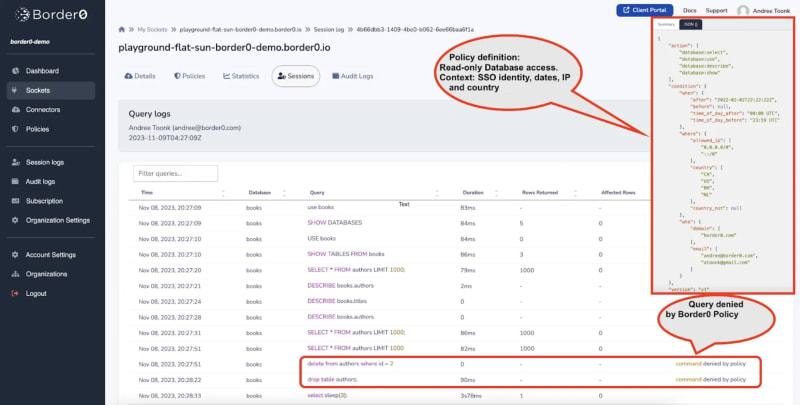
Now that your users can access the database, we can see a report of all access attempts in the Border0 admin portal. These session logs offer valuable information, such as who (SSO identity) accessed specific databases, the location from which the access was made, and the timing of the access. Additionally, query logs record the exact queries executed, providing a clear picture of database activity. This level of detail is particularly useful for compliance, auditing, and security monitoring, addressing challenges like attributing queries to individual users in systems where shared credentials are used.
Zero Trust security model for database access
Incorporating Border0 with AWS RDS IAM authentication significantly advances your journey toward a passwordless Zero Trust security model for database access. With Border0, you get fine-grained access controls that align with the Zero Trust principle of least privilege access. You can even specify the types of queries each user is allowed to execute. Unlike traditional methods that use shared database credentials, Border0 allows engineers to connect using their Single Sign-On (SSO) identity, ensuring each database query can be attributed to a user and is continuously authenticated and authorized. This fulfills the Zero Trust mandate of “never trust, always verify.”
The integration also eliminates the need for passwords, reducing the attack surface and making unauthorized access more challenging. This supports the Zero Trust focus on minimizing credential-based attacks. Additionally, Border0 restricts users to specific databases, preventing lateral movement within the network, and allows for the definition of permissible queries. This is a shift from the broader network access granted by traditional VPNs or Bastion hosts and aligns with the Zero Trust principle of micro-segmentation.
Border0’s detailed session and query logs offer extensive visibility, supporting the Zero Trust principle of continuous monitoring. The platform also allows for dynamic policies that adapt to real-time conditions, another cornerstone of Zero Trust. Moreover, all traffic between the end user and the connector (running in your environment) is end-to-end encrypted, ensuring that no intermediaries, including Border0 itself, can see or modify the database traffic.
By integrating these features, Border0 and AWS RDS IAM authentication provide a robust framework that not only aligns with but also enhances the principles of a Zero Trust security model.
Conclusion
In this blog, we looked at how Border0 and AWS RDS’s IAM-based authentication come together to redefine database access, security, and auditability. This powerful integration offers a secure, streamlined, and entirely passwordless experience, aligning perfectly with the principles of a zero-trust security model.
The advantages are manifold: for administrators, the ability to define fine-grained access policies, implement application-level security, and gain detailed query insights provides a level of visibility and control that is hard to match. For engineers, the user experience is significantly enhanced; they can effortlessly discover all databases they have access to and connect using either Border0’s web client or their preferred database client. All that is required are their SSO credentials, eliminating the need for VPNs — even when the RDS instance is hosted in a private AWS subnet.
Border0 takes care of the complexities, allowing both administrators and engineers to focus on what matters most. The end result is a solution that boosts productivity without compromising on security. Whether you’re an administrator aiming for robust security controls or an engineer looking for seamless access, this integration has something for everyone. We invite you to experience these benefits firsthand by exploring Border0’s free, fully-functional community and see for yourself how easy it is to start your zero trust journey. Within just a couple of minutes, you’ll transform the way your organization manages database access, security, and auditability.



Top comments (0)