Ransomware attacks continue to increase, using techniques that are growing more and more sophisticated and targeted. Security and risk management leaders need to look beyond just the endpoints to help protect the organization from ransomware.
What exactly is Ransomware:
Ransomware is malware that employs encryption to hold a victim’s information at ransom. A user or organization’s critical data is encrypted so that they cannot access files, databases, or applications. A ransom is then demanded to provide access. Ransomware is often designed to spread across a network and target database and file servers, and can thus quickly paralyze an entire organization.
How does ransomware work?
Ransomware uses asymmetric encryption. This is cryptography that uses a pair of keys to encrypt and decrypt a file. The public-private pair of keys is uniquely generated by the attacker for the victim, with the private key to decrypt the files stored on the attacker’s server. The attacker makes the private key available to the victim only after the ransom is paid, though as seen in recent ransomware campaigns, that is not always the case. Without access to the private key, it is nearly impossible to decrypt the files that are being held for ransom.
Many variations of ransomware exist. Often ransomware (and other malware) is distributed using email spam campaigns or through targeted attacks. Malware needs an attack vector to establish its presence on an endpoint. After presence is established, malware stays on the system until its task is accomplished.
After a successful exploit, ransomware drops and executes a malicious binary on the infected system. This binary then searches and encrypts valuable files, such as Microsoft Word documents, images, databases, and so on. The ransomware may also exploit system and network vulnerabilities to spread to other systems and possibly across entire organizations.
Once files are encrypted, ransomware prompts the user for a ransom to be paid within 24 to 48 hours to decrypt the files, or they will be lost forever. If a data backup is unavailable or those backups were themselves encrypted, the victim is faced with paying the ransom to recover personal files.
Why is ransomware spreading?
Ransomware attacks and their variants are rapidly evolving to counter preventive technologies for several reasons:
• Easy availability of malware kits that can be used to create new malware samples on demand
• Use of known good generic interpreters to create cross-platform ransomware (for example, Ransom32 uses Node.js with a JavaScript payload)
• Use of new techniques, such as encrypting the complete disk instead of selected files
Today’s thieves don’t even have to be tech savvy. Ransomware marketplaces have sprouted up online, offering malware strains for any would-be cybercrook and generating extra profit for the malware authors, who often ask for a cut in the ransom proceeds.
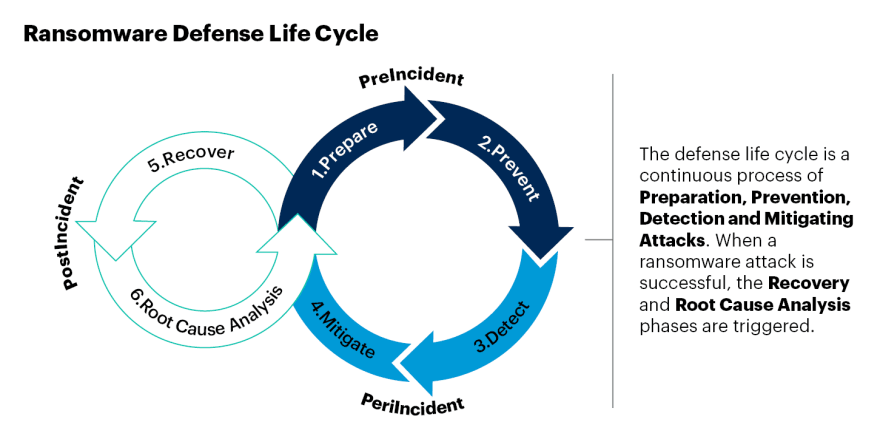
Ransomware Defense Life Cycle
How to defend against ransomware:
To avoid ransomware and mitigate damage if you are attacked, follow these tips:
• Back up your data. The best way to avoid the threat of being locked out of your critical files is to ensure that you always have backup copies of them, preferably in the cloud and on an external hard drive. This way, if you do get a ransomware infection, you can wipe your computer or device free and reinstall your files from backup. This protects your data and you won’t be tempted to reward the malware authors by paying a ransom. Backups won’t prevent ransomware, but it can mitigate the risks.
• Secure your backups. Make sure your backup data is not accessible for modification or deletion from the systems where the data resides. Ransomware will look for data backups and encrypt or delete them so they cannot be recovered, so use backup systems that do not allow direct access to backup files.
• Use security software and keep it up to date. Make sure all your computers and devices are protected with comprehensive security software and keep all your software up to date. Make sure you update your devices’ software early and often, as patches for flaws are typically included in each update.
• Practice safe surfing. Be careful where you click. Don’t respond to emails and text messages from people you don’t know, and only download applications from trusted sources. This is important since malware authors often use social engineering to try to get you to install dangerous files.
• Only use secure networks. Avoid using public Wi-Fi networks, since many of them are not secure, and cybercriminals can snoop on your internet usage. Instead, consider installing a VPN, which provides you with a secure connection to the internet no matter where you go.
• Implement a security awareness program. Provide regular security awareness training for every member of your organization so they can avoid phishing and other social engineering attacks. Conduct regular drills and tests to be sure that training is being observed.
Anatomy of a Ransomware Attack

Final and more important:
Why shouldn’t I just pay the ransom?
When faced with the possibility of weeks or months of recovery, it might be tempting to give in to a ransom demand. But there are several reasons why this is a bad idea:
• You may never get a decryption key. When you pay a ransomware demand, you’re supposed to get a decryption key in return. But when you conduct a ransomware transaction, you’re depending on the integrity of criminals. Many people and organizations have paid the ransom only to receive nothing in return—they’re then out tens or hundreds or thousands of dollars, and they still have to rebuild their systems from scratch.
• You could get repeated ransom demands. Once you pay a ransom, the cybercriminals who deployed the ransomware know you’re at their mercy. They may give you a working key if you’re willing to pay a little (or a lot) more.
• You may receive a decryption key that works—kind of. The creators of ransomware aren’t in the file recovery business; they’re in the moneymaking business. In other words, the decryptor you receive may be just good enough for the criminals to say they held up their end of the deal. Moreover, it’s not unheard of for the encryption process itself to corrupt some files beyond repair. If this happens, even a good decryption key will be unable to unlock your files—they’re gone forever.
• You may be painting a target on your back. Once you pay a ransom, criminals know you’re a good investment. An organization that has a proven history of paying the ransom is a more attractive target than a new target that may or may not pay. What’s going to stop the same group of criminals from attacking again in a year or two, or logging onto a forum and announcing to other cybercriminals that you’re an easy mark?
• Even if everything somehow ends up fine, you’re still funding criminal activity. Say you pay the ransom, receive a good decryptor key, and get everything back up and running. This is merely the best worst-case scenario (and not just because you’re out a lot of money). When you pay the ransom, you’re funding criminal activities. Putting aside the obvious moral implications, you’re reinforcing the idea that ransomware is a business model that works. (Think about it—if no one ever paid the ransom, do you think they’d keep putting out ransomware?) Bolstered by their success and their outsized payday, these criminals will continue wreaking havoc on unsuspecting businesses, and will continue putting time and money into developing newer and even more nefarious strains of ransomware—one of which may find its way onto your devices in the future.
Thank you very much for your time.








Top comments (0)