Having the right tools at your disposal can be a bit of a challenge when there are so many open-source tools out there available on the web.
Therefore, I decided to share some of my favorite tools, scripts, and blogs with you in the AWS Toolbox 🧰
Here is what you'll find in the AWS Toolbox.
Bash & Python scripts
You'll find over 20 Bash and Python scripts that you can use to run to avoid repetitive tasks.
As an example, the multi-account execution script gives you the ability to run Boto3 commands on all accounts which are specified in the AWS account list.
See the code below for details:
```python showLineNumbers
https://github.com/towardsthecloud/aws-toolbox
This script gives you the ability to run Boto3 commands on all accounts which are specified in the aws_account_list
import boto3
aws_account_list = ["111111111111", "222222222222", "333333333333"]
def role_arn_to_session(args):
client = boto3.client("sts")
response = client.assume_role(args)
return boto3.Session(
aws_access_key_id=response["Credentials"]["AccessKeyId"],
aws_secret_access_key=response["Credentials"]["SecretAccessKey"],
aws_session_token=response["Credentials"]["SessionToken"],
)
This decides what role to use, the name of the session you will start, and potentially an external id.
The external id can be used as a passcode to protect your role.
def set_boto3_clients(account_id):
return role_arn_to_session(
RoleArn="arn:aws:iam::" + account_id + ":role/your-rolename-to-assume",
RoleSessionName="your-rolename-to-assume",
)
This is an example function which deletes evaluation results for a specific config rule.
You can create your own Boto3 function which you want to execute on mutliple accounts.
def delete_awsconfig_rule_evaluations(awsconfig):
return awsconfig.delete_evaluation_results(ConfigRuleName="SHIELD_002")
def lambda_handler(event, context):
for account_id in aws_account_list:
run_boto3_in_account = set_boto3_clients(account_id)
# You can use run_boto3_in_account as if you are using boto in another account
# For example: s3 = run_boto3_in_account.client('s3')
awsconfig = run_boto3_in_account.client("config")
delete_awsconfig_rule_evaluations(awsconfig)
if name == "main":
lambda_handler({"invokingEvent": '{"messageType":"ScheduledNotification"}'}, None)
## Third-party AWS tools
This section in the repository contains links to popular tools and **hidden gems 💎** that you might now know about yet that automate or simplify the usage of AWS in the console, CLI, or API's.
An example of a popular tool that helps you set up and deploy AWS ECS containers relatively easily in an automated way is [AWS Copilot CLI](https://github.com/aws/copilot-cli).
[The AWS Copilot CLI](https://towardsthecloud.com/aws-copilot-cli-deploy-containers-tutorial) is a tool for developers to build, release and operate production-ready containerized applications on Amazon ECS and AWS Fargate.
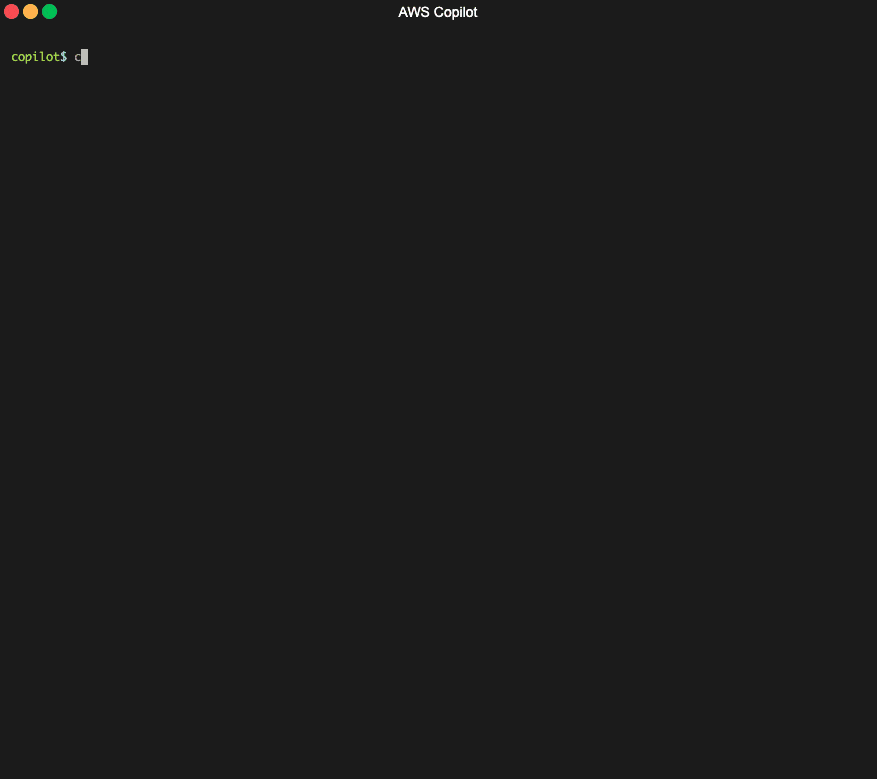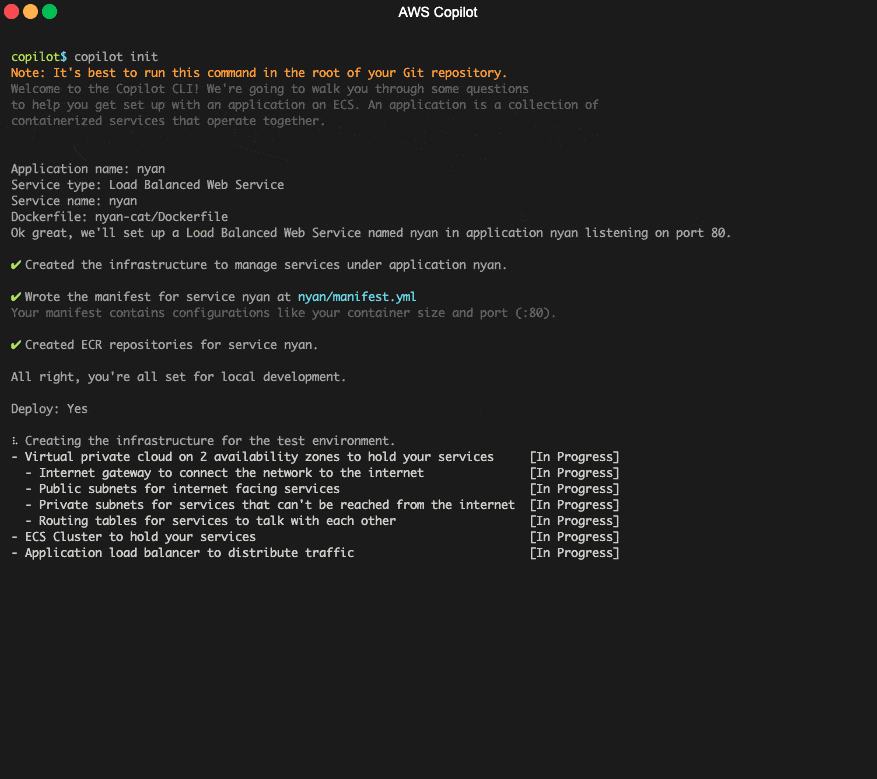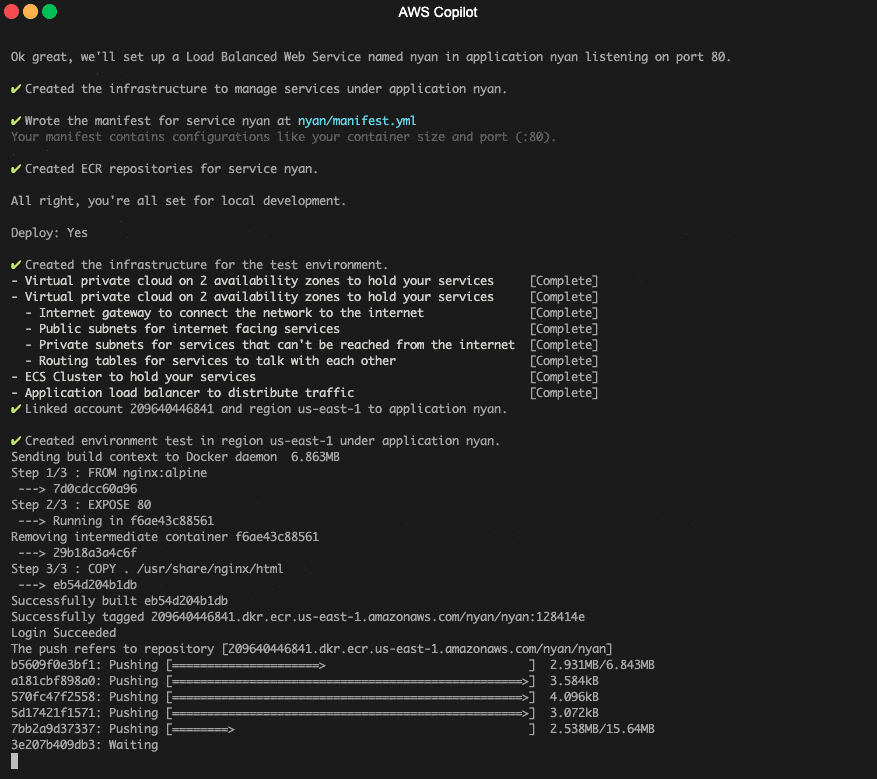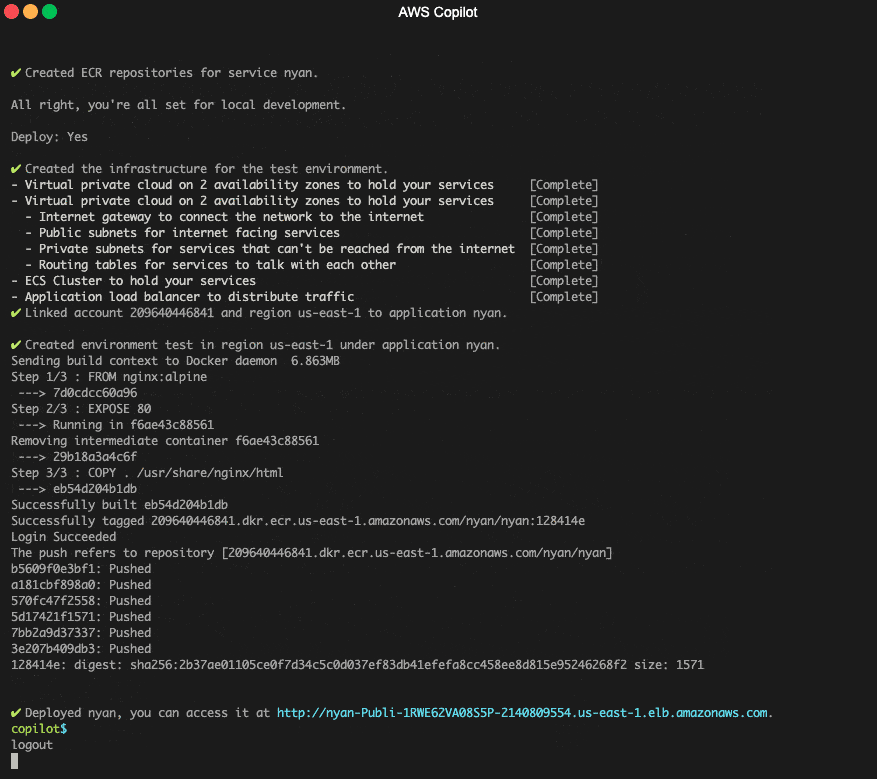
AWS Copilot CLI creating an AWS Fargate service example
An example of a hidden gem 💎 is [steampipe](https://github.com/turbot/steampipe). This tool allows you to query Cloud resources in a SQL-like fashion.
I dare to say that if you wish to query multiple AWS resources, this tool is way faster and easier to use than the default AWS CLI!
You can instantly run query cloud APIs using SQL like so:
select
title,
create_date,
mfa_enabled
from
aws_iam_user
The example query will return all IAM users including their creation date and if MFA has been enabled:
```bash
+-----------------+---------------------+-------------+
| title | create_date | mfa_enabled |
+-----------------+---------------------+-------------+
| pam_beesly | 2005-03-24 21:30:00 | false |
| creed_bratton | 2005-03-24 21:30:00 | true |
| stanley_hudson | 2005-03-24 21:30:00 | false |
| michael_scott | 2005-03-24 21:30:00 | false |
| dwight_schrute | 2005-03-24 21:30:00 | true |
+-----------------+---------------------+-------------+
But the real power of this tool is the use of mods! A Steampipe mod is a collection of related Steampipe resources such as queries, controls, and benchmarks.
You can simply download one of the several mods from the Steampipe Hub or create one yourself.
A good example of a mod that you can use for AWS is the AWS Compliance Mod. This mod can run individual configuration, compliance and security controls, or full compliance benchmarks for AWS Foundational Security Best Practices.
Basically, that means it can run a full security health check on your AWS accounts and produce a report based on the findings. This makes this tool invaluable in helping you protect your AWS accounts.
Blogroll
This section contains a collection of AWS blogs that contain helpful tips and tricks.
| Blog title | Description |
|---|---|
| AWS Security | The latest AWS security, identity, and compliance launches, announcements, and how-to posts. |
| AWS DevOps | The latest AWS DevOps announcements, and how-to posts. |
| Netflix Techblog | Learn about Netflix's world-class engineering efforts, company culture, product developments, and more. |
| Last week in AWS | We're the internet's only snarky, sarcastic resource for literally anything and everything AWS… and we know it. |
Contributions
All contributions are welcome! So if you have a Bash or Python script lying around, feel free to create a Pull Request! Read how you can contribute by reading the contribution guidelines
Join my newsletter for real-world insights, actionable strategies, and lessons learned the hard way on my journey building a successful AWS Cloud Consulting business, delivered to your inbox.



Top comments (0)