Level 200
Table of Contents
In previous posts you can find some examples about how to use AWS CDK and security at scale for application deployments in AWS, now suppose that you need use cloud environments for control and manage those deployments using just the tools require for your organization, manage and audit developer’s sessions and control traffic. Furthermore, you need to homologate and deploy different environments with custom tools, SDKs, plugins, and software. In this series you will learn how the AWS services can help you to accomplish this task, some alternatives, applying security in depth and IaC.
If you want to explore Cloud9 and end to end development environment in AWS use AWS Codestar.
AWS Cloud9 is the principal service that can help you to solve this challenge, a cloud-based IDE that allows you to write, execute, and debug code through the web browser. AWS Cloud9 contains pre-installed software and tools for language such as Python, Ruby, Go, PHP and others, AWS CLI, and direct integration with services such as AWS Lambda and CodeCommit. Key features of AWS Cloud9 include an integrated code debugger, built-in terminal, collaborative chat and editing, and connectivity to any Linux server platform. To know more about these features, you can read the service’s details.
Also, you can use AWS Cloud9 as backup of your local IDE or emergency IDE.
There are two types of scenarios for deploying these environments:
1.Environment where the connection is through SSH, at this point the security groups will have an access rule to 22 to a set of IPs. This environment can be configured from a new instance or to an existing server.
2.Environment using AWS Systems Manager for connection. In this scenario, security groups will have no inbound rules, and through SSM Agent communication between cloud9 and the managed Amazon EC2 instance is ensured.
According to requirements the best option is Environment using AWS Systems Manager for connections, because the manage EC2 instance wouldn’t be expose to internet and the connection for management keep secure with SSM agent.
Before the hands on remember some key advantages to use Session Manager, Session Manager provides a secure and auditable way to access compute nodes, not only for Amazon EC2, but also for services such as Fargate and CodeBuild, in addition:
1.It is compatible with Linux and Windows operating systems.
2.Eliminates the need to create bastion hosts, add exceptions to the firewall, and manage SSH keys.
3.Centralizes access controls via IAM.
4.Save session activity and send logs to Amazon Cloudwatch logs, S3, and/or CloudTrail.
5.Improves the security posture for instance management by using VPC interface endpoints and preventing communication from going online.
6.It enables investigation and remediation of DevOps teams and incident resolution through instant and secure access.
Hands On
Requirements
- cdk >= 2.51.1
- AWS CLI >= 2.7.0
- Python >= 3.10.4
- Pytest >= 7.1.3
- cdk-nag >=2.18.44
- checkov >= 2.1.229
AWS Services
- AWS Cloud Development Kit (CDK): is an open-source software development framework to define your cloud application resources using familiar programming languages.
- AWS Identity and Access Management (IAM): Securely manage identities and access to AWS services and resources.
- AWS IAM Identity Center (Successor to AWS Single Sign-On): helps you securely create or connect your workforce identities and manage their access centrally across AWS accounts and applications.
- AWS CodeCommit: secure, highly scalable, managed source control service that hosts private Git repositories.
- AWS Key Management Service (AWS KMS): lets you create, manage, and control cryptographic keys across your applications and more than 100 AWS services.
- AWS CloudFormation: Speed up cloud provisioning with infrastructure as code
- AWS Identity and Access Management (IAM): Securely manage identities and access to AWS services and resources.
- AWS Cloud 9: A cloud-based IDE that lets you write, run, and debug your code through a browser.
- AWS Lambda: A serverless compute service that lets you run code without provisioning or managing servers, build workload-based cluster scaling logic, maintain event integrations, or manage runtimes.
- AWS Systems Manager – This is the AWS Operations Center. Systems Manager provides a unified user interface so you can track and resolve operational issues across all your AWS applications and resources from one place.
Solution Overview
Conditions
- Source code can only be cloned from a development VPC (DevVPC).
- AWS Cloud9 environments can only be created in a DevVPC in central account.
- VPC flow logs are enabled on DevVPC.
User management
- Amazon Single Sign-On, AD, IAM users, etc.
- Developers are assigned an IAM role.
- The user’s sessions should be logged and audited.
Developer IAM role
- Gives access to source code in CodeCommit
- Allows using AWS Cloud9

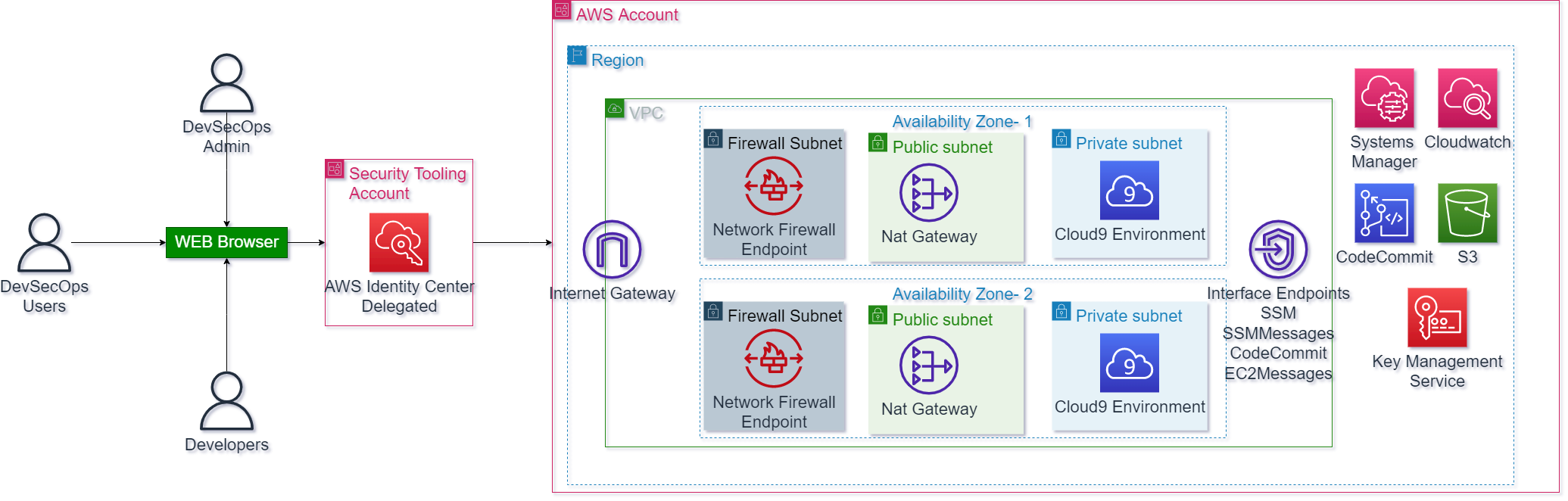
Figure 1. Solution overview- Secure Cloud Native IDE
Figure 1 shows the reference architecture diagram for this scenario. You can see that the login to the environment will be through SSO, use of IAM for custom roles and integration with CodeCommit that allows us to clone without the need for additional steps our repositories within the environment, network segmentation, the use of AWS Network Firewall and VPC Endpoints to connect privately to AWS Systems manager and thus be able to apply more controls aligned with the principle of minimum exposure and security in depth. In order to guarantee the traceability and auditing of the sessions, the Session Manager preferences are configured to send the encrypted logs to an S3 Bucket and Cloudwatch which will allow to the security team to analyze and automate to respond to any event or unwanted behavior of our users on the environments.
For other hand, the CDK code have some custom actions for managing and add features to your environment. For example,
Figure 2 shows a diagram of the main components of the CDK project, we can see three custom Cloudformation resources that correspond to the lambdas functions responsible for:
- Resize the disk of the Cloud9 instance.
- Assign a custom role, it can be a role with managed policies or a custom role.
- Install additional custom tools that are not in the default environment. This boostrap command just run one time. For this task we will use the Run-Command functionality within Systems Manager. If you want to run every time there are many alternatives, for example, modify the custom resource events for run after run command actions after each code update
If you want to encrypt the EBS volume, please enable default encryption for each region and account.
Step by Step
You can find the code here.
velez94 / cdk_c9_secure_ides
Secure IDE in AWS
Table of Contents
Cloud-native development with AWS – Part 1 – Secure IDEs Cloud9 Setup
AWS Cloud9 is the principal service that can help you to solve this challenge, a cloud-based IDE that allows you to write, execute, and debug code through the web browser. AWS Cloud9 contains pre-installed software and tools for language such as Python, Ruby, Go, PHP and others, AWS CLI, and direct integration with services such as AWS Lambda and CodeCommit. Key features of AWS Cloud9 include an integrated code debugger, built-in terminal, collaborative chat and editing, and connectivity to any Linux server platform. To know more about these features, you can read the service’s details.
Solution Overview
Figure 1. Solution overview- Secure Cloud Native IDE
Please visit https://dev.to/avelez For more!
How to
The
cdk.jsonfile…
1- Understand the project structure.
The CDK project has the following structure, as is usual the project properties are in yaml file in project_configs folder.
.
├── app.py
├── cdk.context.json
├── cdk.json
├── cdk.out
├── __init__.py
├── project_configs
│ ├── environment_options
│ │ ├── environment_options_example.yaml
│ │ └── project_1
│ ├── environment_options_example.yaml
│ ├── helpers
│ │ ├── helper.py
│ │ ├── __init__.py
│ │ ├── project_configs.py
│ ├── images
│ │ ├── DevSecOps-labs-Cloud-native development with AWS-ArchOverview.png
│ │ └── diagram.png
│ ├── __init__.py
│ └── __init__.cpython-310.pyc
├── README.md
├── requirements-dev.txt
├── requirements.txt
├── source.bat
├── src
│ ├── cdkv2_secure_ides_c9_aws_stack.py
│ ├── __init__.py
│ ├── lib
│ │ ├── customs
│ │ ├── ides
│ │ ├── __init__.py
│ │ ├── cdkv2_secure_ides_c9_aws_stack.cpython-310.pyc
│ └── stacks
│ ├── __init__.py
│ ├── network
└── tests
├── __init__.py
└── unit
├── __init__.py
└── test_cdkv2_secure_ides_c9_aws_stack.py
2- Modify project properties
For this setup the project properties are in project_configs/environment_options/project_1/environment_options.yaml, the code is created for deployment and manage many environments in different accounts you can setup each one creating a folder like project_configs/environment_options/<project_name>/environment_options.yaml, and setup an environment variable for synth and deploy. Also, you can create many environments for the same account in the environment_props block.
export props_paths='../environment_options/project_1/environment_options.yaml'
Create a environment options file like:
project_name: 'CloudNativeIDEs'
# DevSecOps Account Environment setup
devsecops_account: "123456789012"
devsecops_region: "us-east-1"
network_definitions:
create_vpc: True
vpc_cidr: "192.168.0.0/16"
max_azs: 2
nat_gateways: 0
subnet_configuration:
- name: "public"
cidr_mask : 24
subnet_type : "public"
- name: "ides"
cidr_mask : 24
subnet_type : "isolate"
environment_props:
- environment_name: 'DevSecOpsIDE-Project'
description: "DevSecOps IDE Blog"
instance_size: 't3.small'
automatic_stop_time_minutes: 30
resize_volume: "True"
ebs_volume_size: '17'
bootstrap_environment: "True"
bootstrap_commands: 'bootstrap.sh'
subnet_type: 'public'
owner_arn: 'arn:aws:sts:: 123456789012:assumed-role/AWSReservedSSO_LabxlDevSecOpsRW_a4790b6a3d6c520a/DevSecOpsAdm'
codecommit_repos:
- 'MyREPO'
# Tags definitions align with enterprise instructions
tags:
- key: 'Project'
value: 'SecureIdes'
- key: 'Stack'
value: 'SecureIdes'
- key: 'Environment'
value: 'Prod'
In this example you can find the network definitions and environment definitions blocks. You can enable or disable custom actions and use codecommit repositories, if you don want clone codecommit repositories comment the lines.
The boostrap_commands parameter indicates the path of bootstrap shell script file. For example:
#!/bin/bash
sudo yum update -y
sudo yum upgrade -y
sudo yum install -y yum-utils
echo "bootstrapping environment"> /home/ec2-user/environment/bootstrap-file.txt
This file is in the same project folder, use with precaution and scripts certificated for correct deployment.
3- Synth code and deploy.
Verify the stacks.
$ cdk ls
CdkSecureIDEsVPCStack
Cdkv2SecureIDEsCloud9AWSStack
The VPC stack don’t create a network firewall this task will be posted in other blog, if you want learn more about this service please visit Deployment models for AWS Network Firewall | Networking & Content Delivery (amazon.com)
Setup AWS CLI profile using aws configure command for DevSecOps Account.
aws configure sso --profile labxl-devsecops
SSO start URL [None]: https://my-sso-portal.awsapps.com/start
SSO region [None]:us-east-1
Using a browser, open the following URL:
https://my-sso-portal.awsapps.com/verify
and enter the following code:
QCFK-N451
There are 3 AWS accounts available to you.
Using the account ID 123456789012
The only role available to you is: AWSAdministratorAccess
Using the role name "AWSAdministratorAccess"
CLI default client Region [None]: us-east-2
CLI default output format [None]: json
To use this profile, specify the profile name using --profile, as shown:
aws s3 ls --profile labxl-devsecops
Deploy stacks
$ cdk deploy --all --profile labvel-devsecops
✨ Synthesis time: 6.62s
CdkSecureIDEsVPCStack (DevVPC-CloudNativeIDEs): building assets...
[0%] start: Building 40dae843e204df8b0fc85836a8a344658c2514fa8ae825b2348df12341960f78:105171185823-us-east-1
[100%] success: Built 40dae843e204df8b0fc85836a8a344658c2514fa8ae825b2348df12341960f78:105171185823-us-east-1
CdkSecureIDEsVPCStack (DevVPC-CloudNativeIDEs): assets built
Cdkv2SecureIDEsCloud9AWSStack (CloudNativeIDEs): building assets...
[0%] start: Building 981a709b2daa7c467d8271977457844e940407809bdd5336e235c65df15d0754:105171185823-us-east-1
[0%] start: Building eb5b005c858404ea0c8f68098ed5dcdf5340e02461f149751d10f59c210d5ef8:105171185823-us-east-1
[0%] start: Building 8fbc01afe9d34b7bc70c0e0bba150b818e69346045661a6f2dde080d042234e6:105171185823-us-east-1
[0%] start: Building 496eafd105d8ed7173a71653a09e1ef0d9f49148669222520228b97
...
Confirm for potential sensitive changes
This deployment will make potentially sensitive changes according to your current security approval level (--require-approval broadening).
Please confirm you intend to make the following modifications:
IAM Statement Changes
┌───┬───────────────────────────────┬────────┬──────────────────────────────────────────────────────────────┬─────────────────────────────────────┬───────────┐
│ │ Resource │ Effect │ Action │ Principal │ Condition │
├───┼───────────────────────────────┼────────┼──────────────────────────────────────────────────────────────┼─────────────────────────────────────┼───────────┤
│ + │ ${VPC/flow_logs/IAMRole.Arn} │ Allow │ sts:AssumeRole │ Service:vpc-flow-logs.amazonaws.com │ │
│ + │ ${VPC/flow_logs/IAMRole.Arn} │ Allow │ iam:PassRole │ AWS:${VPC/flow_logs/IAMRole} │ │
├───┼───────────────────────────────┼────────┼──────────────────────────────────────────────────────────────┼─────────────────────────────────────┼───────────┤
│ + │ ${VPC/flow_logs/LogGroup.Arn} │ Allow │ logs:CreateLogStream │ AWS:${VPC/flow_logs/IAMRole} │ │
│ │ │ │ logs:DescribeLogStreams │ │ │
│ │ │ │ logs:PutLogEvents │ │ │
└───┴───────────────────────────────┴────────┴──────────────────────────────────────────────────────────────┴─────────────────────────────────────┴───────────┘
(NOTE: There may be security-related changes not in this list. See https://github.com/aws/aws-cdk/issues/1299)
Do you wish to deploy these changes (y/n)? y
Deployment time is approximately 10-15 minutes due to provisioning the managed EC2 instance, disk size changes, and running custom resources.
Now you can see some evidence in console.

Figure 3. CloudFormation Console.
Figure 3 shows the Stacks and nested stacks for this project.
Figure 4 shows the cloud9 interface with environment properties according to the yaml specifications.
Figure 5 shows the Cloud9 interface, here you can share, add custom plugins, modify IDE properties, inspect AWS resources and more. For example, Figure 6 shows the AWS Toolkit and some resources that you can explore without leave of the IDE.
Clean up
$ cdk destroy --all --profile labxl-devsecops
Are you sure you want to delete: Cdkv2SecureIDEsCloud9AWSStack, CdkSecureIDEsVPCStack (y/n)? y
Cdkv2SecureIDEsCloud9AWSStack (CloudNativeIDEs): destroying...
Enjoy and thanks for reading and sharing!







Top comments (0)