With the world progressing towards cloud-native applications, the cyber threat landscape is also taking a revolutionary turn. As a result, it’s crucial to guard our applications and systems against internal and external security threats.
Most security risks to an organization are caused by insufficient and improper access control that may put the company at risk for fraud, unauthorized access to data and programs, or completely shut down or corrupt the computer servers and services. Therefore, it’s essential to secure organizational resources and information by restricting access and providing only the relevant permission to the appropriate entities to access and manipulate the data in the system.
This article will discuss the three primary access control mechanisms: role-based, claim-based, and permission-based access control, and provide guidance on which approach to select based on your requirements.
What is Access Control?
Access control governs who can access particular data, applications, and resources inside an organization and under what circumstances. Access control lets the right people in and leaves the wrong people out by granting the users an appropriate level of access using different mechanisms.
Organizations use authentication and authorization techniques to verify users. Depending on compliance requirements and security levels, access control models such as role-based, claim-based, and permission-based access controls prevent unauthorized access to sensitive data.
The following sections will review these different models, providing a comprehensive comparison.
Role-based Access Control (RBAC)
Role-based access control (RBAC) limits access (viewing, creating, editing, deleting) based on a user's role and responsibilities within an organization, preventing unauthorized access to critical resources. Therefore, an organization can use RBAC to allow some people, such as system administrators, to create or change files while allowing others to view them. As a result, access to sensitive information is restricted for lower-level users, tightening the organization's security measures for essential data.
Implementing RBAC
The main steps involved in implementing RBAC are as follows:
- Define and determine the most sensitive resources and information that require controlled access.
- Logically group the employees according to the workforce's functions and relationships to identify the organization's key roles.
- Assign proper access rights to the roles based on their responsibilities.
- Conduct periodic audits to check if a role has unnecessary access to a specific system and modify access levels accordingly over time.
Advantages of RBAC
- Flexible: Any organizational structure changes can be applied quickly to users by modifying the corresponding roles.
- Less administration work: Policies can be assigned to user groups instead of manually to individuals.
- Secure: Utilization of the principle of least privilege reduces the risk of a data breach. Integrating third-party users is also more secure with RBAC, as we can give them strictly defined roles and permissions.
Disadvantages of RBAC
- Assigning the appropriate roles can be challenging: Assigning people to ill-fitting roles or creating new roles against policies may lead to security gaps.
- Role explosion: Roles minimize the potential for altering the permissions for a single entity, forcing administrators to create new roles to give an entity a customized set of permissions.
- Less scalable and less dynamic: As the organization grows, RBAC may be difficult to maintain and manage due to the expansion of user categories and lack of compatibility of existing roles with the new organizational structure.
- Coarse-grained and static: RBAC has fixed access rules that ignore other significant factors, such as time, location, or device, and limits access based only on a user's role.
Claims-based Access Control (CBAC)
Organizations may utilize claims-based access control (CBAC), also known as attribute-based access control (ABAC), either as a replacement or a supplement to RBAC to provide more granular access control.
CBAC restricts and provides access to critical resources based on a combination of three factors:
- The user’s identity
- The user's responsibilities
- The context of the action performed.
Attributes or claims are used to identify an entity based on its characteristics and allow you to implement rich, complex access policies more simply. For example, if a user is promoted from marketing to management, their access permission would be modified due to the change in their business attributes rather than because a system administrator explicitly changed the specific user’s role.
Implementing CBAC
The basics steps involved in the CBAC process are:
- Identify the attributes needed to specify access rules: Three main categories of claims are based on the entity.
- Subject/user claims: Characteristics of a user trying to access a resource such as a username, job title, user ID, and security clearance.
- Object/resource claims: Attributes of the resources such as filename, creation date, and ownership.
- Context/environment claims: Environmental characteristics such as time, place, type of communication, and type of device used to access a resource.
Create a set of rules to determine the attributes that allow user access based on the requirements.
The given access to a user if the attributes match the rules specified.
Advantages of CBAC
- Flexible, granular policies: Policies can be precisely defined, targetting specific attributes rather than the roles of the users.
- Dynamic access: Since rules can be specified based on environmental parameters, access control can be done at runtime by evaluating the context and risk.
- Scalable: Access can be easily given to new users without creating new policies or roles by simply assigning the attributes needed to access the resource.
- Secure: With context-sensitive rules, user privacy and resources can be protected based on the situation where access is requested.
Disadvantages of CBAC
- Implementation is time-consuming: Correctly identifying the mapping of authorization policies to attributes may consume time and resources.
- Comparatively complex: Granularity introduces complexity.
Permission-based Access Control
Conceptually, permitting users means granting access to a resource or allowing them to execute a specific operation in a system. Therefore, permission-based access control (PBAC) is a technique that defines the set of actions each user in the organization is allowed to perform on each resource.
The image below illustrates how access is given to three entities using PBAC.
Implementing PBAC
Enforcing PBAC is relatively straightforward compared to RBAC and CBAC. Access rules should be specified for each user as a tuple, indicating the resources and the permitted operations such as view, create, edit, and delete. Therefore, obtaining access rights to a resource means that, at the very least, the entity can read its content.
Advantages of PBAC
- Fine granularity: Permission can be defined flexibly for each entity for each resource in the system.
- Secure: Since customized access levels are defined for each entity, only the least privileges will be given for all users to perform their tasks.
Disadvantages of PBAC
- Less scalable: When the number of users is high, managing permissions for each user individually is impractical.
- Access is static: The permissions are not specified based on the environmental context of the users accessing the resources.
When to Choose Which?
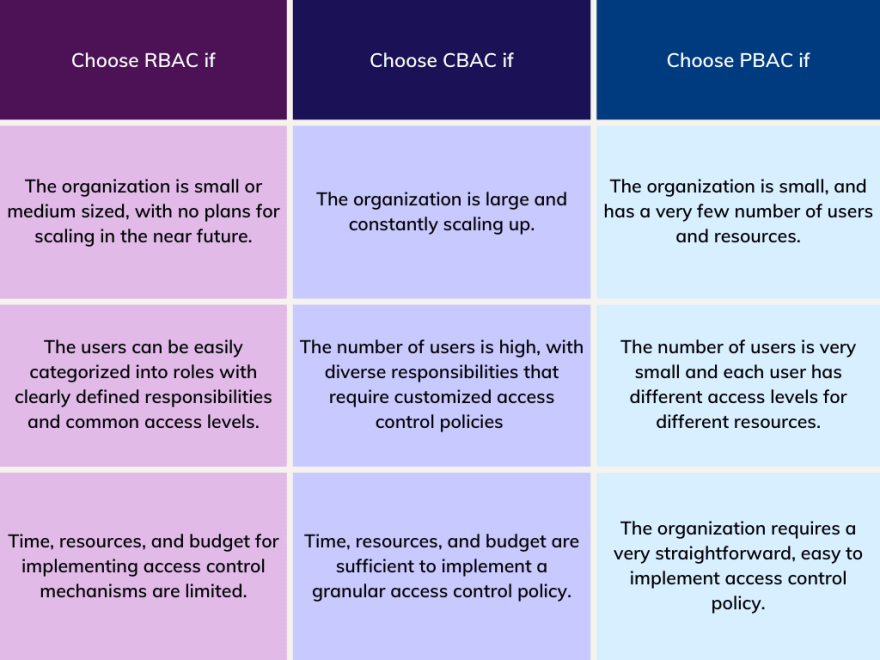
Now that there is a clear understanding of each access control mechanism, let's compare the characteristics to identify the best use cases for each method. The table below shows a comparison of the three methods discussed.
Considering all these differences, here's a summarized set of guidelines for choosing a well-suited access control mechanism for your organization.
Wrapping Up
Access control is an essential step that needs to be taken to help ensure the security of your organizational resources.
RBAC, CBAC, and PBAC are three popular access control mechanisms with pros and cons. This article provides guidance on selecting an access control method based on your organizational structure and resources.
However, remember that these tips are highly generalized, and you might sometimes reap tremendous benefits from combining them rather than implementing a single access control mechanism.
How Amplication Can Help
Amplication provides a role-based permission model that is generated automatically with your code, saving you time setting up authentication and authorization in your app. You can create as many roles as needed and granularly set permissions per data model or specific fields for different roles. All the permissions are automatically enforced in the REST and GraphQL APIs including response filtering on specific fields.
Amplication uses the @nestjs/passport module as middleware to support authentication, providing a rich ecosystem of strategies that implement various authentication mechanisms.
Thank you for reading.









Top comments (0)