Atlassian SAML SSO with Auth0 IdP
In this article we'll look at how to configure Auth0 as SAML 2.0 SSO IdP for Atlassian.
Prerequisite
Inside your Atlassian Organisation you should have:
- A verified domain
- Atlassian Access
Setup
Step 1. Auth0 IdP Client
Create a "Regular Web Application" in Auth0
Step 2. Add Connections to your App
Make sure that correct set of Auth0 connections are associated to your IdP app.
Step 3. Enable SAML2 Addon
Go to application's Addons tab and enable SAML2 Web App.
Step 4. IdP Metadata
Go to Usage section in addon configuration. Here you find information to populate SAML metadata in Atlassian Access.
Step 5. Add SAML Connection in Atlassian
In Atlassian Admin dashboard, go to Organization > Security > SAML single sign-on
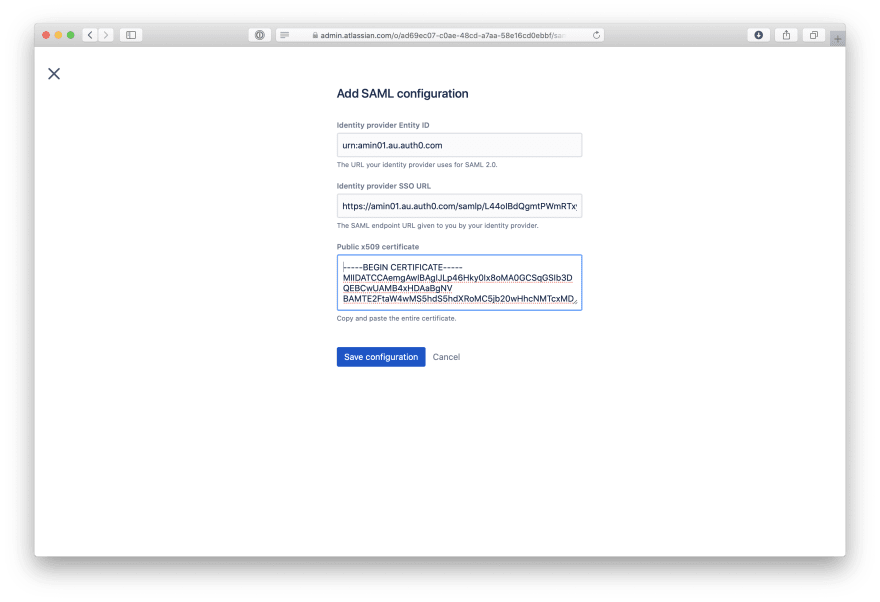
Step 6. Populate Configuration
Copy configs from addon usage page (step 4) to SAML configuration.
-
Identity provider Entity ID=>urn:TENANT.auth0.com -
Identity provider SSO URL=>https://TENANT.auth0.com/samlp/APP_ID -
Public x509 certificate=> Content from tenant's/pemhttps://TENANT.auth0.com/pem
Step 7. Get SP Assertion Consumer Service URL
Once configuration saves, you'll see a summary page, copy SP Assertion Consumer Service URL
Step 8. Configure Application Callback URL in Auth0 SAML2 Addon
Go back to Auth0 dashboard for your application's SAML2 addon setup tab and
paste:
-
SP Assertion Consumer Service URL=>Application Callback URL
And populate metadata mapping file into Settings section and Save
{
"mappings": {
"user_id": "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier",
"given_name": "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname",
"family_name": "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname"
},
"nameIdentifierProbes": [
"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress",
"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier",
"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name"
],
"nameIdentifierFormat": "urn:oasis:names:tc:SAML:2.0:nameid-format:email"
}
Step 9. Try Sign in with Verified Domain Email
Visit id.atlassian.com and login with a user@your-verified-domain.com











Top comments (0)