Hello Readers!
I know we all want to skip to these basics and directly want to jump to the place where there are codes, tools, and tweaks that will be applied to start all the sneaky tech we have been boasting about from the beginning. Perhaps I’m eager too, to start covering those topics. But, we know that without having any building blocks the further topics are gonna look greek Zuzu to you.
So let’s start with the Basic Concepts of Networking. Starting with the OSI model and then further with some necessary packet headers, protocols and port numbers.
OSI (Open System Interconnection) MODEL
It’s a 7-layer reference model that is used by all the communicaion systems to maintain a standard for every function they perform. This helps them to communicate easily with each other and also for understanding and categorization of the same. This also helps the communication system device vendors to build an architecture for the same amicably.
So, I would like to keep this explanation in the form of a string of situations and would try to cover the concepts for all of them as we proceed.
Have you ever used an online banking system or any social media website?
When you connect to the internet or when you put the ethernet cable that comes under the Physical Layer(1).
Physical Layer consists of the physical transmission medium for transferring the raw and unstructured data.
Now when the network connectivity is established, how the data would be encapsulated for the further layer and medium of access over the network in the responsibility of the Data Link Layer(2).
Data Link Layer provides the node-to-node transfer. It is responsible for the protocol to be established. This layer has two sublayers.
MAC(Media Access Control) Layer:- This layer has it’s role to control how the devices gain access to medium and permission to transmit data.
LLC(Logic Link Control) Layer:- this identifies to encapsulate the network layer protocol, checks error and synchronizes.
When the data is encapsulated it gets converted to the packets at Layer 3 — The Network Layer(3). In this layer, the packets can travel to different networks as well.
Network Layer converts the data into packets and helps it to send to various networks. The data on this layer travels using IP addresses, with the help of which the data reaches its destination.
Now when the data packet is being sent over the network, there will be protocols that help them over the network and ensure that how the data is being transferred. Now the Transport Layer(4) is responsible for it.
The transport layer provides the functional and procedural means of transferring variable-length data sequences from a source to a destination host while maintaining the quality of service functions. They can ensure the reliability of the link as they do error checking during Segmentation/Desegmentation, with the help of which they can resend the packet from where it failed.
There are two types of protocols in it.
TCP(Transfer Control Protocol):- This protocol ensures that the data is transferred. Thus, this uses a 3-way handshake methodology.

This makes the TCP a reliable source to send messages, for the highest priority. For example, the Net banking Transaction, log in and etc.
UDP(User Datagram Protocol): This protocol is not so reliable, it doesn’t ensure that the packet has reached the destination. Therefore not so important things are sent over UDP, for example, VoIP packets.
Now, when the data is transferred, a session is created between you and your banking server. The process of creating a session and providing you with a secured Session-Id is done by the Session Layer(5).
The session layer is responsible for the dialogues between the systems. It can establish the procedures for checkpointing, restarting or suspending an ongoing connection.
Now, when the session has been established the data is shown into several forms and using various languages. Thus this is also known as the syntax layer. This provides the interdependency of choosing the form of representation of data. This is done by the Presentation Layer(6). The language in which the page of the Net-Banking is written comes in this layer.
Data can be written in various forms and languages like Python, XML, etc and then are further encoded in various ways. This layer presents the structures of the various encoding rules.
When the encoding has been done, it’s time for the visibility of the data. The data can be shown on various codecs and applications which is considered into Application Layer(7). Therefore, when you see that Net Banking webpage, that is shown by the Application Layer.
Application-layer functions typically include identifying communication partners, determining resource availability, and synchronizing communication. When identifying communication partners, the application layer determines the identity and availability of communication partners for an application with data to transmit. The most important distinction in the application layer is the distinction between the application-entity and the application.
TCP (Transfer Control Protocol) Model
The TCP Model is also a reference model that came after the OSI Model. The TCP model came to cut-short the OSI Model and reduce the strict boundaries at each layer. Thus this model was made of 4 layers including and combining some of the OSI Layers into one.
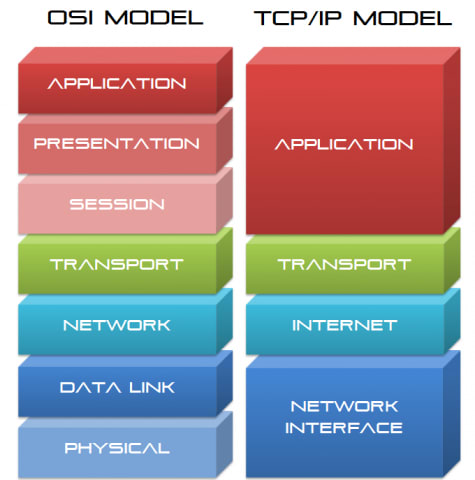
The final scenario of the OSI Model and the TCP Model is given in the figure below. This shows the protocols on each layer of both the models.
If you have any doubts regarding any of the layers, feel free to ping in the comment section below.









Top comments (0)