Vulnerability Description and Impact
A security issue was discovered in Kubernetes and disclosed on June 1, 2020, as CVE-2020-8552.
The vulnerability enables an attacker to gain access to data from services that are connected to the host network of the cluster’s manager, and although the attack is not simple to execute, it can remotely bypass authorization controls and break confidentiality.
Are You Vulnerable?
The vulnerability affects kube-controller-manager which is part of Kubernetes control plane:
- V1.18.0, v1.17.0 - v1.17.4, v1.16.0 - v1.16.8, and versions earlier than v1.15.11
The affected volume types that can be abused as part of the attack execution, as explained below, are:
GlusterFS, Quobyte, StorageFS, ScaleIO.
The vulnerability is patched in Kubernetes versions:
- V1.18.1+, v1.17.5+, v1.16.9+, v1.15.12+
Remediation & Mitigation
Prior to upgrading, these vulnerabilities can be mitigated by adding endpoint protections on the master or restricting usage of the vulnerable volume types and restricting StorageClass write permissions through RBAC.
Technical Breakdown of the Exploit
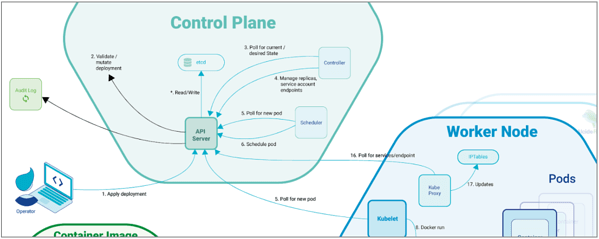
According to Kubernetes’ GitHub issue, this vulnerability allows certain authorized users to access endpoints within the master's host network, such as link-local or loopback services.
By exploiting this vulnerability, these users can leak arbitrary information (up to 500 bytes per successful malicious request) from such unprotected endpoints.
The attack’s steps are:
- An attacker with permissions to do so creates a pod
- The attacker attaches a volume to the pod. This volume can be one with certain built-in Volume types (GlusterFS, Quobyte, StorageFS, ScaleIO). An attacker with permissions to create a StorageClass can use this capability to the same effect.
- By using the volume attachment or storage class creation, the attacker makes the kube-controller-manager k8s component make GET requests or POST requests without an attacker-controlled request body from the master's host network.
Automatic Vulnerability and Attack Detection with Alcide kAudit
The Kubernetes API Server logs every request it receives in its audit log. Of specific relevance to the detection of attempts to exploit CVE-2020-8555, actions like creation of a new pod, creation of a StorageClass, and sending of any requests to the API server leave traces in the audit log.
Alcide kAudit automatically monitors and analyzes these audit logs. It creates and dynamically updates a profile of the normal behavior in the cluster. By comparing in real-time this profile to the audit log, kAudit can detect anomalous behavior that is associated with attempts to attack the k8s infrastructure of a cluster.
kAudit can detect anomalous behavior related to attempts to exploit CVE-2020-8555 at several points along the attack chain:
- Attacker creates a pod
- Attacker creates a StorageClass
- kube-controller-manager sends unusual requests to API-Server
- Unusual increase in unauthorized requests or other irregular status in responses, when an attacker attempts to execute the previous steps.
By combining correlated anomalies to an incident associated with the attacking user, which in this case is the one that creates the pod and StorageClass, Alcide kAudit can alert security teams that an attack was attempted and focus their attention on the relevant users, resources and actions to investigate.
Like other security tools, kAudit also enables the user to configure rules to filter specific entries in the audit log that are interesting for compliance and security investigation. However, in this case, even if the user happens to create rules that identify specific actions that are part of the attack, it will be difficult and time-consuming for a security expert to link these traces of the attack and to create a holistic understanding of it, as regular cluster activity also often creates pods, creates StorageClass, sends requests from the kube-controller component to the API server, or occasionally sends unauthorized requests.
On the other hand, the automated machine learning algorithm used by Alcide kAudit will sift through the log and focus the expert’s attention on the security incident and anomalous behavior that stands out against this noisy background.
Automatic Detection of Vulnerable Clusters with Alcide Advisor
Alcide Advisor is a Kubernetes multi-cluster vulnerability scanner that covers rich Kubernetes and Istio security best practices and compliance checks such as Kubernetes vulnerability scanning, hunting misplaced secrets, or excessive secret access, and many more security configuration and compliance checks.
With Alcide Advisor users can:
- Identify the vulnerable clusters for this vulnerability (as well as other CVEs)
- Define StorageClass whitelist and identify violations of this list.
- Identify the components, as well as ServiceAccounts that have RBAC permissions to create pods.
Conclusion
Kubernetes, like any software, has bugs and vulnerabilities. Leveraging Kubernetes as a cloud-native application infrastructure requires operators to monitor and secure all the moving parts, whether these are the application workloads or the platform and infrastructure components.
Alcide Advisor can identify vulnerable clusters and understand the risk surface associated with CVE-2020-8555, as well as mitigate it. With Alcide kAudit, machine-learning driven dynamic profiling is used to detect actual attempts to exploit known weaknesses such as CVE-2020-8555, as well as detecting attacks targeting new and unknown vulnerabilities.
Try Alcide's security solution with a 14-day trial





Top comments (0)