How can you avoid common mistakes when building a SaaS admin panel? We’ll outline some pitfalls and potential solutions specifically for all you SaaS builders out there!
What happens when you’re building a SaaS app that has more than a few customers? At some point, the inevitable happens! Your sales and customer success people come to the development team with requirements like:
- Show me which accounts are actively used
- Allow me to enter a customer account for technical support
- Enable or disable a specific feature flag for some account
- Some users cannot log in, can you tell me what method they use to authenticate?
- I have a reseller and they need access to their subaccounts
- I need to extend a free trial for an account
- An account needs a specific config that only customer success agents should be able to set up
- Show me the total MRR for a specific group of customers.
A variety of tools can cover some of these use cases. PLG tools like Segment and journy.io can track activity. Maybe you use a feature flag service such as LaunchDarkly. Stripe or Chargebee might manage some of the billing-related aspects. Meanwhile, problems related to authentication might be visible in your Auth0 account. However, it’s unlikely that you’re using all these platforms. Even if you are, you probably can’t cover some use cases.
The solution is building a custom admin panel. There seem to be some frameworks and commercial services available to start quickly. But, how do you go about picking one vs building your own from scratch?
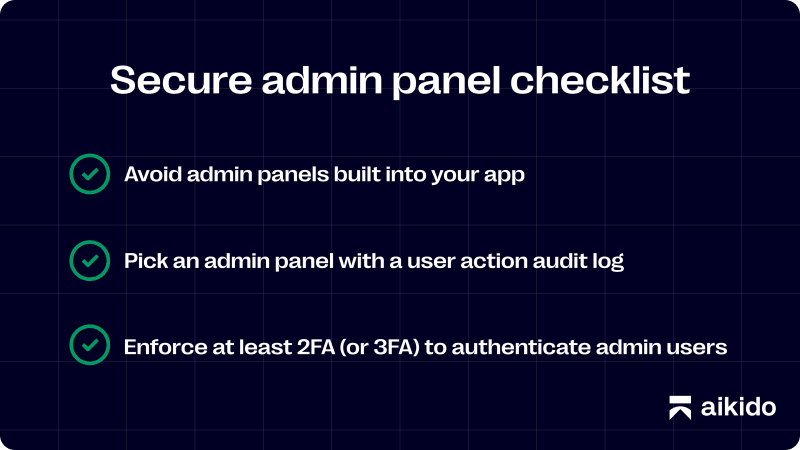
Avoid admin panels built into your app
As a first principle, we’d advocate avoiding any admin panel injected into your main app’s code, as ActiveAdmin does. This has many disadvantages:
- New admin API routes can likely be detected in your app’s client code and attackers can probe or attack this vulnerability
- You’ll likely end up with multiple types of users inside of one codebase, complicating access control reviews
- Adding extra protection features, such as restricting access from a single IP address, will be a lot harder
- If there’s a critical issue detected in the admin panel code, it’s harder to take it offline without taking your app offline.
Apps that do not follow this principle have a higher chance of ending up in Slashdot stories. Here’s one: https://yro.slashdot.org/story/23/01/09/221207/researchers-track-gps-location-of-all-of-californias-new-digital-license-plates. Notably, this story demonstrates that it’s possible to upgrade a user account to a super admin account that can view data from other users.
Pick an admin panel with a user action audit log
In case it has to be said, that means your admins will need to authenticate with separate user accounts. (No logging in with a shared password using support@app.io !). What’s the advantage of this? If any sensitive account settings are updated, you can find out later who made the change.
Enforce at least 2FA (or 3FA) to authenticate admin users
Choose an admin panel solution that allows you to add extra factors on top of 2FA such as IP restrictions or access via other zero-trust solutions.
Bonus: Use Content Security Policy (CSP) headers to block unknown javascript
Blocking unknown javascript is critical, especially on internal admin portals. Below, an example of how Apple was vulnerable to email injection vulnerability, which could’ve been solved with simple CSP headers.
https://twitter.com/samwcyo/status/1738991457627717913
Concluding thoughts on building a secure admin panel
Yes, it’s possible to build a safe admin panel for your app. You’ll have to pick either a framework to help you or an existing SaaS or low-code solution to help you get started. As long as you keep it separate from your main app and have it communicate with your main app over private APIs, you should be good to go.
Aikido is an all-in-one application security tool. Want to see if your app is secure? Start scanning for free.







Top comments (0)