Originally published on the krypt.co blog
No I don't mean crypto-currency. What I'm really talking about is Universal 2nd Factor (U2F). U2F is a protocol for doing two-factor authentication that constructively prevents phishing on the web.
How does phishing work?
It's very simple -- an attacker gets you to click on a fake link like http://facebo0k.com or http://dropobox.com, and the page looks exactly like the real thing.
Next, the attacker's site asks for your username + password. And you enter it. Because it looks legitimate and you're just trying to browse the web like you do everyday. You might think you'll never click on a suspicious link, but what if it comes from a trusted source? Like a compromised facebook or email account of one of your friends?
When you click enter, you will send your username + password to your attacker and it's game over!
I already use two-factor -- I'm invincible!
I've talked to a bunch of folks about this, and the gut reaction is often "I use two-factor so I can't be phished!" This is actually very wrong, two-factor is just as easy to phish as a username and password -- especially since people are now even more used to entering 2FA codes all the time.
After asking for your username + password, the attacker will simply show you another dialogue to get your two-factor code. It's true that the attacker has minimal time to use the 2nd factor code as it expires quickly, but this can all be automated.
Even push-to-approve 2FA like Duo or Google Prompt can be phished
An attacker doesn't need you to enter a code to phish you. They just need to convince you to hit approve on a Duo or Google Prompt style push notification, and you will tap approve because you think you are logging into the real site and you've been trained to do this. Once you tap approve, you will sign the attacker in to your account on their session.
U2F Stops Phishing with Crypto
Universal 2nd Factor (U2F) uses public-key cryptography to prevent phishing, automatically. Many sites you use today already support it like: Facebook, Google, Dropbox, Salesforce, Stripe, GitHub, GitLab, and more.
There are many different forms of phishing and some are very hard to prevent. However -- credential phishing is something we absolutely can prevent using cryptography. The trick is that the "credential" becomes cryptographically bound to the website that you're actually on.
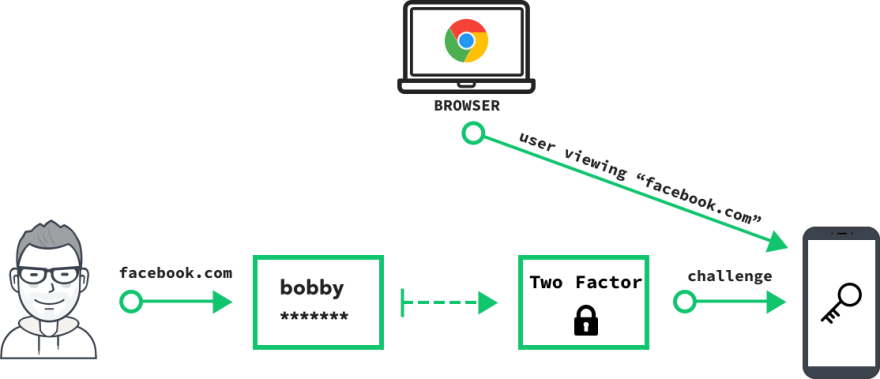
There are two steps to U2F:
- Registration Generate a new key pair on an authenticator. Register the public key with a website, say facebook.com.
-
Authentication
- The website's server sends a random
challengetoken. - The browser tells the authenticator the domain that the user is viewing
- Using the private key, the authenticator creates a digital signature of both the
challengeand, most importantly, the domain of the website that you are actually on -- this comes directly, and securely from the browser itself.
- The website's server sends a random
The phishing protection is built in -- the credential that the authenticator spits out is only useful for the owner of the website. A signature for "facebook.com" cannot be used on "google.com". Likewise, a signature for "facebo0k.com" cannot be used on "facebook.com".
Even if the attacker tricked you into producing a signature for their fake website http://facebo0k.com -- this signature would be useless to them! The real facebook.com would never accept a signature that contains an invalid domain.
That's the point of U2F -- it makes the domain you've visited a part of the cryptographic credential you need to login.
How do I get started?
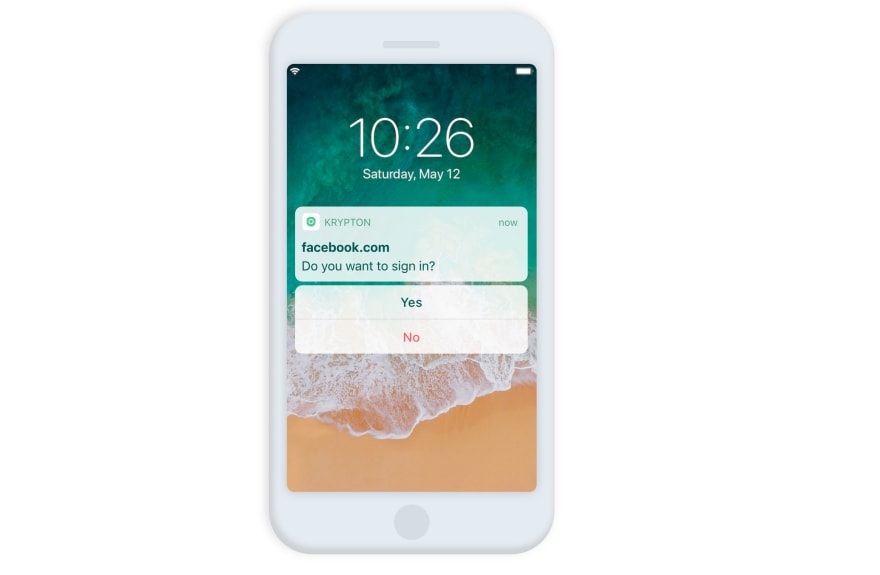
The first step is to get an authenticator. There are several options. We built Krypton to make it easy for anyone to get become un-phishable on the web. Krypton works on the device you already have -- your phone.
Install the Krypton Authenticator
Other options
If you don't want to use your phone, you can buy a standalone USB device. I recommend this wonderful guide for comparing different standalone U2F keys.






Top comments (2)
Doesn't seem like crypto is necessary here.
If the computer(browser) is trusted, then it can just send the domain to the 2FA device, and the 2FA can use the domain to see which key to use from the table of your registered keys (without actually using the domain as part of the crypto)
If the computer(browser) is compromised, then it can just send the real domain while giving your response to the bad guys.
When is using the domain as part of the crypto give an advantage over validating and discarding the domain?
While what you wrote is true, there are advantages for this being part of the cryptographic protocol. Namely with TOTP 6-digit codes the user can shoot themselves in the foot by giving away the code to some site or somebody (think of it like "oh the auto-2fa isn't working, I should just punch in the code). Of course you could hide the code from the user. There is also some complexity about which sites should be allowed to use the 2FA code (i.e. accounts.google.com vs my.google.com) and the U2F protocol outlines how this all works.
If the browser is compromised then the user is totally compromised anyways (steal the sessions after you login).