tl;dr
dotenv-vault is a simple dotenv management tool, keeping tokens secret.
 acro5piano
/
dotenv-vault
acro5piano
/
dotenv-vault
[deprecated] simple dotenv encrypt & decrypt tool inspired by yaml_vault
Use git-crypt https://github.com/AGWA/git-crypt
No more maintained. Use other tools.
dotenv-vault
simple dotenv encrypt tool inspired by yaml_vault
Default cipher is aes-256-cbc. Default sign digest is SHA256.
Install
For MacOS:
git clone https://github.com/acro5piano/dotenv-vault ~/.dotenv-vault
ln -sfnv ~/.dotenv-vault/bin/dotenv-vault /usr/local/bin/dotenv-vault
For Linux:
git clone https://github.com/acro5piano/dotenv-vault ~/.dotenv-vault
sudo ln -sfnv ~/.dotenv-vault/bin/dotenv-vault /usr/bin/dotenv-vault
Requirements
dotenv-vault requires the following:
- Bash >= 2
- Openssl >= 2
- Perl >= 5
Almost all machine does not need any additional installation process.
Usage
Encrypt
Input file (.env):
NODE_ENV=development
API_KEY=123456789
Command:
$ dotenv-vault -e API_KEY -k foobarbaz encrypt .env
where -e specify the key you encrypt.
Output:
NODE_ENV=development
API_KEY=U2FsdGVkX186T6zdupR27pXHO0Hdnz9rqZfVdgqBEqk=
Decrypt
Input file (.env.encrypted):
NODE_ENV=development
API_KEY=U2FsdGVkX186T6zdupR27pXHO0Hdnz9rqZfVdgqBEqk=
Command:
$ dotenv-vault -e API_KEY -k foobarbaz decrypt .env
Output:
NODE_ENV=development
API_KEY=123456789
Create Encrypt env
dotenv-vault create command is convenient to create new entry:
$ bin/dotenv-vault -k foobarbaz create 'SOME_KEY=123456'
# => SOME_KEY=U2FsdGVkX18tEclKImEV30HSG0b7IOu3dyO3MpceCd4=
You can paste or redirect to register new entry like this:
$ bin/dotenv-vaultWhy
How do you manage .env file in your repository?
The file may contain some secret tokens. In OSS, those information must not open. Even in private repository, we shouldn't include secret information into Git repository, because a lot of stakeholder including out-source developers will commit the code.
However, secret information is needed in applications so we may want to include them to the repository.
According to this article, major option is to use KMS, Key Management Service. Major cloud service such as AWS and GCP provide the service.
https://www.reddit.com/r/devops/comments/52pl5c/how_do_you_manage_env_dotenv_files/
However, I would like to manage them more simple way without any plugins and dependencies.
Options
yaml_vault is a good tool to keep YAML files secret.
 joker1007
/
yaml_vault
joker1007
/
yaml_vault
Yaml file encryption/decryption helper.
YamlVault
Yaml file encryption/decryption helper.
Breaking Change from 0.x to 1.0
- Output YAML file keeps alias & anchor syntax & tag info. (But empty line is trimmed)
-
--keyformat is changed. (Need$as root document at first) -
--keysupports new formats. (Root Doc, Wildcard, Regexp, Quote)
Encryption Algorithm
yaml_vault uses ActiveSupport::MessageEncryptor.
Default cipher is aes-256-cbc
Default sign digest is SHA256.
Installation
Add this line to your application's Gemfile:
gem 'yaml_vault'
And then execute:
$ bundle
Or install it yourself as:
$ gem install yaml_vault
Usage
Encrypt
# secrets.yml
default: &default
hoge: fuga
aaa: true
bbb: 2
foo: bar
complicated:
- 1
- ["hoge", "fuga"]
- [{key1: val1, key2: val2}, {key3: val3}]
- a:
b:
c: d
e: !ruby/range 1..10
test:
<<: *default
hoge:
- 1
- 2
- 3
vault:
secret_data: …It is written in Ruby. Ruby on Rails use YAML file for configurations. So the tool is popular with Ruby on Rails applications.
Rails 5.2 has the similar function by default. If we run the following command, the file is decrypted and our editor will run. The file encrypted again after editing the file.
bin/rails credentials:edit
However, my project does not use neither Ruby on Rails nor YAML. Just .env and .env.local, .env.production files exists.
So I created dotenv-vault (apparently inspired by yaml_vault).
Philosophy
- Less dependency. This is convenient if we run in CI.
- Simple. Easy setup and no DSL, zero learning cost.
- Productive. Automate as possible.
Less dependency is really important because we could use this tool in any environments, any projects, with zero cost. Currently dotenv-vault depends on the three:
- Bash
- Openssl
- Perl
I chose Perl to parse dotenv file because Perl does not change command syntax between operating systems. sed differs between BSD and GNU.
Major OS, such as macOS and Ubuntu, have Perl by default.
How to use
Manually
After install (check out the repo), add # encrypt-me comment at the end of line to be encrypted:
# .env
APP_ENV=production
APP_KEY=super_secret_value # encrypt-me
Then run the following command:
$ dotenv-vault encrypt .env
You may be asked the password to encrypt, input it and press return:
Please input password and press Return:
It will output encrypted file as standard output like this:
APP_ENV=production
APP_KEY=U2FsdGVkX19VF+rLm7ypGQFl76Sq7QUEaU5uM+AlQmRxcKMTTj63R81K4U0WYZzy # decrypt-me
So you can redirect the output to a file:
$ dotenv-vault encrypt .env > .env.production
To decrypt the file, run:
$ dotenv-vault decrypt .env.production
Then input the password and decrypted output will be shown.
In CI
In CI, we cannot input the password manually, so set DOTENV_PASSWORD environment variable in your CI service.
$ env DOTENV_PASSWORD=foo dotenv-vault decrypt .env.production > .env
(Actually env DOTENV_PASSWORD=foo is not needed)
Add tokens
It is not convenient if we should decrypt & encrypt every time we add new token.
dotenv-vault generate simply generate encrypted token.
$ dotenv-vault generate 'FIREBASE_TOKEN=new_secret_token'
The command output will be like this:
FIREBASE_TOKEN=U2FsdGVkX19NWIIPCamKJOFdJktBSETdFNV6BIwBlkjBNhCRQ18z2zDtVRu3fO79 # decrypt-me
So we can redirect the output to add new token.
$ dotenv-vault generate 'FIREBASE_TOKEN=new_secret_token' >> .env.production
Thanks
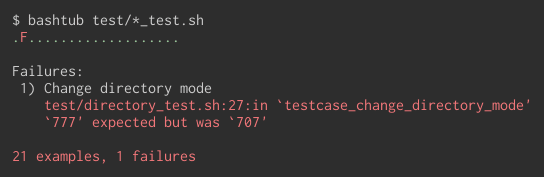
I use Bashtub to run unit test for bash script. Bashtub is really simple and good tool.
Bashtub 🛁 - Unit test framework for Bash
Bashtub is a tiny unit test framework for Bash You can specify the test caes as as assertion-based test cases likes xUnit Bashtub colorfully outputs the results of the test When test passed
and when tests failed, it bashtub outputs the information of the failures,
Requirements
- Bash 3.2+
Installation
curl -o ~/bin/bashtub https://raw.githubusercontent.com/ueokande/bashtub/v0.2/bin/bashtub
chmod +x ~/bin/bashtub
where the path ~/bin must be included in $PATH.
Then test to run the bashtub.
bashtub # output 0 examples
Writing tests
Test cases are declared in the function that start with testcase_.
Bashtub automatically finds the testcase in the loaded file.
The tests are written as assertion-based test cases likes xUnit.
Minimal test
The first, simple example is the following :
# examples/first_test_case.sh
lorem_ipsum='lorem ipsum dolor sit amet'
testcase_first_word() {
first_word=$(echo $lorem_ipsum | cut -f1…Conclusion
In my use case, dotenv-vault provides useful features. If you have any opinions, please let me know!
Thanks.



Top comments (4)
Hey! Just wanted to share that if you use this syntax
{% github https://github.com/acro5piano/dotenv-vaultwe can see a preview of your repo/readme %}!simple dotenv encrypt & decrypt tool inspired by yaml_vault
dotenv-vault
simple dotenv encrypt tool inspired by yaml_vault
Default cipher is aes-256-cbc. Default sign digest is SHA256.
Install
For MacOS:
For Linux:
Requirements
dotenv-vault requires the following:
Almost all machine does not need any installation process.
Usage
Encrypt
Input file (.env):
where
# encrypt-meis the mark of the line dotenv-vault encrypt.Command:
Output:
# decrypt-mewill be used when decrypt the file.Decrypt
Input file (.env.encrypted):
# decrypt-meis the mark of the line dotenv-vault decrypt.Command:
Output:
Create Encrypt env
…dotenv-vault createcommand is convenient to create new entry:Thanks! Great feature.
Another useful tool - github.com/dotenv-linter/dotenv-li....
It’s a lightning-fast linter for .env files. Written in Rust.
Also check out github.com/dotenv-org/dotenv-vault - from the same people that helped pioneer .env files.