Introduction
Marking attendance is a regular activity in schools & colleges. It is
done anytime during the length of class depending on the instructors. Some prefer to do it before starting the class, while others prefer doing it after the class. Others may even do this activity in between the class. Overall, the focus here is that this is an activity which is done repeatedly, regularly and thus, wastes precious teaching time of the instructor. If done in between the class duration, this breaks
the flow of the class and often causes the peers to lose in the subject/topic being currently taught by the instructor. We aim to solve this problem by providing an Automated Attendance System Using Face Recognition.
Key Challenges
- Reduce attendance time - If we can create an attendance management system in which the time required to take the attendance is less as compared to other attendance management systems. Then educational institutions will prefer our attendance management system as it will save the attendance time in the class which will be productive as it can be utilized more effectively.
- Reduce Hassle - There is effort from the teacher and more workload to manage and maintain the attendance of the students of the class.
- Improve Accuracy - The existing models of attendance management system generally has low frequency due to certain factors involved in different management systems.
- Increase ROI
- Enhance Security - There is a security issue in some of the existing attendance management systems. If a system can designed with role based access and zero manipulation of the attendance data of the students. Then it will be a better solution
Proposed Solution
- When a student enters the class, his/her photo is captured(using a video frame).
- We pass this image through our model and find out the dataset entry which is most similar(above a particular threshold).
- The user is given a prompt to verify the name predicted by the model.
- If user replies “no”, steps 1,2,3 are repeated.
- Else, the details of the student along with the time of entry is written into a db.
- Same procedure applies when students exit.
- Attendance is marked for students who attend the class for the entire duration.
- The teachers are given an option to manually override the attendance marked by the system.
- After the teacher confirms the shown attendance, it is uploaded to the database.
Design & Methodology
Dataset Used
We started creating out own dataset of 10-12 images per person.
This we did with the help of out friends.
Next up, to increase the amount of training data, we tried the concept
of image augmentation. In this technique, new images are generated from already
existing image using the following kinds of transformations :
❖ Horizontal and Vertical Shift Augmentation
❖ Horizontal and Vertical Flip Augmentation
❖ Random Rotation Augmentation
❖ Random Brightness Augmentation
❖ Random Zoom Augmentation
NN Architecture
Inception net, broadly, allows the internal layers to pick a suitable
filter which will prove relevant for the image. This has a huge impact as it leads to the network giving good outputs for various image sizes.
When testing on Cifar 10 dataset, this model gives 80% + accuracy on
the test set without any parameter optimisation. Thus, this is one of the most important models for Image Analysis.

Process
Data Collection
- Collect the images for each student. We keep these images in folder corresponding to each student. The folder name is according to the "_id" field corresponding to the student in the mongodb database.
- We can now use the folder name as a label for training the model on this student's data.
- A model is created for each class consisting of some students. This model is generated once and saved for predictions later on
Generating the Model
- Get the list of students for a class
- Go through each of the image folders corresponding to each of the students
- For each image, class label is the parent folder name.
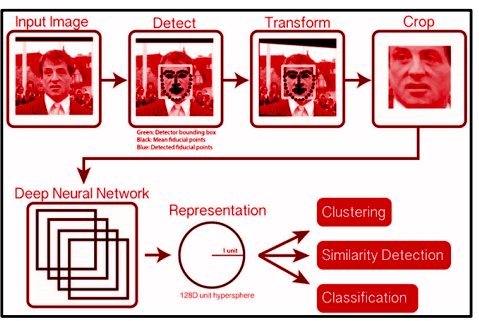
- Run a face detection algorithm on the face and detect the presence of a face
- If a face is detected, get the bounding box coordinates
- Using the bounding box coordinates, crop the image so that you have image only of a face.
- Detect the orientation of face using Dlib, and apply transforms to make the eyes, mouth & other facial features aligned at a certain level. This ensures good quality input to the neural network.
- Pass the aligned image through the neural network. The net generates 128 embeddings (or mesaurements) of each face
- This is now the data (or features) extracted from the image. Use this embeddings vector to train a classifier.(See our trials with different classifiers)
- At the end, the classifier is dumped & saved as a object, this can be loaded anytime from the database & used for predictions.
Face Recognition Pipeline
- Load the classifier from the database. Database query is done using the class for which attendance is being marked.
- For each frame do the next steps
- Run a face detection algorithm on the face and detect the presence of a face
- If a face is detected, get the bounding box coordinates
- Using the bounding box coordinates, crop the image so that you have image only of a face.
- Detect the orientation of face using Dlib, and apply transforms to make the eyes, mouth & other facial features aligned at a certain level. This ensures good quality input to the neural network.
- Pass the aligned image through the neural network. The net generates 128 embeddings (or measurements) of each face
- This is now the data (or features) extracted from the image.
- This is now passed to the classifier to detect the correct class label.
- Once we have all class labels from a video file, we can determine which students were present in the class.
References
[1] Freya. J. Vora, Pooja. L. Yadav, Rhea. P. Rai, Nikita. M. Yadav “Android Based Mobile Attendance System”, International Journal of Advanced Research in Computer Science and Software Engineering, pp 1-2, Volume 6, Issue 2,
February 2016.
[2] Subhadeep Dey, Sujit Barman, Ramesh K. Bhukya, Rohan K. Das, Haris BC, S. R. M. Prasanna and R. Sinha, “Speech Biometric Based Attendance System”, Communications (NCC), 2014 Twentieth National Conference, pp 2-3, February 2014.
[3] Prof.A.D.Sawant, Arti Dongare, Ichha Gilbile, Amit Singh Thakur,
PoojaTekawade. “A Survey on Smart Attendance System Based on Various
Technologies”, International Journal of Innovative Research in Computer and Communication Engineering, pp 5-7, Vol. 5, Issue 10, October 2017.
[4] Sanjay Badhe, Kunal Chaudhari, Sneha Kale, Tejaswi Mane, “Smart
Attendance Management System”, International Journal of Computer
Applications. pp 4-6, 2016.
[5] Zhang, Xiao zheng, and Yong sheng Gao, "Face recognition across pose: A review." Pattern Recognition42.11 (2009): 2876-2896
[6] Lacey et al, “A Longitudinal Study of AutomaticFace Recognition‖”, IEEE ICB, 2015, pp: 1- 8
[7] Ms. Snehal Houshiram Gorde1, et al, “A Review on Face Recognition
Algorithms”, Volume III, Issue I Issn No.:2350-1146, I.F-2.71
[8] C. Szegedy et al., "Going deeper with convolutions", Proc. IEEE Conf. Comput. Vis. Pattern Recognit., pp. 1-9, Jun. 2015.




Top comments (5)
OR instead of creating a dystopian mass-surveillance tool, teachers could count on students to attend responsibly because after all they are adults in charge of their own destiny.
Though it's definitely interesting technically speaking.
I think this is aimed at children, who are far from responsible adults, which makes the ethical questions even more prominent, in my opinion.
Yet another example of how Computer Science still doesn’t have a strong idea of ethics surrounding the discipline.
"Now I am become death, the destroyer of worlds."
This is excellent, thank you! Rather than focus on the potential misuses (c'mon, this is humanity, by experience we know someone either will or already has -- maybe not openly -- weaponized everything including farts most likely), we need operational stuff like this for more potential good, as well as having working examples to study in order to incorporate either defenses or mitigations. Like AI consensus for example.
Nice job!