What is DevSecOps?
DevOps is now the default approach to agile software development and deployment in most tech companies. With the promise of speed and quality, it seamlessly integrates the functions of development and operations teams to ensure that applications can be continuously pushed out to production. However, the emphasis on speed often comes at the cost of security. Critical vulnerabilities are addressed only late in development, with security patches often being tacked on right before deployment. This is where DevSecOps, also known as Secure DevOps, comes in.
Simply put, DevSecOps is the future of DevOps. DevSecOps involves integrating application security testing earlier in the software development lifecycle (SDLC). This notion of shifting security to the left is commonly called "shift left."
Top 11 DevSecOps Tools
Here are the top 11 DevSecOps tools (in no particular order) that can help you as you make the transition to a more secure approach to agile development.
1. Prisma Cloud by PaloAlto
Prisma Cloud focuses on cloud native security and compliance. It allows you to scan and secure applications and infrastructure in the CI/CD pipeline across hybrid and multi-cloud environments. By monitoring suspicious user behavior, exposed secrets, faulty configurations, and network threats, Prisma Cloud helps you quickly secure your cloud resources early in development.
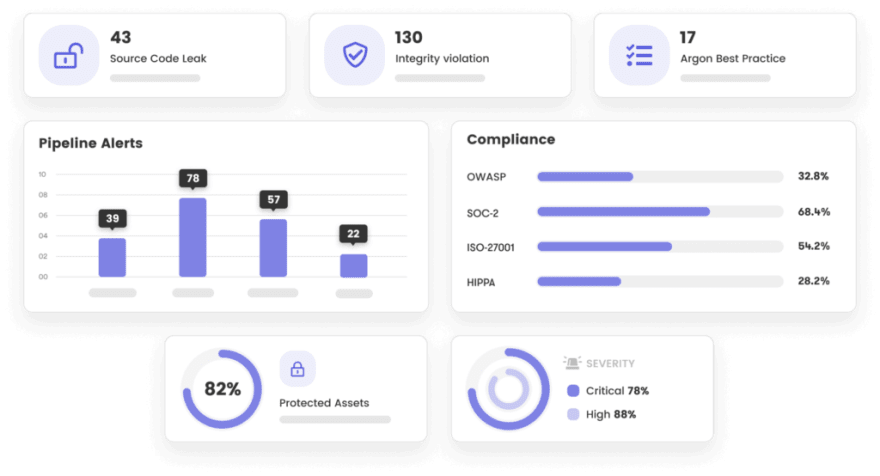
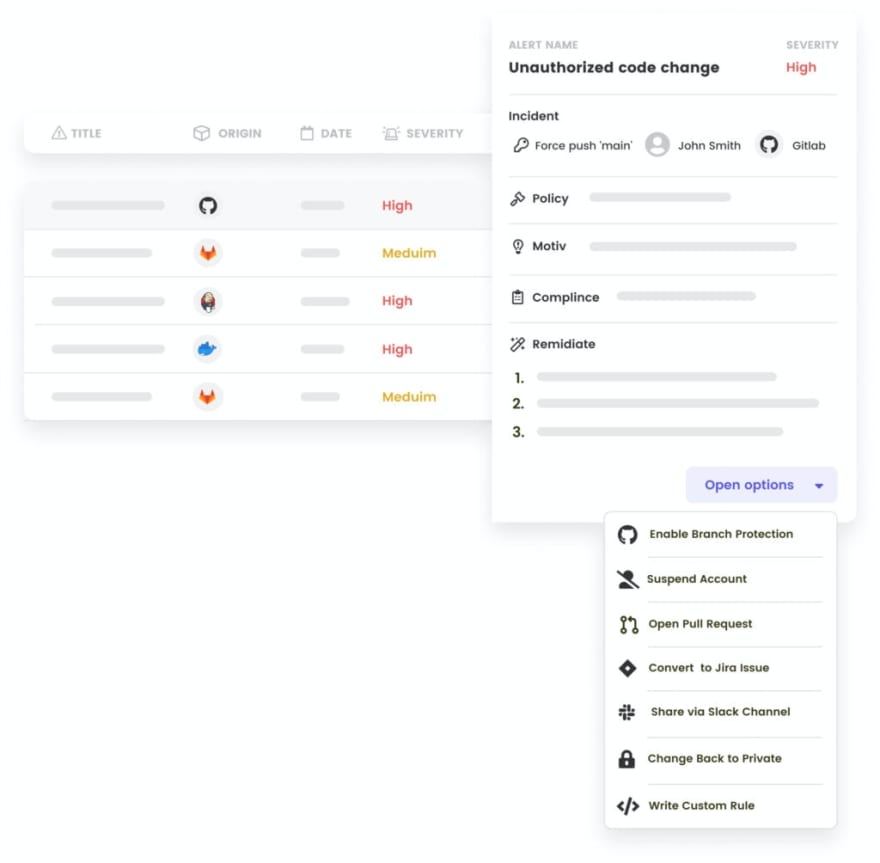
2. Argon Security
Argon Security provides holistic security solutions across your CI/CD pipeline, and positions itself as the first unified security solution that protects your software throughout the DevOps software supply chain. It exemplifies DevSecOps in that it ensures end-to-end security for your software supply chain's CI/CD pipeline without compromising on speed and output.
Argon provides you complete visibility on all assets, tools, activities, and users across the pipeline and also identifies misconfigurations, suspicious behavior, exposed credentials, and code leaks. Argon goes one step further and also automates the remediation of vulnerabilities based on compliance regulations and CI/CD security best practices, taking the burden off teams to manually intervene and address alerts.
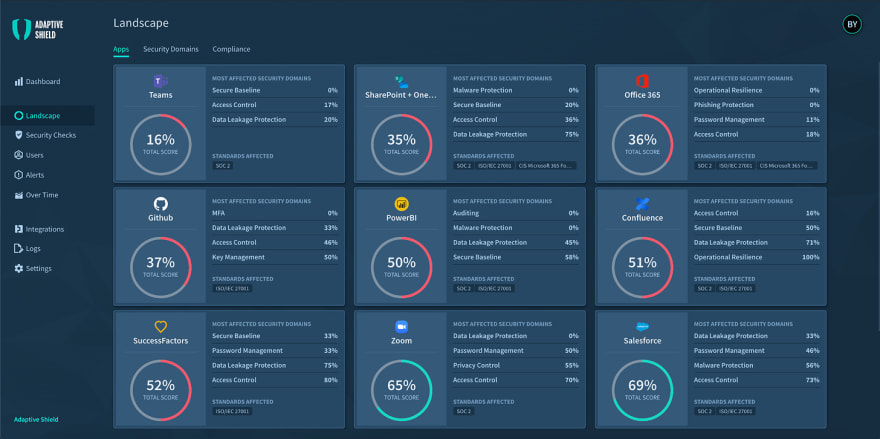
3. Adaptive Shield
Adaptive Shield's specialty is security posture management for Software as a Service (SaaS) platforms. It proactively spots and fixes security threats in all your SaaS applications, while managing user permissions, and scanning for accidental exposures and misconfigurations.
4. DoControl
DoControl is a SaaS-oriented security tool that addresses user access privileges, profiling and managing data exposure. DoControl gives you visibility on all your assets, users, and external collaborators. By automating data access controls, it enables security without compromising efficiency.
5.Checkmarx
Application Security (AppSec) is the forte of Checkmarx, which is an award-winning AppSec Testing tool that integrates security policies into the DevOps workflow and ensures security across the application lifecycle. Checkmarx scans all your code and provides actionable insights for critical vulnerabilities. Checkmarx also offers developer-friendly AppSec training that makes the transition to DevSecOps more efficient.
6. Snyk
Snyk is a developer-friendly security platform that sees developers as the first step in building secure applications and infrastructure. Snyk scans and secures components across the cloud native application stack through automated fixes, suggestions for preventive measures, and constant monitoring for vulnerabilities.
7. Reflectiz
Reflectiz targets online businesses who are looking to secure their financial websites against advanced third-party attacks. Reflectiz gives businesses insight into the third-party applications running on their websites as well as the security practices and behaviors of these third-parties. Once a complete assessment has been made, the tool suggests measures for mitigating security threats from third-party applications.
8. Orca Security
Orca Security offers timely detection of cloud security risks across AWS, Azure, and GCP, with prioritization of alerts that require more immediate attention. Its interface is easy to understand, allowing any team member to access actionable insights, in turn, making remediation faster.
9. Qualys
Qualys describes itself as a cloud platform and accompanying cloud agent that gives you a single platform for your IT, security, and compliance solutions. Its free Global AssetView app gives you instant visibility on all your known and unknown assets across your hybrid cloud environment. Several other apps integrated into its cloud platform allow you to analyze threats and misconfigurations, prioritize the most urgent vulnerabilities, and patch these risks with just a single click.
10. Tenable
The "cyber exposure company", Tenable, offers an independent assessment of weaknesses in your attack surface across your domains. Tenable not only provides visibility into exposures and the effectiveness of your current security practices, but it also predicts potential threats and generates actions to mitigate current and future risks. Tenable has a range of products covering security assessments for VMs, cloud platforms, containers, web applications, and IT/OT infrastructure.
11. SpectralOps
SpectralOps promises speed in securing code and cloud resources. Targeting developers, SpectralOps enables you to shift left without compromising efficiency by automating the protection of secrets at build time. It assures minimal noise as it scans for exposed tokens, credentials, and API keys as well as risky misconfigurations, and makes it easier for developers to integrate their own detectors and mitigation policies across the pipeline.
Recommendation & Next Steps
This is by no means an exhaustive list of tools that can help you shift left to a culture of DevSecOps. Based on your enterprise's needs and development workflow, you can pick and choose the tools that best suit your approach and culture. Security training for developers is often a crucial aspect of the shift to the left, but this transition can be seamless if you select tools that can be easily mastered and integrated into your pipeline without compromising on speed and efficiency.attacks](https://www.firstpoint-mg.com/cellular-iot-cybersecurity/) and being able to mitigate them should be part of a security strategy when it comes to mission-critical private cellular networks.













Oldest comments (0)