The Endpoint security policies are designed to help you focus on the security of your devices and mitigate risk. The available tasks can help you identify at-risk devices, remediate those devices, and restore them to a compliant or more secure state.
Now to understand endpoint security let's first register s device in our Azure AD, To do that first we will create a VM and will connect it to our Azure AD.
Once logged in to our VM we will go to sesstings> accounts> and will click on login in office or school account.
In the next step, we will put our work credential and it will our device to Azure AD.
We can find our device in Azure AD> device

Now let's Manage Antivirus In Microsoft Azure Endpoint Manager admin center.
Go to https://endpoint.microsoft.com/ and now go to Endpoint Security>Antivirus

Now we will create an Antivirus Policy. To do that click on create a new AV policy.

We can closing monitor devices in AV reports and can manually look into unhealthy devices.
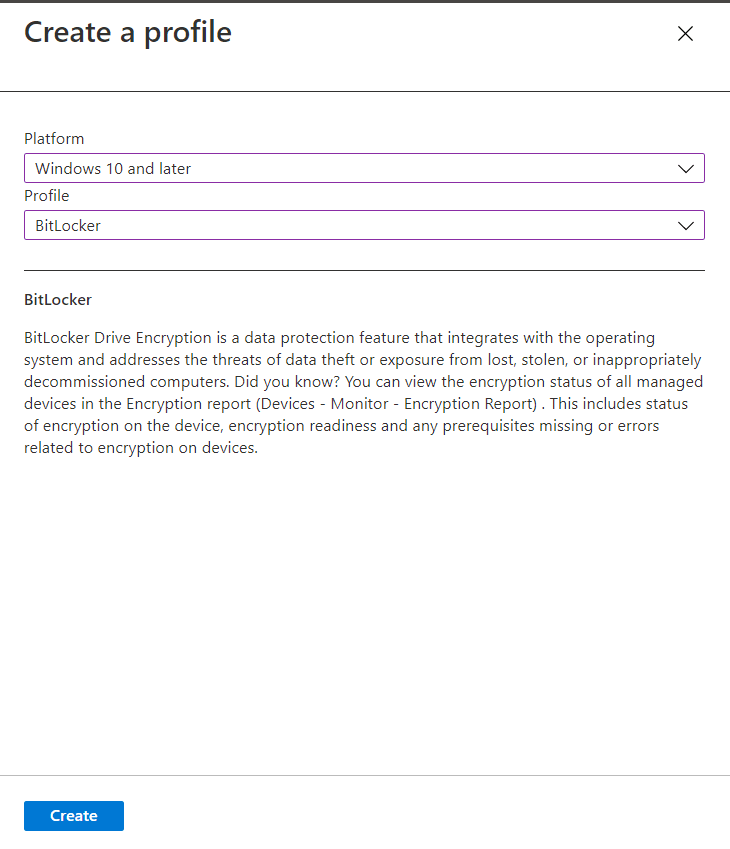
Let's now implement a disk encryption policy for window 10 and above. We can use BitLocker for encryption.
BitLocker Drive Encryption is a data protection feature that integrates with the operating system and addresses the threats of data theft or exposure from lost, stolen, or inappropriately decommissioned computers.
Next, let's talk about Endpoint detection and response. Microsoft Defender for Endpoint endpoint detection and response capabilities provide advanced attack detections that are near real-time and actionable. Security analysts can prioritize alerts effectively, gain visibility into the full scope of a breach, and take response actions to remediate threats.
To create an Endpoint detection and response policy we can go vo the Microsoft endpoint security admin panel and can create one from there.

When Defender antivirus is in use on your Windows 10 devices, you can use Intune endpoint security policies for Attack surface reduction to manage those settings for your devices.
Let's create a policy for App and browser isolation. We can do the same using the Microsoft Endpoint Manager admin center.

Account protection policies help protect user credentials by using technology such as Windows Hello for Business and Credential Guard.

In a similar, we can create device Compliance policies as well.
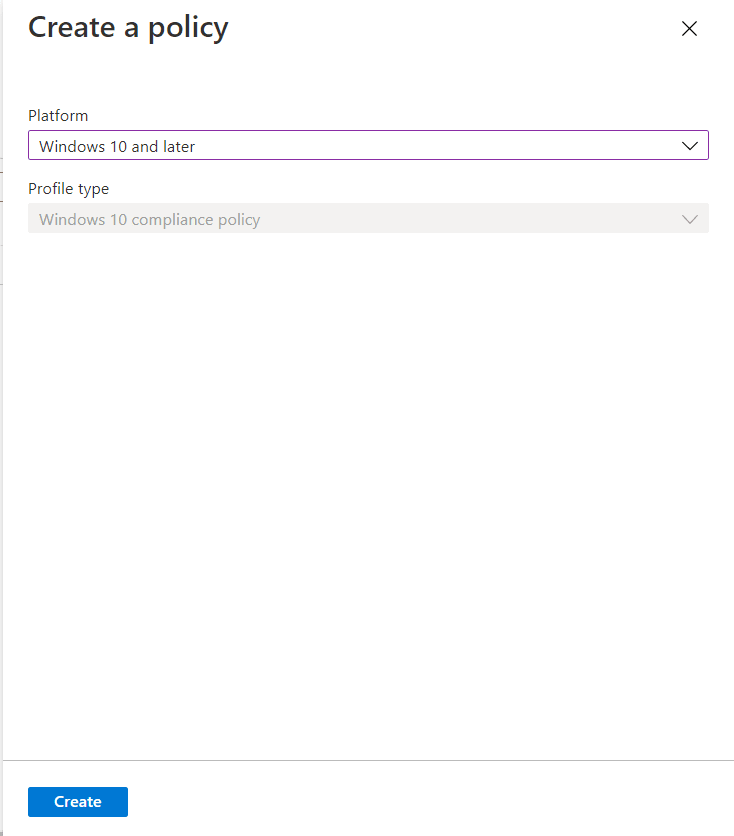
From Microsoft Endpoint Manager admin center Endpoint Analytics dashboard we can manage device which is incompatible with our Endpoint security policies.

Hope now you have an overview on Endpoint security policies. Follow me on twitter for more- https://twitter.com/stharvid







Top comments (0)